Imagine that you’ve been hit by ransomware.
All your data files are scrambled, you’re staring at a ransom note demanding $1000, and you’re thinking, “I wish I hadn’t put off updating that cybersecurity software.”
When the dust has settled – hopefully after you’ve restored from your latest backup rather than by paying the blackmail charge – and you’ve got your anti-virus situation sorted out, your burning question will be…
…where did the malware come from?
But what if, no matter how carefully and deeply you scan, you can’t find any trace that there ever was any malware on your computer at all?
Unfortunately, as our friends over at Bleeping Computer recently reported, that can happen, and it’s one case where not being infected yourself is actually a bad sign, rather than a good one.
The Bleeper crew have had several reports of users whose files were scrambled from a distance across the internet, by ransomware running on someone else’s computer.
It’s a bit like suffering from a malware attack while you’ve got a USB disk plugged in – if your computer can access files on the plug-in device over the USB cable, you’ll end up with files scrambled on both your laptop and the USB disk, but the malware program itself will only ever show up on your laptop.
The USB drive will be affected but not infected
The same sort of thing often happens across the local network in ransomware attacks inside a company, where a single infected computer on the network ends up scrambling files on all your servers, because the user happened to be logged in with an account that had widespread network access.
In the end, hundreds of users and hundreds of thousands of files many get affected, even though only one user and one computer were ever infected.
Over the internet?
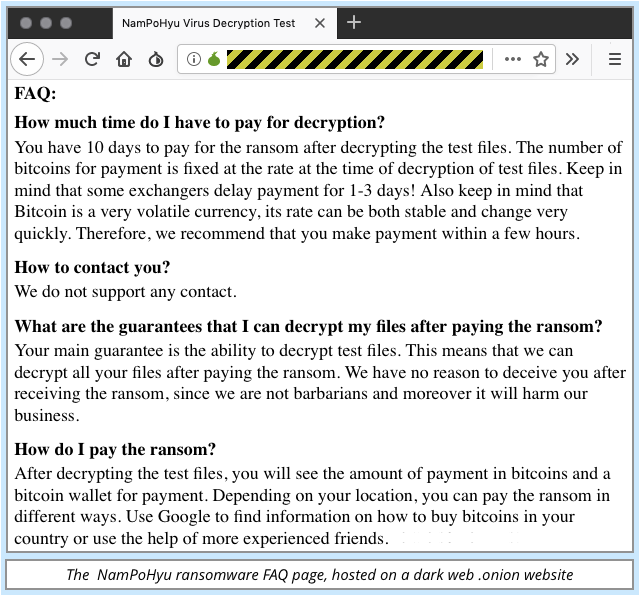
Bleeping Computer has dubbed this latest strain of remote-control ransomware NamPoHyu – that’s the moniker that pops up when you visit the malware’s web page – but the name doesn’t help much, because there isn’t any malware file that you can go looking for if the attack started from afar.
It could have been almost any ransomware that did the damage, and that’s the problem.
Of course, this raises the questions, “How on earth can file-scrambling malware work over the internet, and how can crooks purposely aim it at me?”
Sure, lots of companies, and many home users, run web servers, gaming servers, remote access servers, and so on, but who runs plain old file servers over the internet?
Who would leave their computer sitting online so that crooks anywhere in the world could type in a Windows network mapping command such as the one below?
C:\> net use j: \\203.0.113.42\C$
If your computer is online at the IP number 203.0.113.42 and accepting Windows networking connections, the above command will leave the crooks with a J: drive that lets them wander around your files at will, as easily as if those files were on their C: drive.
Few, if any people, would let crooks share their local drives on purpose, but surprisingly many leave their local disks open by accident.
Microsoft’s file sharing protocol – the protocol that lets you open up your disks with the command net share and connect to other people’s disks with net use – is now officially known as CIFS, short for Common Internet File System, but it started life with the jargon name of Server Message Block, or SMB.
Back in the early 1990s, when prolific Aussie coder Dr Andrew Tridgell started his open source implementation of SMB so that Linux and Windows computers could work together more easily, the acronym SMB was turned into the pronounceable name “Samba”, and that’s the name you’ll probably hear used most frequently these days, by Windows and Linux users alike.
Samba is what does the sharing, and shares are what you connect to on servers that you’re supposed to access.
