Do you look after any sort of social media content?
If so, especially if it’s business related, you’ve probably received your fair share of copyright infringement complaints.
No matter how scrupulous you are about correctly licensing and attributing your content, you may be the victim of a scurillous or over-zealous complainant.
For example, we went through a phase recently during which a spammer took to emailing us about images that we had licensed via Shutterstock, implying that we were using them illegally. (We were not.)
The spammer offered us specious conditions to help “regularise” our use of the image – complete with a thinly-disguised warning that “removing the image isn’t the solution since you have been using our image on your website for a while now.”
Sometimes, however, a complainant may be prepared to make an claim on the record by lodging a formal infringement complaint with the site where your content is hosted.
In such cases, you may indeed be contacted by the relevant social media company to try to sort the issue out.
Ignoring genuine complaints is not really an option, given that the social media site may decide to remove the offending material unilaterally, or even to lock you out of your account temporarily, if you don’t respond within a reasonable time.
As you can imagine, this creates an opening for cybercriminals to frighten you into responding by sending out a fake takedown message.
Fake infringement notice
Here’s how cybercriminals tried to use this attack against us today, starting with a short but simple email:
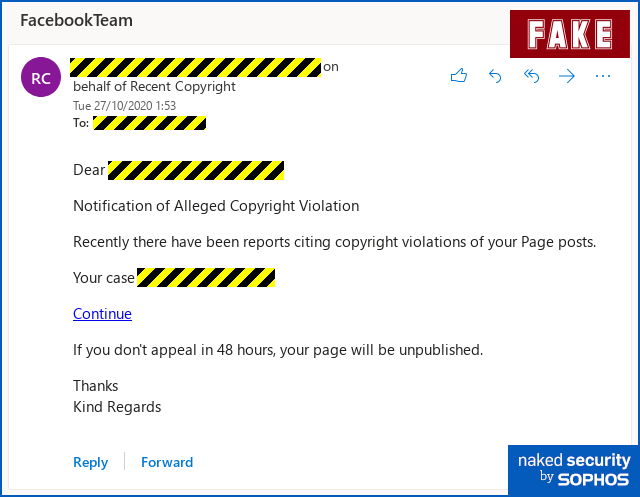
Notification of Alleged Copyright Violation Recently there have been reports citing copyright violations of your Page posts. Your case NNNNNNNNNNNNNN [Continue] If you don't appeal in 48 hours, your page will be unpublished. Thanks Kind Regards
The good news is that he English isn’t quite right, the email didn’t come from Facebook’s servers, and the email address of the sender is bogus.
In other words, you should be suspicious of this message right away and you shouldn’t click the link in it.
The bad news, however, given that many recipients might feel compelled to investigate further just in case, is that the link you’ll see when you hover over [Continue] does indeed take you to facebook.com.
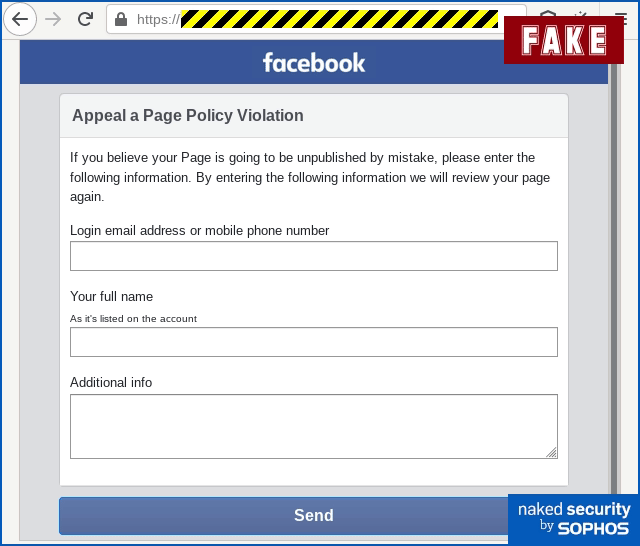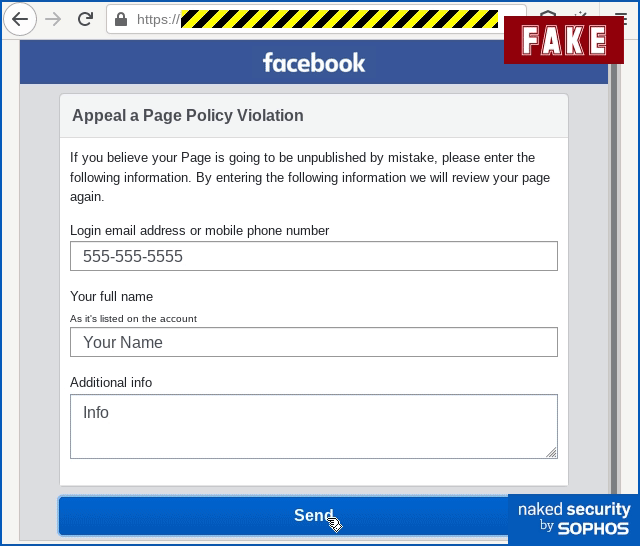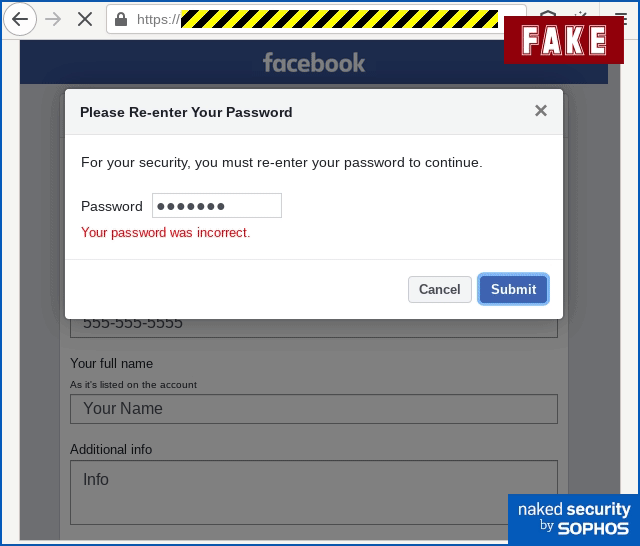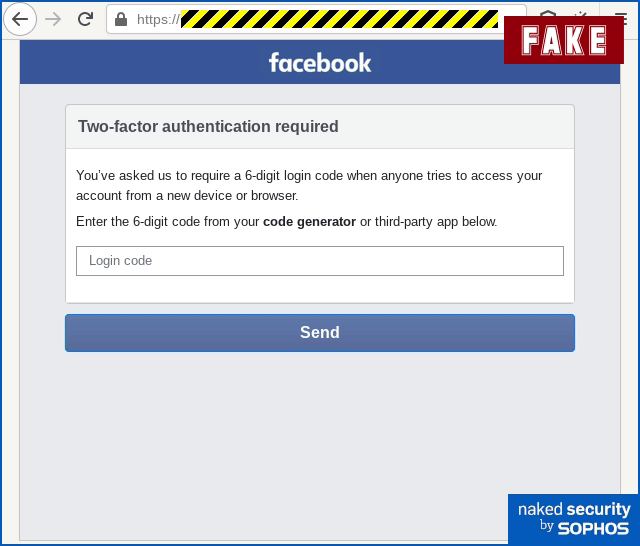
That’s because it’s a fraudulent account on Facebook itself that’s pretending to be an official Facebook landing page for copyright infringement notices:
