David Mitchell, Senior Director of Email Product Management at Sophos, shares his top tips to optimize workplace email security.
How many work emails have you sent and received today? Despite the rise of workplace chat and instant messaging apps, for many of us email continues to dominate business communications both internally and externally.
Unfortunately, email is also the most common entry point for cyberattacks – sneaking malware and exploits into the network, and credentials and sensitive data out.
Email security threats: the new and the enduring
The latest data from SophosLabs shows that in September 2020, 97% of the malicious spam caught by our spam traps were phishing emails, hunting for credentials or other information.
The remaining 3% was a mixed bag of messages carrying links to malicious websites or with booby-trapped attachments, variously hoping to install backdoors, remote access trojans (RATs), information stealer or exploits or to download other malicious files.
Phishing remains a frighteningly effective tactic for attackers, regardless of the final objective.
This is in part because the operators behind them continue to refine their skills and enhance the sophistication of their campaigns.
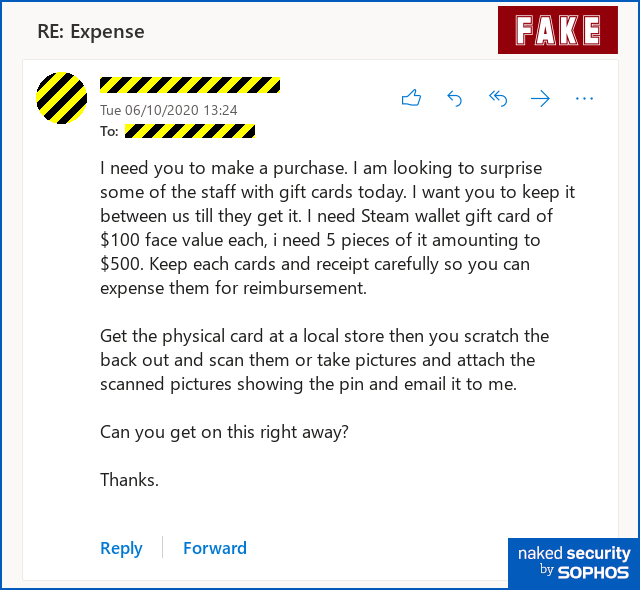
A good example is the rise of Business Email Compromise (BEC). No longer confined to poorly spelled or formatted messages pretending to come from the CEO and demanding the immediate and confidential transfer of significant funds, the latest iterations are subtler and smarter.
The attackers are doing their groundwork before launching the attack. They get to know the business and the target executives, adopting their language style and tone, and sometimes even actual email accounts.
The absence of malicious links or attachments in such emails make them difficult to detect with traditional security tools.
Attackers have also learned to better mimic web domains and take full advantage of the fact that one in three business emails is now opened on mobile devices.
It is harder to check the source and integrity of a message on a smartphone, and people are more likely to be on the move or distracted and therefore easier prey.
Five steps to secure your organization’s email
With these considerations in mind, here are our five essential steps to secure your organization’s email.
Step 1: Install an intelligent, multi-capability security solution that will screen, detect and block most of the bad stuff before it ever reaches you
To defend your network, data and employees against rapidly evolving email-based attacks your starting point must be effective security software. It is worth considering a cloud-based option that allows for real-time updates, scalability and integration with other security tools for shared intelligence.
To enable your security solution to perform at its best, you also need to set appropriate controls for inbound and outbound emails. For example, do you only scan emails upon receipt or monitor what users are clicking on after they’ve opened the email?
How do you quarantine unwanted emails or those that have failed authentication, and who has the authority to configure or overrule decisions?
This brings me to the second step.
Step 2: Implement robust measures for email authentication
Your organization must be able to verify that an email has come from the person and source it claims to come from. Phishing emails often have spoofed or disguised email addresses and email authentication offers vital protection against them.
Your email security solution should be able to check every incoming email against the authentication rules set by the domain the email appears to come from. The best way to do this is to implement one or more of the recognized standards for email authentication.
The main industry standards are:
- The Sender Policy Framework (SPF) – This is a Domain Name Server (DNS) record that checks the email address on inbound messages against pre-defined IP addresses that are allowed to send an email for a particular domain. If the inbound email address doesn’t match any of them, the address has likely been faked.
- DomainKeys Identified Mail (DKIM) – This looks into an inbound email to check nothing has been altered. If the email is legitimate, DKIM will find a digital signature linked to a specific domain name attached to the header of the email, and there will be a corresponding encryption key back at the source domain.
