Ransomware attacker tactics have shifted – sometimes drastically – over the past ten months. In order to evade detection by increasingly effective endpoint security, nearly every attack involves a live engagement on the part of one or more attackers, who first surveil and inventory the target’s network and then focus their attention on shutting down or disabling various protective layers. These interactive sessions have become de rigeur in virtually all successful attacks against well-defended targets.
Over the same time period, the average ransom demand amounts also increased, and criminals expanded their attack portfolio to include the theft of highly sensitive information stolen from the target’s network, usually done at an early phase of the attack. This increases the chances a target would pay a ransom even if they have perfect backups and could restore from those backups immediately.
These two factors – the need to evade detection, and the need to strengthen the criminal’s hand in ransom negotiations – have been the dominant factors driving the most dramatic behavior changes, some of which we’ll discuss in this article. They also indicate the increasingly strenuous degree of effort it now requires to pull off a successful attack, a positive sign that the work defenders do has measurable effect on the attackers’ workloads.
What follows are an unscientifically chosen list of some of those escalations we found most interesting. We think these indicate a level of frustration on the part of the ransomware criminals at their inability to terminate or disable these security controls.
Unsafe Mode
In the fall of 2019, a ransomware named Snatch began doing something we don’t normally see happen during ransomware attacks: The infected computers rebooted into Windows Safe Mode, then began encrypting their hard drive.
The trick with Safe Mode in Windows is that it is designed to run with a minimal set of drivers and programs running in order to troubleshoot software problems. Booting into Safe Mode can inhibit endpoint protection, as that protection normally isn’t operational in Safe Mode.
There are certain situations where a PC needs a specific driver or file to run, even during Safe Mode, in order to do something critical (for example, have a working display). Snatch unexpectedly took advantage of this intentional feature of Safe Mode. During its infection process, the malware sets the registry keys that need to be there in order to run a particular file in Safe Mode. It plants its payload (the encrypting component), points the registry keys at it, and reboots the machine.
When the computer comes back up in Safe Mode, with the endpoint protection not loaded, the ransomware can launch its encrpytion payload and proceed to seal up key files on the hard drive unimpeded.
Abusing Exploitable Drivers
Retrospective analysis of attacks by a ransomware known as Robbinhood revealed that the attackers installed an otherwise benign third-party device driver in order to leverage a vulnerability in that driver. The vulnerable driver provided a stepping stone to the rest of the attack.
In the case of the attacks we analyzed, the attackers behind Robbinhood loaded a long-disused motherboard driver digitally signed by Gigabyte, the hardware manufacturer. Recent updates to Windows 10 mean that only these kinds of digitally signed drivers can run under normal circumstances.
The attackers use the Gigabyte driver, ironically, to turn off this feature in Windows that prevents the installation of hardware drivers that haven’t been cryptographically signed. Gigabyte withdrew the driver from the public several years ago and replaced it with newer software that isn’t vulnerable to the same types of abuse. But the Robbinhood operators found a copy and used it anyway.
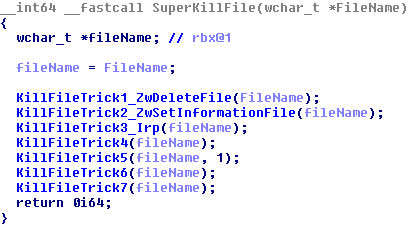
Once RobbinHood disables this Driver Signature Enforcement feature, the attackers then deliver yet another driver (this one unsigned) to the infected computer. The malware uses this second driver to load itself at an operational level low enough that, the attackers believed, they were able to make an end-run around endpoint protection tools. Using the cover of this driver, the Robbinhood attackers attempted to either terminate or hobble a large number of files and processes associated with a wide variety of security software.
All this effort took place before the ransomware begins encrypting files on the computer.
Extortion becomes an important secondary revenue stream
Several ransomware gangs have begun to leverage their presence on an enterprise network to steal sensitive corporate data at an early stage of the attack. Later, the attackers extort the victims with the threat of releasing of this stolen information to the public. Maze, REvil/sodinokibi, and Lockbit ransomware all engage in this secondary method of victimizing their targets.