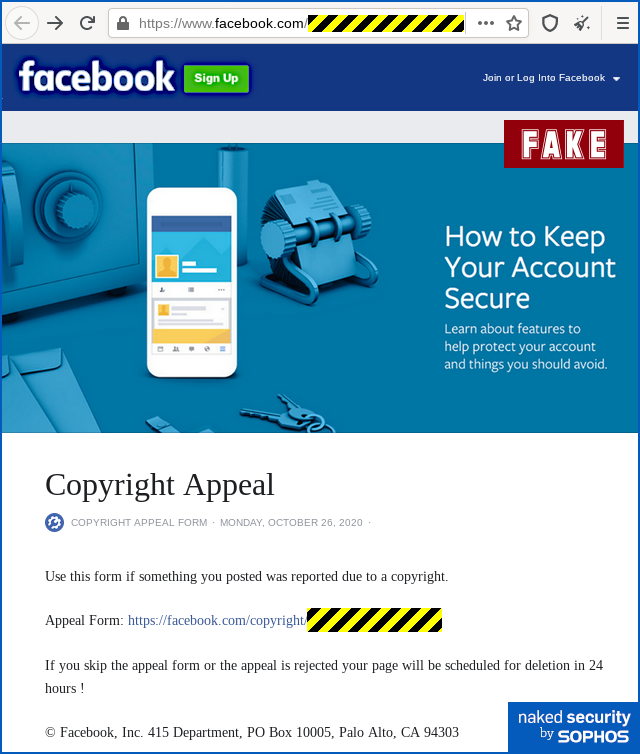
Use this form if something you posted was reported due to a copyright. Appeal Form: https://facebook.com/copyright/NNNNNNNNNNNNNNNNNNNNNNNNNN If you skip the appeal form or the appeal is rejected your page will be scheduled for deletion in 24 hours! (C) Facebook, Inc. 415 Department, PO Box 10005, Palo Alto, CA 94303
The link on the Facebook page above looks as though it stays on facebook.com, but the URL you see in blue above isn’t the URL you visit if you click it.
That’s an old trick used by crooks – and even by some legitimate sites.
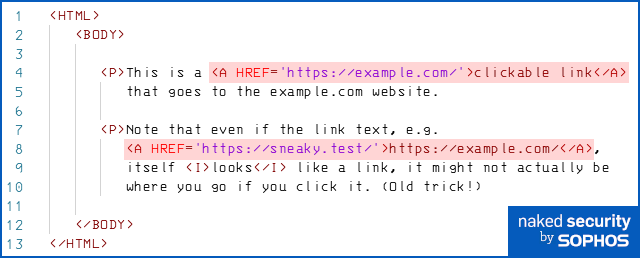
The text of a link isn’t where you end up if you click on it, because the actual target URL you visit is specified separately from the link text in HTML.
The text that is displayed as the clickable text in a web page is whatever appears between the tags (markers) <A> and </A> in the HTML source code.
But the link to which you actually navigate if you click on the link text, whether it looks like a URL or not, is specified by an HREF (hypertext reference) attribute in the HTML tag itself, as depicted below:
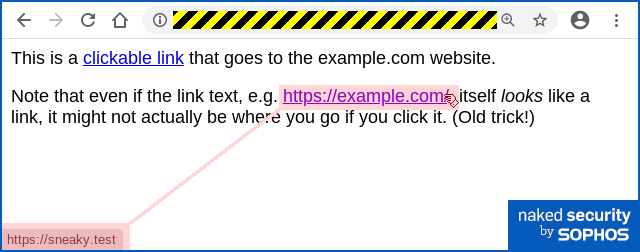
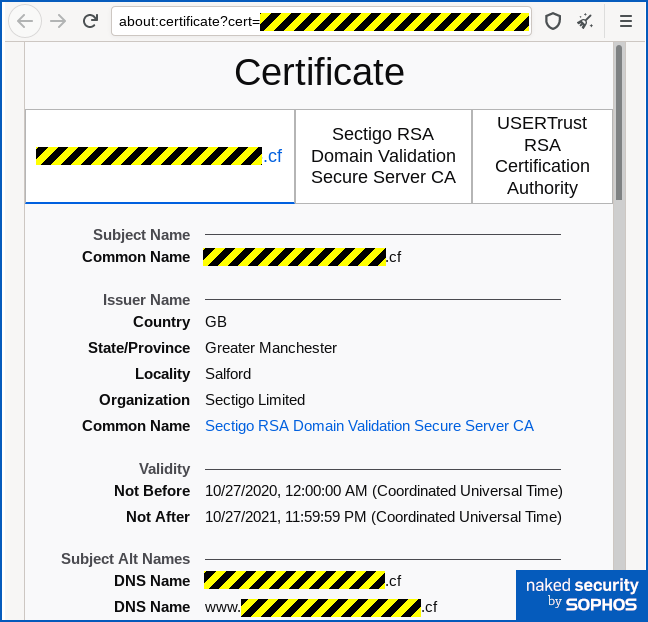
The link on the fraudulent Facebook page in this scam takes you off to an external site using a .CF domain.
