As the world rolls into another Cyber Monday, and online shoppers continue their hunt for the best deals, SophosLabs wants to remind you that there’s a metaphorical malware elephant in the room that would like nothing more than to steal financial information, and the use of your computer, for nefarious ends.
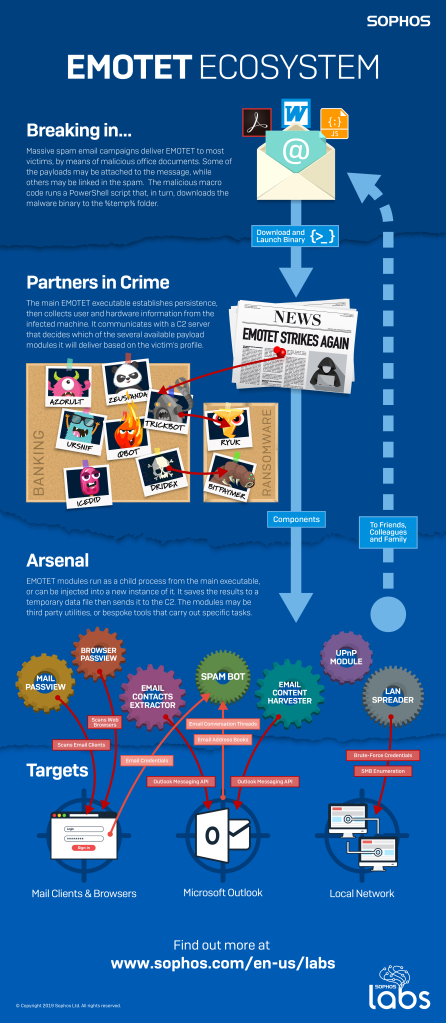
The Emotet Ecosystem infographic, produced by experts within SophosLabs, describes the infection process and subsequent behavior commonly displayed by samples in the Emotet malware family. Emotet is routinely among the most problematic and widely distributed malware family that Sophos researchers encounter daily. If there were such a thing as a Most Wanted list for malware, Emotet would surely top the list.
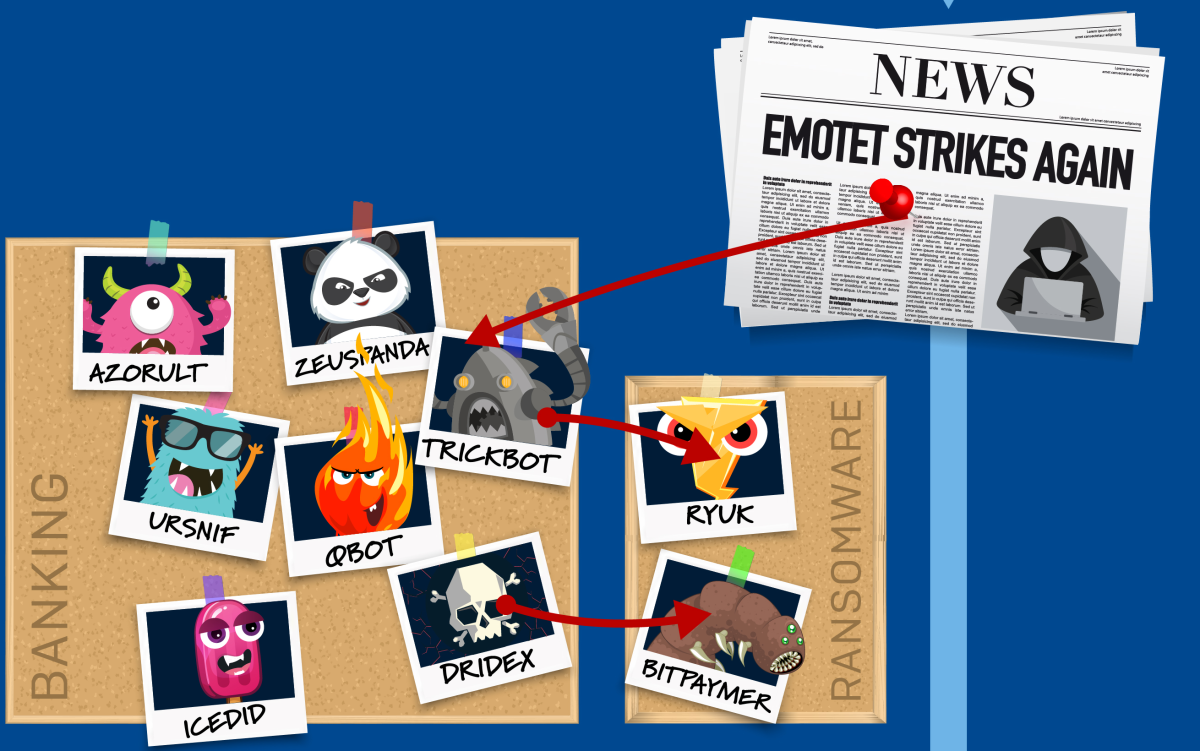
Emotet serves a purpose both as a standalone malware capable of causing significant harm on its own, and as a distribution network for other malware families, whose operators appear to engage with Emotet’s software distribution capabilities as a matter of routine. Part of the payload package may, in fact, be components that assist Emotet in finding and infecting other victims. In this way, Emotet plays a uniquely central role in a wide variety of malware infection scenarios, just a few of which are illustrated here.
You may download a full-resolution version of the infographic either as a PDF or as a .PNG image.
Most Emotet infections begin with a malicious spam email that prompts the recipient to open a malicious Microsoft Office document. The document may be attached to the message, or the message may contain a link to download the document from a website. When someone opens one of these documents, it retrieves the Emotet malware executable and launches it (usually from the %temp% folder) on the victim’s computer.
After establishing persistence (the ability to start itself after a reboot), the malware sends profile information to its operator(s) about the victim and their computer. Knowing about the victim, their computer, and the network on which it is running helps the criminals decide what payloads to deliver. Emotet routinely delivers samples of one or more families of credential-stealing Trojan malware, such as Trickbot, Dridex, Ursnif, or Azorult.
Depending on what the profile information reveals about the target, and the goals or priorities of the attacker, the attacker may leverage the payloads that Emotet distributed to deliver ransomware or other malware payloads. For example, Emotet may deliver Trickbot to the target machine, and then Trickbot may deliver the Ryuk ransomware to that same machine.
The Emotet ecosystem also includes a variety of payloads the malware uses for a variety of ancillary tasks. These payloads may steal and exfiltrate credentials, laterally spread the malware within the network in which the infected machine is located, scrape the target’s hard drive for email addresses, harvest data from the contents of email messages sent to and from the target, or even use the infected machine to send out new spam campaigns to the newly discovered targets.
Some of these additional payloads include legitimate tools for power users that have been publicly available for some time, such as NirSoft’s Mail PassView or Browser PassView. Several of the payloads appear to be specialized for the task, such as the mail scraper/spam bot components. These components extract message text and subject lines from Outlook, which the spam bot component uses to inject a weaponized office document file into the middle of an email thread between the victim and one or more potential targets, using the same subject line as the original message thread.
Such techniques help ensure the Emotet ecosystem continues to grow and flourish, at all of our peril.
Leave a Reply