As novel ransomware tends to appear at a regular pace, we’ve observed that most ransomware creators who launch a new ransomware family go through a similar set of growth stages over the first 6-9 months of operation, slowly escalating the feature set to incorporate a variety of techniques the attackers use to establish their persistence and move undetected within the network. Extortion is just the latest additional behavior we see from the more mature ransomware families.
Lockbit further thwarts analysis by not only deleting its own executable binaries, but also overwriting the space occupied by those files on the hard drive so they aren’t recoverable using data recovery software. It also had a long list of software it tries to terminate, including some programs with no security function: The malware simply wanted to make sure these programs were closed so any open documents could be overwritten more effectively during the encryption phase.

When in doubt, bring your own computer
One ransomware evasion technique that really stood out was attempted by Ragnar Locker: The malware could not perform its encryption while Intercept X was loaded, so the attackers built a headless Windows image for a VirtualBox hypervisor, and put the VM on every box they wanted to attack.
It was a devious ploy, since it appeared that any actions taken by the ransomware running inside the guest operating system had been taken by the process running the hypervisor. Since this is a trusted application, endpoint protection didn’t immediately kick in when the attackers executed all their commands from inside the VM guest.
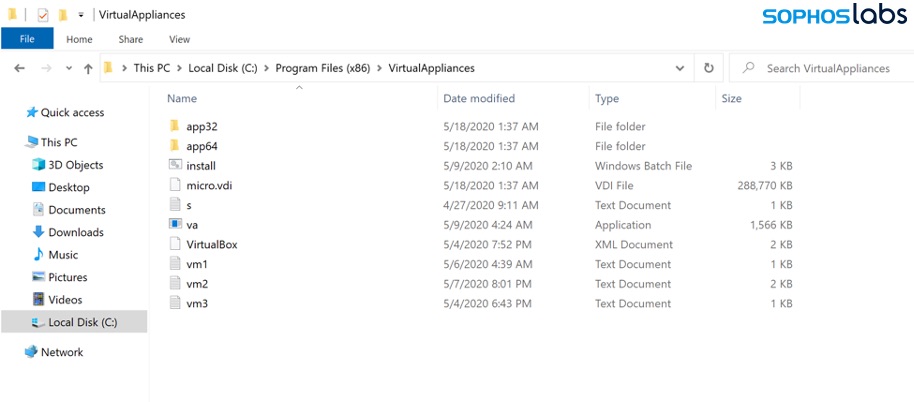
The virtual machine was comparatively huge, with an installer of more than 122MB, given that ransomware binaries aren’t usually more than a few MB in size. This was a real chonk. The attackers bundled an installer for an old copy of VirtualBox and the guest operating system disk image into an MSI file then tried to download a copy and launch it on every infected endpoint.
Only when the virtual environment was set up did the malware begin attempting to prepare its environment and then begin encrypting the hard drive. Initially, it appeared that the trusted VirtualBox process was the origin of the ransomware’s file encrypting behavior on the host computer, which was confusing for a number of reasons.
An increasing use of open source or public tools (and a growing library of exploits)
Discovering the malware repository used by the attackers behind the Netwalker ransomware gave us a lot of insight into the planning and technique required to carry out an attack. One thing it revealed was just how many free or open source tools the attackers needed to use throughout the attack.