The CF top-level domain belongs to the Central African Republic, one of many developing economies that gives away some domains for free in the hope of attracting users and selling cool-sounding domain names for $500 or more.
The domain name in this case was just a long string of digits – something that you don’t see often, but possibly selected here by the crooks in order to look like the numeric codes that Facebook uses in its own URLs to denote accounts.
As you can see, this phish tries to scam your your login name and your password, sneakily asking you to “re-enter” your password in a second step instead of simply demanding your username and password up front:
Interestingly, and ironically, the crooks have made the password entry form look like an additional security precaution, thus justifying the password prompt even if you are already authenticated to the real Facebook site.
The crooks also try to trick you into entering in the 2FA code from the Facebook app on your phone (it’s in Settings & Privacy > Code Generator), potentially giving them a one-shot chance to login as you directly from their server, even if you have 2FA enabled.
Of course, the address bar contains a bogus domain name that ought to dissuade you from filling in forms on this site, let alone your password and 2FA code.
However, the fake site does have HTTPS enabled because it’s a temporary website set up on a cloud web hosting service – the HTTPS certificate is automatically generated by the hosting service when the site is activated.
The certificate’s validity started at midnight today [2020-10-27T00:00:00Z], and the scam email we received arrived at 01:53 UTC, which is early evening on the West Coast of America, and late evening on the East Coast.
As you can see, cybercrooks move fast!
In the video above, you’ll notice that the 2FA prompt reappeared after a short delay. We’re assuming that the crooks actually tried logging in with the username-password-2FA “triplet” in the time that the Loading animation was visible, and failed. (We shortened that section of the video to save time; in real life, the delay was about 2.5 times longer than depicted above.)
What to do?
- Check the email sender. Annoyingly, different email clients use different addresses from the email headers to decide what to show you, but in this case, the deceit should have been obvious. Outlook showed an email address associated with the web hosting company that the crooks had used; Apple Mail showed an email address from CF domain registered by the crooks. In both cases it was obvious that Facebook did not sent the message.
- Check the address bar. Although this scam softens you up by leading you to a page on
facebook.comfirst, the password-stealing part of the attack depends on you failing to notice that you’re on an imposter site when the password and 2FA prompts appear. Don’t be in too much of a hurry! - Don’t assume that a page on Facebook is a Facebook page. Rememeber that the vast majority of pages on Facebook – all of which show
facebook.comdomain names in the address bar – are not official pages of the Facebook organisation itself. Anyone can put Facebook imagery into their own pages to give them a veneer of officialdom. - Report phishing scams like this to Facebook. We forwarded the offending email to
phish@fb.com, an email address Facebook introduced more than eight years ago, and that is still listed on its advice pages. We’re hoping that Facebook will quickly remove the offending account and therefore neutralise the first link in this attack. - Avoid login requests that you arrive at from an email link. If you reach a password or 2FA prompt after following links in an email, don’t login there. You should know how to reach the login page directly for any service you use, for example by using a bookmark you set up earlier or by referring to your password manager. (Password managers also help to stop you pasting the right data into the wrong site.)
- Use a web filter. A good anti-virus solution (Sophos Home is free for Windows and Mac) won’t just scan incoming content to stop bad stuff such as malware getting in, but will also check outbound web requests to stop good stuff such as passwords going to malicious sites.

Leave a Reply