Hear me, Ebenezer Everybody! Tonight you shall be visited by three spirits. The ghosts of the passwords you’ve used on your email account, your online bank account, your Twitter account, your Instagram account, your… OK, scratch that, you’ll be visited by at least 100 truly terrible password ghosts.
Their breath is foul, because some of us have reused them until they’ve begun to compost – an odor that attracts swarms of hackers who’ll use them to try to get into not just one breached account, but ALL of your accounts while they’re at it.
They’re spirits, because wow, these things are old. Seriously, are we seeing you again, “123456?”
Yes, we are.
Once again, it’s end-of-the-year, worst-passwords listicle time, and once again, “123456” reins supreme as the king of bad passwords on SplashData’s annual worst password list.
Just like it did last year. And in every year since 2013, when it knocked “password” from its number one spot.
Last year, SplashData evaluated more than five million leaked passwords to see how often they showed up. Since 2011, it’s been publishing the list based on millions of passwords leaked in data breaches. SplashData didn’t actually say how many breached passwords they analyzed for this year’s list, which it published in two sets of 50: here’s the worst 1-49, and here’s the worst 50-100.
Last year, tired of nagging users about using these clunkers, I instead took websites to task. Users are clearly never going to stop using “123456,” “123456789,” “qwerty” or “password” – 2019’s top four most commonly breached passwords – so how about if websites and services simply stop allowing users to choose passwords that are on the list of worst passwords?
Sites and services could do even more, we suggested – they could, say, disallow creation of any of the 10,000 worst passwords. Or maybe use rate limiting, which gives even the weakest password a serious upgrade. Limiting the number of times a user can try a wrong password means that attacks take a long time. Attackers have to be far more circumspect about how many guesses they make: as we noted, all you have to do is ask the FBI about how inconvenient, or impossible, it can make the task of forcing your way in past an unknown login.
Clearly, there’s still work to be done. Bad passwords are still being cooked up, and reused, though they don’t have to be. If you’d like a short, easy way to pick a proper password, you can watch our video:
(No video? Watch on YouTube. No audio? Click on the [CC] icon for subtitles.)
And if a website gives you the option to turn on two-factor authentication (2FA or MFA), by all means, turn it on. It will protect you even if you use something like a) “banana” (#97 on this year’s listicle), b) “whatever” (#58), or c) “cookie” (#95).
Maybe SplashData is tired of nagging users, too. Maybe that’s why it released the listicle without a lot of verbiage. Instead, it compiled a video full of imagery, including a) a kid dancing with a banana, b) comedian Mindy Kaling slapping her forehead, c) a bunny stealing a baby’s cookie.
Its pure, simple advice:
Don’t catch your passwords on this list …
Our own pure, simple commentary, based on this joyous season’s not-so-joyous password predictability:
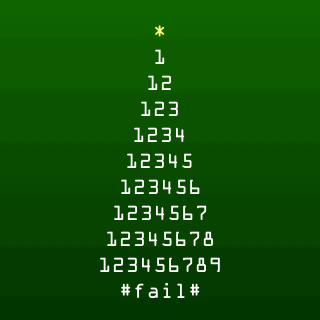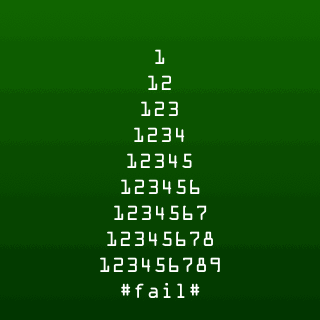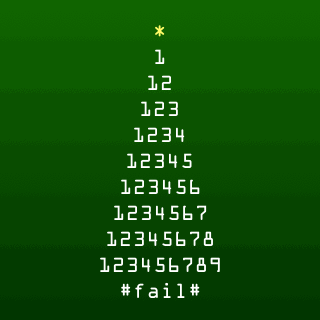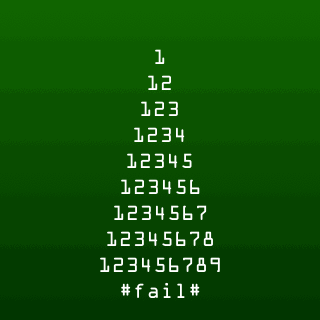
Deck the halls with password failure,
fail fail fail fail fail, fail fail, fail, fail!
Here’s hoping the new year brings us all good health, fewer breaches, and passwords that are as unique as snowflakes!

Anonymous
is there an infinite number of passwords?
