Why do online swindlers rob people over the age of 60?
Because that’s where the money is.
According to the FBI’s 2019 Internet Crime Report, released on Tuesday by the bureau’s Internet Crime Complaint Center (IC3), the total amount of money clawed out of victims through a smorgasbord of cybercrime types just keeps climbing, with 2019 bringing both the highest number of complaints and the highest dollar losses reported since the center was established in May 2000.
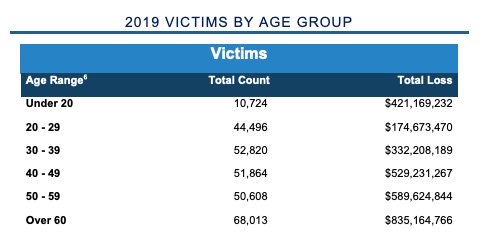
Those of us with gray hair tend to have the most money, and thus we have the dubious honor of being the most targeted and of having the biggest holes torn in our pockets. There were 68,013 people over the age of 60 who reported being victimized last year, and their total reported loss was $835,164,766.
The number steadily increases with age after the age of 20, but the younger amongst us – under 20 – are right up there when it comes to how much money they lose. Though only 10,724 victims under the age of 20 reported cybercrime in 2019, they reported stiff losses, at a total of $421,169,232.
More specifics from one of the report’s charts:
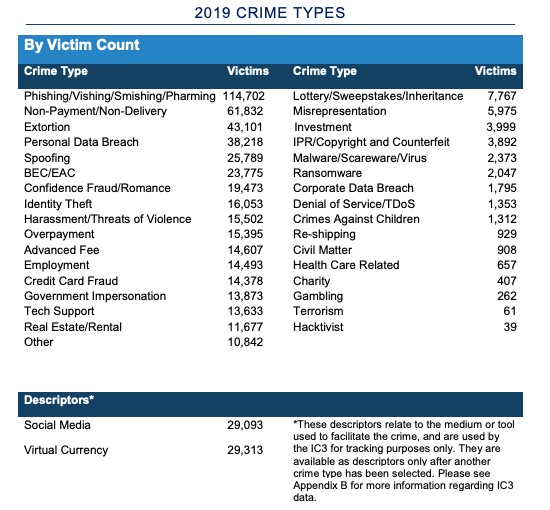
In all, the IC3 received 467,361 complaints last year – an average of nearly 1,300 every day, at a total swindle tally of more than $3.5 billion. Phishing and similar ploys were the most frequently reported complaints, along with non-payment/non-delivery scams and extortion.
But while crooks preyed on both individuals and businesses, businesses proved to be their most profitable targets, along with people who fell for romance or confidence scams. Spoofing was also how much of the money was made to disappear: used in business email compromise (BEC), spoofing is when crooks pose as known people or vendors in order to get personal or financial information out of their targets.
An ever-growing money-making racket
BEC has been a big money-maker for criminals for quite a while, and BEC scammers just keep getting more and more sophisticated at it. This is the second year in a row that the FBI cited increasing skill with these scams, which typically involve legitimate business email accounts that have been compromised, be it through social engineering or computer intrusion, to initiate unauthorized transfers.
Donna Gregory, the chief of IC3, said that the center didn’t see an uptick in new types of fraud last year, but it did see new tactics and techniques to carry out existing scams like BEC, which is also referred to as Email Account Compromise (EAC).
Criminals are getting so sophisticated. It is getting harder and harder for victims to spot the red flags and tell real from fake.
Specifically, spoofers aren’t just using email as a point of attack anymore, though that attack vector is still common. One example: in September 2019, we heard about scammers who used a deepfake of a CEO’s voice to talk an underling into a $243,000 transfer.
BEC can happen to any company, regardless of how hip to the inner workings of cybercrime they are. Even Facebook and Google have been fooled by these kind of scammers.
