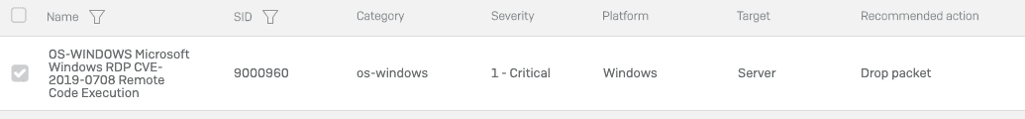
CVE-2019-07-08, nicknamed BlueKeep, is a critical remote code execution vulnerability in Windows’ Remote Desktop Services. The bug is considered ‘wormable’ and so severe that Microsoft took the highly unusual step of including patches for the unsupported Windows XP and Windows Server 2003 in its May Patch Tuesday output, alongside patches for the affected operating systems it does support.
If this flaw is successfully exploited it could be used to create self-replicating malware like Slammer, WannaCry or NotPetya – a trio of network worms that used exploits to invade networks and spread globally in a matter of hours.
Patches that could have stopped those worms from spreading were available months before the outbreaks occurred. The race is now on to make sure history doesn’t repeat itself with CVE-2019-07-08.
So far the signs aren’t good. Two weeks after Microsoft’s patches dropped a scan revealed that a million unpatched devices were accessible over the internet, with likely millions more hidden from view, inside corporate networks.
Yesterday, the NSA (the U.S.A.’s National Security Agency) was moved to issue its own advisory, urging organizations to get on with the business of patching.
It is likely only a matter of time before remote exploitation code is widely available for this vulnerability. NSA is concerned that malicious cyber actors will use the vulnerability in ransomware and exploit kits containing other known exploits, increasing capabilities against other unpatched systems.
Patching doesn’t get much more urgent than this but, as previous outbreaks have shown, it takes time.
An exploit could appear at any time so you need a way to protect yourself now, until the patching is done. As both Microsoft and the NSA say in their advisories, your Firewall can be your line in the sand.
Protect your organization against BlueKeep
All firewalls can pull up the drawbridge by blocking access to port 3389, which disables external RDP access for all machines, including the ones that nobody told your IT team about.
Besides blocking and unblocking vulnerable ports, Sophos XG Firewall provides other more nuanced and sophisticated layers of security. Its built in Intrusion Prevention System (IPS) looks at network traffic for exploits and stops them from passing through your network perimeter, or traversing the segments of your internal network.
At the same time that Microsoft announced the CVE-2019-07-08 vulnerability, SophosLabs issued an IPS update for all Sophos customers to ensure their XG Firewall-protected networks could stop these kinds of attacks dead in their tracks.
 While we have a full guide on how to protect your network, here are the essential firewall best practices to stop vulnerabilities like BlueKeep from exposing your network:
While we have a full guide on how to protect your network, here are the essential firewall best practices to stop vulnerabilities like BlueKeep from exposing your network:
- Reduce the attack surface by reviewing your port-forwarding rules and eliminating any non-essential open ports. Where possible use a VPN rather than port-forwarding to access internal network resources from the outside.
- Minimize the risk of lateral movement by using XG Firewall and Sophos Synchronized Security, and consider segmenting your LANs into smaller subnets and assign them to separate zones that are secured by the firewall.
- Apply IPS protection to the rules governing traffic to and from any Windows hosts on your network, and between your network zones to prevent worms from spreading between LAN segments.
XG Firewall and Synchronized Security are your best protection against the latest threats with industry leading protection and performance. Download our Firewall Best Practices to Block Ransomware guide to learn more.

Nataraj
Kindly send us the latest update on Sophos Fire Wall