Paul Ducklin
Technically, no. Most password input systems have some sort of limit on how many characters you can type in, and most password storage systems don’t save what you typed in but some sort of cryptographic ‘fingerprint’ of it, typically 64 bytes’ worth. The number of different passwords is therefore the lower of the number of different passwords you can possibly type in and the number of different passwords you can represent in your database.
Suppose that you have 64 bytes of stored hash, or 256 bits, for 2256 different passwords you can differentiate, and that you allow a maximum of 32 typed-in characters from a set of, say, 64, for 6432 = 2192 different passwords you can possibly enter. So the number of different typeable passwords is the lower value in this case.
Now 2192 passwords is not infinite, but it might as well be given how long it would take to try them all. (It’s more than one million million million million million million million million million.)
Even with 14-character passwords from 62 different characters (A-Za-z0-9) you have more than 280 different choices (one million million million million)…
…so you ought to be able to choose one that isn’t on the naughty list, despite the total number being finite!
George E Mays, III
I use Roboform for many years, BUT just recently I discovered they had a security center included, so much for just glancing at the instruction book or file. It includes, Password strength, How old each password is. Some over 1000 days use. It also shows if they have been reused and or duplicated on other sites. (Only three so far).
Michael Sosnin
Thanks for suggesting “snowflakes” as a password ; )
mom
Many websites calling for passwords don’t really need passwords. They simply have users log in to track their activity separately from others users, not to protect critical information.
Knowing this, why should a user select a unique password for the site? It’s a waste of brainpower and time, when 12345678 will do.
You make the nerd assumption that the user is lazy or foolish. This is nerd arrogance. Instead the user is intelligently choosing to get around the hassle of a website login in the lowest energy state. Nerds should commend it!
Paul Ducklin
The problem with website accounts is that, no matter how trivial the purpose of the account might seem, it’s still *your* account and it represents you in some way – for example by allowing the holder of the password to publish comments in your name.
There is never any reason to make it easy for other people to masquerade as you, no matter how unimportant that might seem.
If a website’s reason for making you have an account is so pointless that a password genuinely is not necessary, then that website has the wrong sort of approach to security (GDPR says not to ask for information you don’t require.) Don’t humour the site with a silly password… avoid it instead!
And use a password manager. It makes it easy to pick decent passwords all the time.
mom
There are very few sites where users really need to authenticate themselves and have a good password: work, banking, email, calendars/contacts, telecom, medical/pharmacy records, paid content/shopping, and government access.
Everything else, including social media and creative sites is of no consequence and really doesn’t need a decent password.
What if someone gets into your twitter? No consequence. Facebook? No consequence. Imgur? No consequence. Loyalty card at the supermarket? No consequence.
Paul Ducklin
No consequence having your Twitter or your Facebook account taken over? Are you SERIOUS?
One problem with an attitude like that it’s very much like the problem of people who are happy to keep on running XP or never patching anything “because I don’t care if my computer gets taken over and everything gets lost or stolen or destroyed, I never keep anything of importance on my computer.”
The thing is that *I* and millions of others care very deeply indeed, because it’s thanks to people who make it easier for crooks that *we* have to deal with yet more spam, yet more malware attacks, yet more bogus recommendations on social media, and so on. If a crook gets into your email, or your Twitter profile, they can instantly acquire a precise list of all your friends…
…and so your insecurity affects other people.
Please don’t be the sort of person who refuses to wear a seatbelt when in the rear seat of a car because they don’t care what happens to them… rear seatbelts exist *to protect the person in front of you* from *your* kinetic energy in the event of a collision.
Also, there’s usually so much more that a crook can learn about you from the inside of your social media accounts than from what you have made public that you are inevitably helping them attack your other accounts by giving them hints about how better to convince other people that they know you really well, or even that they are you.
There’s just no reason to make yourself part of the problem when you could so easily be part of the solution.
Bryan
Best argument ever.
…at least for those seeking to refute the time-honored advice “always listen to your mother.”
Bryan
Mom, by this logic one would be “intelligently efficient” by not bothering to secure one’s locker at the pool. After all, it protects a patently paltry proportion of personal possessions when juxtaposed with the player piano and Panasonic plasma–guarded by a new security panel and exuberant canine.
Enjoy walking home in your swimsuit; the load will be lighter without needing to lug those heavy car keys.
Bryan
Lisa, as a musician (and fan of the song referenced by the title), I hereby present My Opinion Unsolicited:
I will read your article as written.
But as I sing it in my head**, it shall be pronounced
“hello [bad password] my old friend;
I’ve come to talk with you again”
…as it’s the only way I can fit the rhythm, ever since my failed aspirations of becoming a world-renowned auctioneer.
.
Solid article, btw
:,)
.
** or mostly therein, at least