- Domain Message Authentication Reporting and Conformance(DMARC) – This instructs the receiving server not to accept an email if it fails DKIM or SPF checks. These checks can be performed individually, but DMARC combines them. It also ensures that a domain authenticated by SPF and DKIM matches the domain in the email header address. DMARC currently provides the best, most widely used approach for authenticating email senders.
Step 3: Educate employees on what to look out for
Alert employees who know the warning signs of suspicious emails are an awesome line of defense.
You can implement formal online training, share examples of the latest threats, run tests and show them some standard checks: does the email address look suspicious, are there unexpected language errors? If it appears to come from an internal colleague, would they normally communicate in this way etc.? Is the inbound email something you were expecting, from someone you know?
As mentioned earlier, some potential red flags are harder to spot when employees are opening the message on a mobile device. One way to address this is to introduce banners that highlight automatically when an email is of external origin even if it is pretending to come from an internal address.
Step 4: Educate employees on what to do when they find something
You need to make it easy for colleagues to report things they’re not sure of. This means providing them with a simple process, like an intranet mailbox for reporting suspicious messages.
The aim is to maximize the number of cases reported. It is never too late to stop further damage, so you should also encourage those who have fallen victim to an attack to come forward.
Step 5: Don’t forget about outbound email
Emails sent from your organization will themselves be assessed by recipients against the authentication methods listed above.
You need to ensure you have robust controls set against your own domain name. This is vital for the integrity of your organization’s communications and brand reputation and to prevent misuse by adversaries.
You may also wish to consider what else you need to monitor and control when it comes to outbound email.
Do you scan for anomalous activity or unusual behavior patterns (like emails sent regularly in the middle of the night to unverified IPs) that could indicate a compromised internal email account or active cyberattack, for example?
Do you scan for and block payment information like credit card details or other customer PPI from leaving the network, etc.?
These are sensitive areas that are as much about employee awareness and trust as they are about email security. The best place to start is by educating and supporting staff.
Email threats are evolving all the time as attackers take advantage of new technologies, new environments, or simply just hone their social engineering tactics. Review regularly your email security and make sure it’s keeping up with both changes in your organization and attacker techniques.
Three more suggestions …
If you’re looking at email security for your workplace, you may like to take a look at:
Sophos Intelix. This is a live threat lookup service that you can use in your own system software and scripts to add high-speed threat detection for suspicious websites, URLs and files. A simple HTTPS-based web API that replies in JSON means you can use Sophos Intelix from just about any programming or scripting language you like. (Registration is free, and you get a generous level of free submissions each month, after which you can pay-as-you-go if you want to do high volumes of queries.)
Sophos Phish Threat. This is a phishing simulator that lets you test out your staff in a sympathetic way, using realistic but artificial scams, so your users can make their mistakes when it’s you at the other end, rather than when it’s a cybercriminal. You can use it for free for 30 days (registration required).
Sophos Email. This is our cloud-based email security solution that blocks phishing imposters, spam, zero-day malware, and unwanted apps.

Cassandra
Is the basic technology of email passed its sell-by date?
Is there an opportunity for a consortium of ISP’s client, server and security software companies to develop a new technology that has more security (and privacy built in)? What sort of “mass” would be required to see this technology over-take email?
Is intelix the sort of technology that someone could build in to a Thunderbird add-in?
Paul Ducklin
You can use Intelix wherever you can make a TCP connection. send a web request over TLS, and get a reply. I wrote my own client in a few lines of Lua that I use to double-check the URLs and attachments that show up in scams I’m taking apart to write up for Naked Security. You can easily use a command line tool like cURL to do the lookups for you – in fact, we feature sample command lines for numerous curl requests in the Intelix documentation.
You do need to sign up for access credentials – for all the various types of request we support there’s a monthly allowance of free lookups, after which you can either pay a modest charge per request, or wait until your allowance ticks over into the next month.
For example, you get 5000 free URL lookups a month; thereafter they’re $1 for 5000. Same for file hash lookups to check on the reputation of a specific file. You can also upload 100 executable files a month for free to run in our sandbox and retreive a full behavioural analysis; thereafter it’s 40 cents a time.
HtH.
Steve
From the blurb about DMARC: “This instructs the receiving server not to accept an email if it fails DKIM and SPF checks.”
Should that actually say “This instructs the receiving server not to accept an email if it fails DKIM *OR* SPF checks.”?
Paul Ducklin
Fixed, thanks.