Over the past few months, we’ve written and spoken many times about a scam known as sextortion.
Sextortion is an online crime that combines sex and extortion – the crooks say that they have embarrassing pictures of you, and they’ll send the pictures to your friends and family…
…unless you pay them blackmail money.
To make the scam seem more believable, the crooks typically claim to have acquired the pics via your own webcam by hacking into your computer using malware and snooping on your online activities.
Sadly, this sort of malware, known as a remote access trojan (RAT), is not only technically possible, but has been used in the past in a number of widely publicised attacks.
One well-known RAT attack involved a college student called Jared James Abrahams, who supposedly spied on 150 young women including Miss Teen USA. Abrahams was caught, pleaded guilty and went to prison back in 2014. More recently, Jonathan Lee Eubanks got seven years for RATting his former employer’s business, wiping servers, diverting the website and ripping off company funds after he was fired.
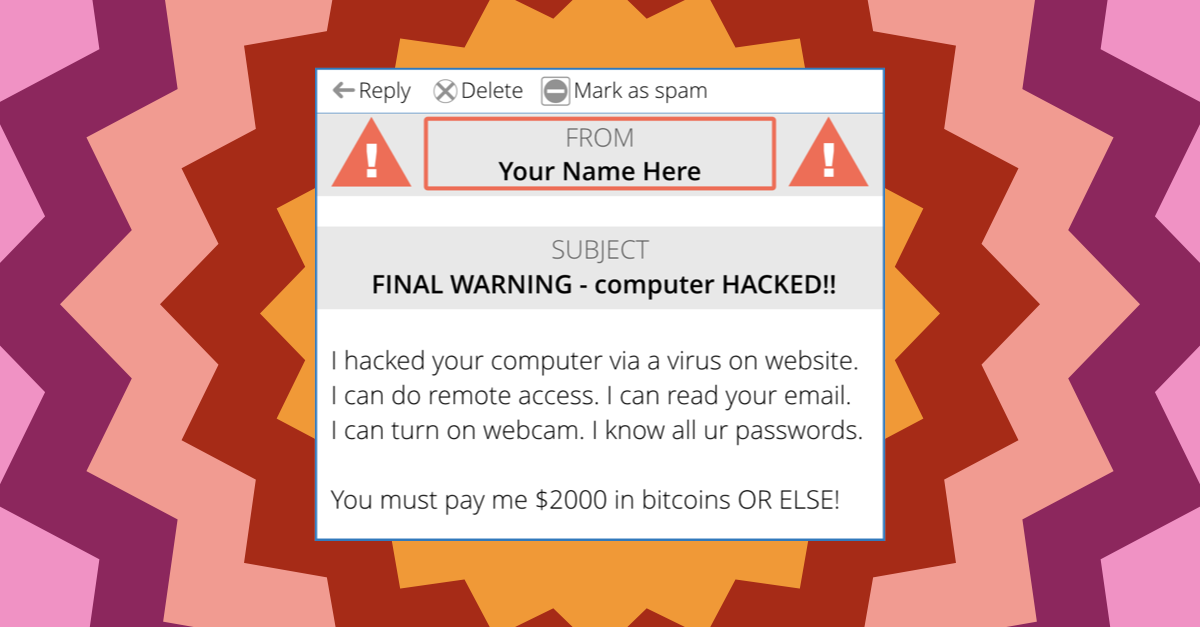
Even if you never look at porn, sextortion emails are pretty confronting, and raise the question, “How much might the crooks know about me?”
Sometimes, sextortion emails arrive apparently from your own account, which frightens a lot of people into thinking the crooks already have access to their computer.
So we thought we’d make a short video that you can show to friends and family, just to clarify that the From: line in an email is as much under the control of the sender as the Subject: line or the text in the email itself:
(Watch directly on YouTube if the video won’t play here.)
What to do?
Most email programs, including webmail services such as Outlook.com and Gmail, automatically fill in the From: part for you and won’t let you pretend to be someone else – but that’s your email software protecting you from yourself.
The crooks don’t use that sort of email software – they use spam-sending “mail cannon” programs that let them structure their messages however they like, such as those spoofed emails you so often see.
So, don’t freak out! Just dump it in the trash.
Bryan
> Sextortion mail from yourself?
Dang. I owe me a lotta money.
:,(
Warren Burstein
I was looking at one of those spams because my sysadmin thinks I can do something about them (I don’t think I can). I noticed that if someone tried to send the Bitcoin they would have to type 34 characters of case-sensitive gibberish for a Bitcoin wallet address. While the email advises the mark to cut and paste the string, the email arriaves as an image, so that isn’t possible.
It would be amusing if the scammer didn’t get any money because out of the few people who tried to respond to the fake blackmail, none of them managed to type the wallet address correctly.
Paul Ducklin
Most (or at least many) of them arrive as text emails that can be copy-n-pasted from…
Ironically, putting text into an image format is supposed to make it harder for spam filters (it probably doesn’t but that’s the crook’s hope) yet – as you say – also makes it harder for humans to use, so a case of cybersecurity swings and roundabouts :-)
Robert Gracie
Its hilarious how many I have gotten over the years but I know they are all fake simply because you have to use my phone to get access to my computer, so how could they hack in when my password requires a second part from my phone, they cant so I know its phony the second I open it and read “You have been hacked” um really, no I havent since you dont have my phone to get into my computer….
Bryan
@Robert Gracie
You have 2FA on your desktop? I’d be curious to check that out–what platform/software?
…and how gracefully does it handle Internet outages?
Comcast support: “there, I updated your modem–please check your connection”
“I can’t.”
“um… excuse me?”
Bryan
PS though:
Catching malware in your daily computer use could still cause a breach (even theoretically one as this hoax describes). Once logged in you’re just as subject to the same security rules and mishaps as everyone else.
Paul D Flahive
Good story. Misspelled word in last graph “progrms.” just thought you would want to know.
Paul Ducklin
Fixed, thanks!
SuitablyHumiliated
Well this part “Sadly, this sort of malware, known as a remote access trojan (RAT), is not only technically possible, but has been used in the past in a number of widely publicised attacks.” just got me worried all over again :((
Can RAT be put on an iPhone? I only watch porn on my iPhone LoL
pithecanthropus erectus
@SuitablyHumiliated Not sure iPhone but RAT does with android phone (i guessed). Mostly 95% use mobile these days to access anything and somehow received a sextortion email scanned as spam in spam allocated inbox showing as my personal email and password. Pretty good job I should impress what they can accomplished these days and yes i condemn malware.
Jimm Mokeyson
Its funny because it said it accessed my webcam but my computer doesn’t have one