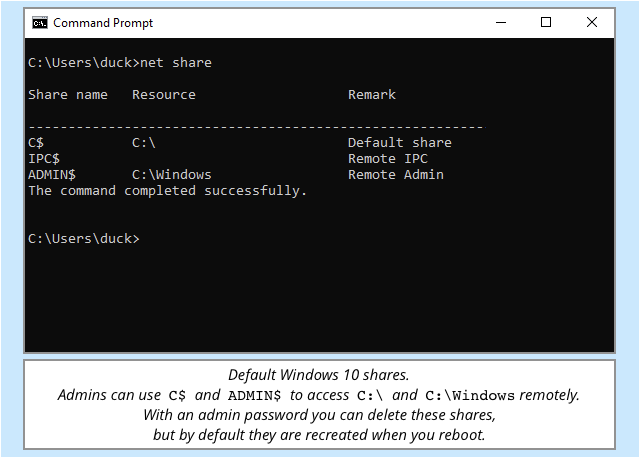
You can create your own shares (use the command net share to list them all) with handy names, such as DOCUMENTS or SOURCECODE, and Windows will automatically add some special ones of its own, notably two default (and hard-to-remove) shares called C$ and ADMIN$ that give remote access directly to your C: drive and your Windows directory respectively.
Annoyingly, shares with names ending in $ are hidden, so it’s easy to forgot they’re there – something that many people, sadly, do.
Not just anyone can hack into C$ and ADMIN$, of course – you need network access directly to the target computer, which you wouldn’t normally get through a firewall or home router, and you need an Administrator’s password.
So far, so good…
…except that, as we write about rather too often, many users have sloppy habits when it comes to choosing passwords, making them easy to guess, and many devices that were never supposed to be accessible to the outside world show up by mistake in internet search engines.
WARNING. It’s tempting, and dangerously easy, when your’re sitting at home having troubles playing the latest game, to get round your setup hassles by simply lowering your firewall security shields. Maybe you went into your router and temporarily told it that your laptop was your “gaming server”, for example? If you allowed in all traffic for troubleshooting, how many crooks took a peek while your security was off? If everything started working while you were testing, did you remember to put your shields back up afterwards, or did your temporary fix become your permanent one?
Remote ransomware attacks
Simply put, if crooks can see your Samba shares from out there on the internet, and can guess your password, they can theoretically wander in and do what they like to your files.
They can therefore attack your computer – manually or automatically – simply by pointing one of their computers, or someone else’s hacked computer, at yours and deliberately “infecting” themselves with any network-enabled ransomware they like.
Many, if not most, modern ransomware samples include a feature to find and attack any drives visible at the time of infection, in order to maximise damage and boost the chance that you’ll end up having to pay – that includes secondary hard disks, USB devices plugged in at the time, and any open file shares.
In other words, if you’re at risk of a remote ransomware scrambling attack, the real situation is actually much worse than that.
It may sound like cold comfort, but a ransomware attack is one of your “least worst” outcomes, because your files get overwritten but not stolen.
Instead of ruining your files, the crooks could choose simply to copy them off your network to use later, and that sort of attack [a] would be much less noticeable [b] would be impossible to reverse and would affect and expose anyone else whose data was stored in those files.
What to do?
- Pick strong passwords. And don’t re-use passwords, ever. You can assume that crooks who finds your password in a data dump from a hacked website will immediately try the same password on any other accounts or online services you have. Don’t let the password for your online newspaper subscription give the crooks a free ride into your webmail, your social media and any computers and file shares you have.
- Keep your shields up. If you’re having connection troubles, resist the temptation to “turn off the firewall” or “bypass the router” to see if that solves the problem. That’s a bit like disconnecting your car’s brakes and then going for a ride to see if performance improves.
- Run anti-malware software. Even on servers. Especially on servers. Your laptop isn’t supposed to be open to the internet, and generally won’t be. But many of your servers are online and accessible to the world on purpose, so although they can be protected by a firewall, they can’t be fully shielded by it, and that’s by design.
- Consider using a ransomware blocker. Tools like Sophos’s own Cryptoguard can detect and block the disk-scrambling part of a ransomware attack. This offers you protection even if the malware file itself, and its running process, is out there on someone else’s computer that you can’t control.
- Make regular backups. And keep at least one recent copy offline, so you can access your precious data even if you’re locked out of your own computer, your own network or your own accounts. By the way, encrypt your backups so that you don’t spend the rest of your life wondering what might show up if any of your backup devices go missing.