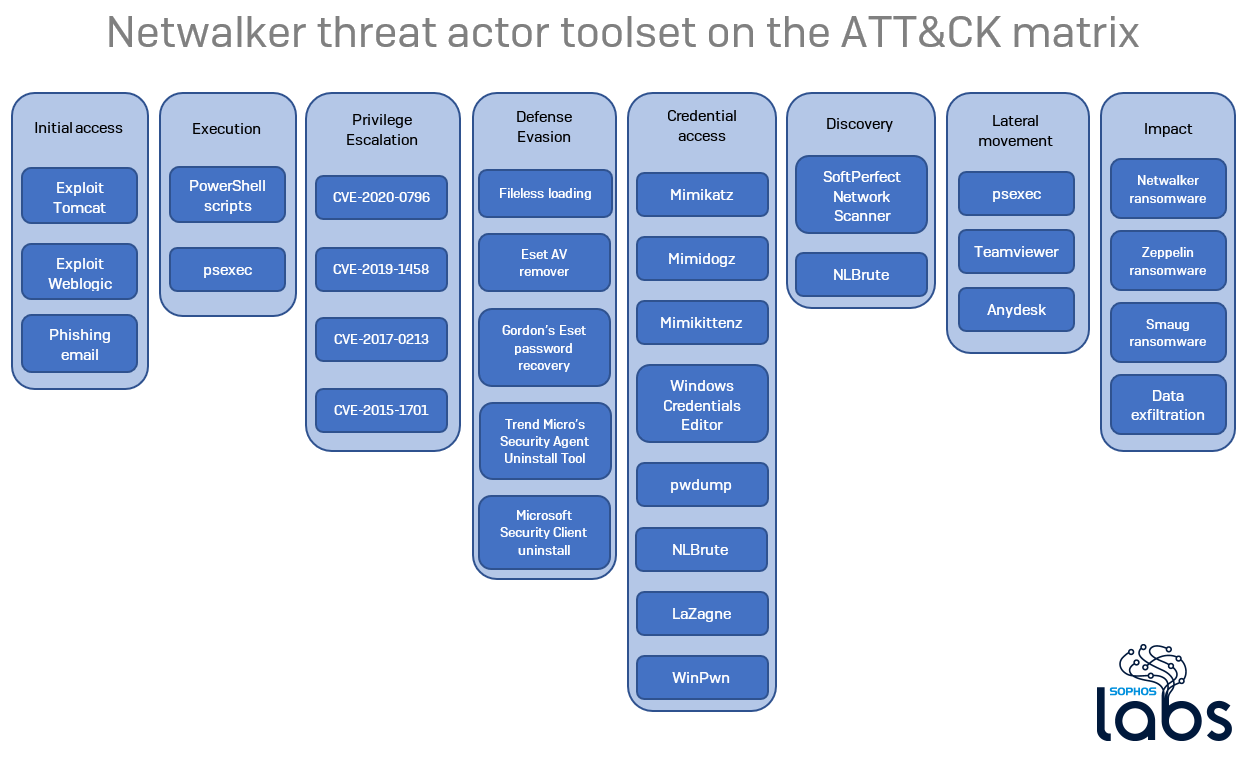
The attackers’ library contained a comprehensive set of tools used to perform reconnaissance on targeted networks; privilege-elevation and other exploits against Windows computers; and utilities that can steal, sniff, or brute-force their way to valuable information (including Mimikatz, and variants called Mimidogz and Mimikittenz, designed around avoiding detection by endpoint security) from a machine or network.
We also found a nearly complete set of the Microsoft SysInternals PsTools package, a copy of NLBrute (which attempts to brute-force passwords), installers for the commercial TeamViewer and AnyDesk remote support tools, and a number of utilities created by endpoint security vendors that are designed to remove their (and other companies’) endpoint security and antivirus tools from a computer.
Once inside the network of their target, the attackers apparently use the SoftPerfect Network Scanner to identify and create target lists of computers with open SMB ports, and subsequently may have used Mimikatz, Mimidogz, or Mimikittenz to obtain credentials.
The files we recovered also revealed their preferred collection of exploits. Among them, we found variations on the EternalDarkness SMBv3 exploit (CVE-2020-0796), a CVE-2019-1458 local privilege exploit against Windows, the CVE-2017-0213 Windows COM privilege escalation exploit published on the Google Security Github account, and the CVE-2015-1701 “RussianDoll” privilege escalation exploit.
What happens in memory stays in memory
This year’s outbreaks of the WastedLocker ransomware brought attention to this newcomer. The malware has already been implicated in some serious attacks, including against GPS device manufacturer Garmin, who reportedly paid a hefty ransom in order to re-enable business operations. WastedLocker has taken a different approach to the ransomware detection-evasion playbook by performing most of its malicious operations within volatile system memory. The technique is called memory mapped I/O.
This behavior has some benefits. With “traditional” ransomware, the malware’s behavior is observable because a binary executable makes a large number of file reads and writes as it encrypts the victim’s important data. Behavioral detection engines that look for this type of unusual activity would otherwise alert the user and/or halted the operation, limiting the damage. Because WastedLocker reduces the number of detectable reads and writes by a significant percentage, it may fall below the thresholds that govern suspicious activity in some behavioral detection rules.