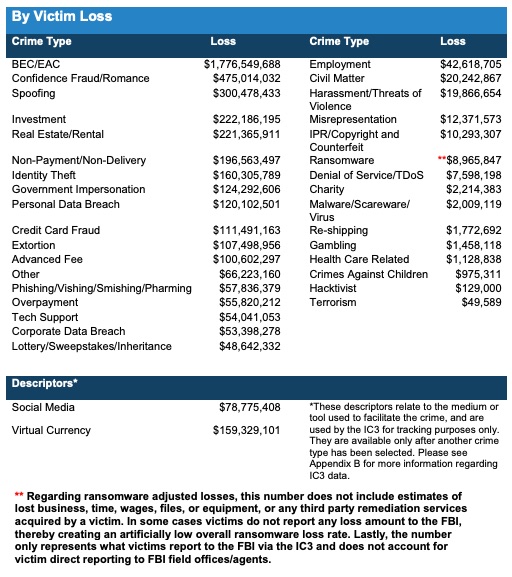
BEC/EAC scam isn’t the most reported crime (that would be Phishing/Vishing/Smishing/Pharming)…
…but it’s definitely the most profitable, accounting for nearly $1.78 billion of the total lost to cybercrime last year:
Last year, the IC3 saw BEC scammers increasingly focusing on diverting payroll funds. The crooks target a company’s human resources or payroll department, sending an email spoofed to look like it was sent from an employee requesting to update their direct deposit information for the current pay period, thus causing employees’ checks to get diverted into accounts that the swindlers control.
We saw a trio of alleged robbers in Australia get busted for this kind of fraud last week: they were charged with identity theft that netted AU$11 million (US$7.41m, £5.73m) – ill-gotten loot they allegedly ripped off by hacking into businesses and modifying their payrolls, pension payments (known as superannuation in Australia) and credit card details.
Phishing/Vishing/Smishing/Pharming
As far as the most commonly reported type of cybercrimes go, the IC3 notes that they’re seeing swindlers do it by texting – a crime called smishing – or via fake websites, a tactic called pharming.
Here’s Gregory again:
You may get a text message that appears to be your bank asking you to verify information on your account. Or you may even search a service online and inadvertently end up on a fraudulent site that gathers your bank or credit card information.
In order to protect ourselves, we’ve got to be “extremely skeptical” and “double-check everything,” the IC3 advises.That means independently verifying everything as if we were walking, talking authentication fobs – those gadgets used in two-factor authentication (2FA).
Gregory:
In the same way your bank and online accounts have started to require two-factor authentication, apply that to your life. Verify requests in person or by phone, double-check web and email addresses, and don’t follow the links provided in any messages.
Don’t suffer in silence – REPORT IT!
A few years ago, a report came out that detailed how elders, in spite of being the ones who suffer most often in these crimes, are often too embarrassed to speak up about it. Such underreporting is unfortunate. When the FBI gets a timely report, it can sometimes stop fraudulent transactions before the money is gone for good.
That’s what the FBI’s Recovery Asset Team (RAT) is all about: streamlining communication with financial institutions and FBI field offices. Last year, the RAT managed to recover more than $300 million for victims.
Gregory said that victims can help by giving as much detail as possible when they report crimes to the IC3: email addresses, account information given to them by the crooks, the phone numbers that the scammers called from, and anything else that might help.
The more information IC3 can gather, the more it helps combat the criminals.
Tech-support fakers
People over 60 are the ones targeted most frequently in some scams. One such is the tech-support scumbaggery of spooking older people by shoving scary “Your computer has a virus, call us!!!!” pop-ups in their faces and then fleecing them for services they didn’t need and never got.
In 2019, the IC3 received 13,633 complaints of tech support fraud, coming from victims in 48 countries who lost a total of more than $54 million. In spite of efforts from the tech companies to stop criminals from pretending to be legitimate support staff – Microsoft, for one, is devoted to battling these logo-absconding name ripper-offers – the IC3 says that the scams increased 40% in 2019 compared with the previous year. The majority of victims were over 60 years old.
Please do report any and all of these crimes, the IC3 asks, be they tech-support, EAC or phishing, so investigators can figure out how the scams work and how to stop them. Matt Gorham, assistant director of the FBI’s Cyber Division:
Information reported to the IC3 plays a vital role in the FBI’s ability to understand our cyber adversaries and their motives, which, in turn, helps us to impose risks and consequences on those who break our laws and threaten our national security. It is through these efforts we hope to build a safer and more secure cyber landscape.
You can report a cybercrime to the IC3 here.
Latest Naked Security podcast
LISTEN NOW
Click-and-drag on the soundwaves below to skip to any point in the podcast. You can also listen directly on Soundcloud.

Leave a Reply