LISTEN NOW
Learn more about strong, unique passwords and why they matter (starts at 01’18”).
(Audio player above not working? Download MP3, listen on Soundcloud or access via iTunes.)

zeke
Hello Paul,
Just 1 question: i have read online that the latest version of sophos AV home for mac incorporates AI technology. Is this technology offered in both the premium and free versions (or is it only offered in Premium version)???? Thanks, best wishes, zeke
Paul Ducklin
As it happens, Machine Learning, a.k.a. AI, is a Windows-only thing at the moment [2019-04-18], so neither Home Free nor Home Premium on the Mac has it. (On Windows, AI is included in Premium but not in Free.)
There’s a chart of the Home Edition Free-versus-Premium differences on the Mac platform here:
https://home.sophos.com/en-us/free-mac-antivirus.aspx
HtH.
Malcolm D
Duck, unfortunately some nits have crept in:
* being infected *yourelf* is actually a bad sign,
* by Windows and *Linuyx* users alike.
* with any network-enabled *ransomwre* they like.
* hacked website will *immdeiately* try the same password
//M
Paul Ducklin
Fixed, thanks.
I’ve been putting off replacing my very-heavily-used MacBook 12 – the early model with the not-so-great keyboard even when it was new – because I have a nagging feeling that I will end up with a MacBook Pro 15 (the raw power!) in its place. 6 cores, 32GB, gorgeous screen, I know I will like it, but there’s something about the lean-mean-clean lines of the 12 that I just never get tired of. And the brilliant simplicity of a single, solitary USB-C port, which I consider a triumph of form over function, where everyone else just moans about it.
But the dodgy keyboard is starting to try my patience…
Mahhn
It’s tough to let go of old tech that we like. Take the KB apart and try and fix it, if you can’t – now you get a new system, if you can, ahh, such a good feeling. I’ve spent hours fixing things worth only a couple bucks, just for the satisfaction, and it’s worth it – insert smile emoji
Paul Ducklin
Take apart a 2015 MacBook 12? Even iFixIt freaked out to take that one apart… they gave it 1/10 for repairability :-) I just use a lot of aircan spray from the photography shop…
Frank
I have been called many things for using Linux, but never “Linuyx users”.
Paul Ducklin
There’s a first time for everything!
Laurence Marks
Duck wrote”… did you remember to put your shields back up afterwards, or did your temporary fix become your permanent one?”
With apologies to Steve Gibson, of course.
Paul Ducklin
Not at all – with apologies to Star Trek :-)
Someone Somewhere
Honestly, if you are leaving your computer exposed via SMB over the Internet in 2019, you’ve got nobody to blame but yourself. One would have to go severely out of the way to facilitate such an exposure as default settings and firewalls would be preventing this from working left-and-right unless you intentionally disabled them all. At that point, the question needs to be raised whether you should be left in charge of an Internet connected device at all…
Paul Ducklin
I hear you, but I still have plenty of room for compasssion.
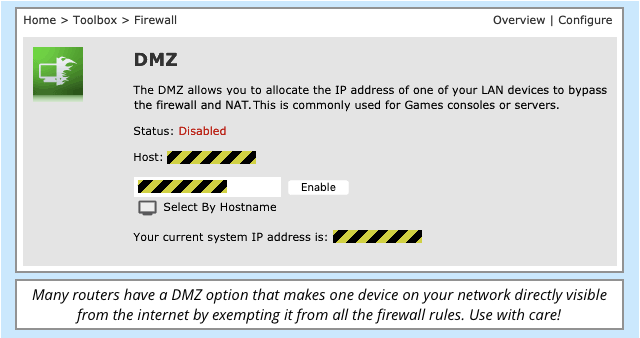
The *blame* lies with the crooks. And it’s possible to end up with SMB resources exposed to the wide world by mistake even if you’re trying to be careful – UPnP, for example, the dreaded DMZ button in many home routers (intended for opening up gaming servers to the world), a badly configured router at a friend’s house, and so on. None of that justifies getting stood over by crooks to get your files back.
We discussed this very issue – “but how can this happen?” – in this week’s Naked Security Live video.
Nobody_Holme
Video invisible, please to add link for the terminally lazy (hi, that’s me)
Paul Ducklin
Done.
Nobody_Holme
You are, as always, a gentleman and a scholar, sir.