In addition, WastedLocker takes advantage of an unintended consequence of how Windows manages memory, using a component called the Cache Manager. The Cache Manager is a kernel component that sits between the file system and the Memory Manager. The Memory Manager keeps an eye on memory that has been modified (known as “dirty pages”).
If a process encrypts the mapped memory, the Memory Manager knows which pages need to be written back to disk. This writing is done by the Cache Manager’s “Lazy Writer” component; Dirty pages are allowed to accumulate for a short time, and are then flushed to disk all at once, reducing the overall number of disk I/O operations.
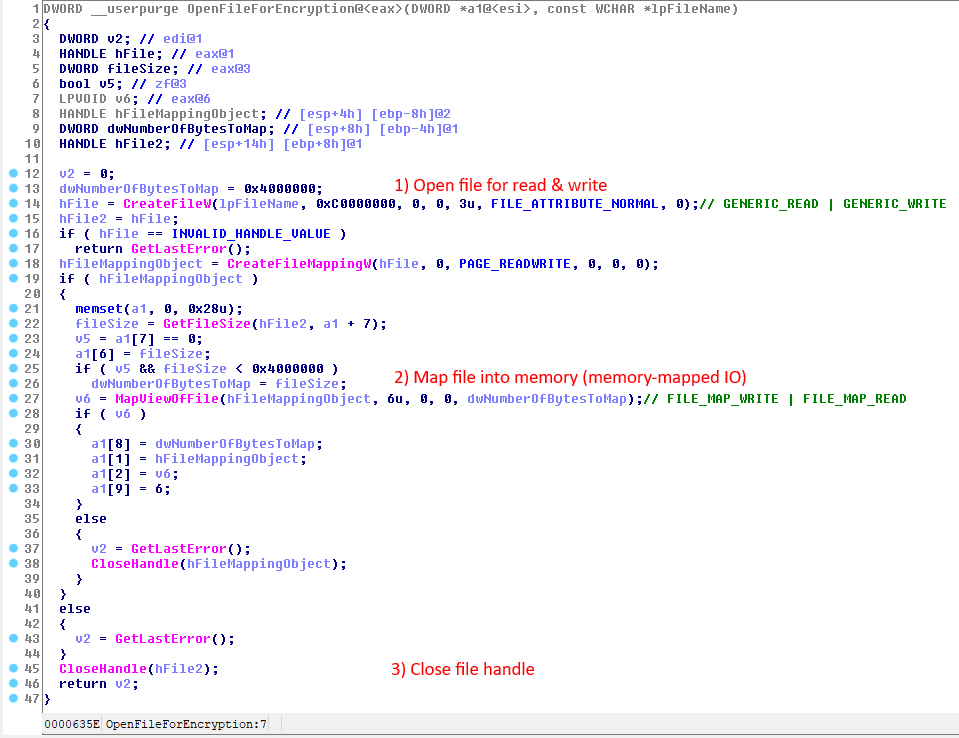
As a secondary unintended consequence of this, the writing of the modified files from their “dirty pages” back to the filesystem is done in the context of the system (PID 4), rather than the ransomware process, which then further complicates behavioral detection. After all, nobody wants to cause a victim’s computer to crash because an antimalware utility decided that the operating system itself was harming the computer. This technique also can hamstring less well qualified behavioral detection.
Prevention is the best defense
With all of these innovations in such a short period of time, it’s not hard to see why ransomware has been going through a renaissance. At the root of many, if not most, ransomware infections is the core issue that plagues so many organizations: A lack of due diligence and effort made towards reducing the attack surface available to malware. We’ve summed up many of these in the related article Ransomware attacks from the victim’s perspective.
If you work in IT security, your organization is relying on you to close the most obvious loopholes and back doors into the network. Basic PC hygiene, including installing all the latest patches, shutting down Remote Desktop entirely (or putting it behind a VPN), and applying multifactor authentication to services hosting the most sensitive data in the organization are just some of these fundamental steps you can take to protect yourself and your network today. If endpoint protection tools are the metaphorical net below the High Wire Act, applying patches and shutting down unnecessary holes in the firewall are the daily practice routines that will keep you out of the net when it matters most.
