If you have an IoT device in your home, you could be receiving an average of 13 login attempts to these devices per minute.
That’s what I found in my latest research project. Over the past 3 months, I’ve setup and monitored 10 honeypots located across 5 different continents. These have been waiting patiently for SSH login attempts to better understand how often you face cybercriminals knocking at your network’s metaphorical front door.
Once I’d set up the honeypots, it took no time at all for the hackers to begin their login attempts. In one instance, a device was attacked less than one minute after deployment, in others it took nearly two hours before login attempts began. But once the login attempts started, the attacks were relentless and continuous. In total, I saw more than 5 million attempted attacks on all my honeypots, over the 30-day period they were live.
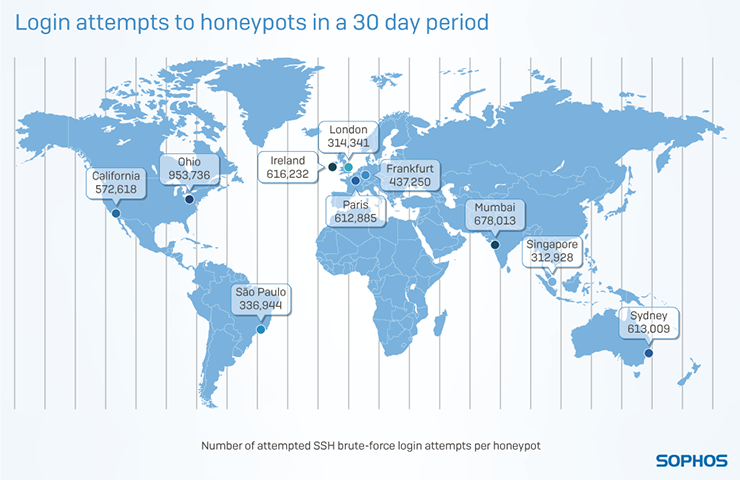
But that wasn’t all I found.
Default usernames and passwords
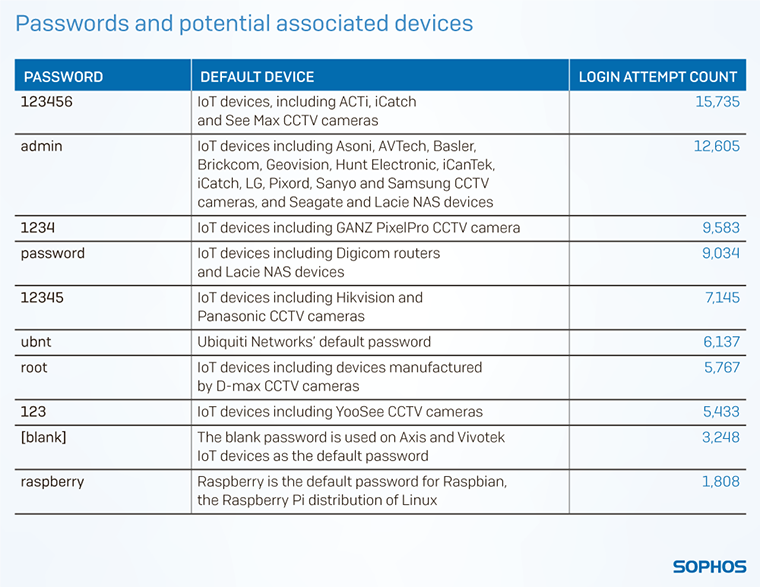
The research revealed that a lot of the login attempts monitored on these honeypots were using default usernames and passwords of devices that the average person would find in their home.
I saw default username and password combinations for routers, CCTV cameras and NAS devices, and combinations like the username pi with the password raspberry popping up together many times over.
This is the default username and password combination for Raspbian, which is a distribution of Linux designed for the Raspberry Pi.
Why is my device online?
Maybe you’re reading this feeling safe, because your router, camera or other IOT device is safely tucked behind Network Address Translation (NAT), hidden from the outside world.
You might not be as safe as you think. Earlier this year, a hacker that goes by the name of TheHackerGiraffe proved that NAT provides us with a false sense of security when he/she found over 70,000 Chromecasts had made their way to the outside world and could be contacted by anyone.
TheHackerGiraffe took the liberty of playing an unwanted video on just over 65,000 of these devices.
Why is it that our home devices are popping up online?
The answer is Universal Plug and Play (UPnP).
UPnP in its current form is designed for convenience. It’s a system that makes it easier for home networking devices to talk to one another through a domestic router or gateway without the user having to do anything.
But the security issue with UPnP is one with the IOT vendors’ implementation. UPnP is implemented on almost all modern routers, and can automatically set up a rule to reveal your device to the internet (and everyone on it) through your NAT – something known as port forwarding.
Password patterns
We’ve mentioned before on Naked Security that the more random your password, the less likely it is to be guessed. But many of the password attempts on my honeypots follow a pattern.
1qaz2wsx and 1q2w3e4r were seen frequently in login attempts to all regions. Although, as a password these aren’t as obviously bad as qwerty, if you take a moment to look at your keyboard, you’ll see the correlation of letters and numbers is very tight.
These passwords have been used so frequently that they are near the top of the cybercriminals’ toolkit. In fact, 1qaz2wsx has been seen 756,613 times and 1q2w3e4r 631,071 times in data breaches, according to breach website Have I Been Pwned.
What to do?
How everyone can stay secure
- Change passwords from their default
- Use a complex and unique password for every service
- Use a password manager to keep track of passwords, so you only have to remember the manager’s master password
- Turn off UPnP on your home router
How to keep your business safe
- On SSH servers, use key-based authentication, not just a password
- Use fail2ban on Linux servers to limit the number of login attempts someone can make
- Use Sophos Antivirus for Linux (it’s free) to catch known payloads that are dropped by the adversary once they’re in
Want to learn more?
Read the full report: Exposed: Cyberattacks on Cloud Honeypots.

Barbara Laumann
i just want to thank you for protecting my computer. I am 75 & so non technical. But I have a Macbbok air a Apple watch & an apple phone. I use my computer daily. You have protected me from 4 viruses and removed them. I do not understand the tech jargin or abreviations and am convinced my 6 yr old great grandchild knows more than i do. But Sophos gives me reassurance that I am protected.
Thank You,
Barbara
Steve
You are not alone, Barbara. This site’s motto should be “Get Naked & Stay Covered!” ;-)
John Knops
Why would I want to use a “password manager” when we know that via the internet someone can get past Sophos protection and download all my passwords? If Walmart’s wifi server can stop me from accessing my favourite swimsuit selling site, calling it “porn” ( the company manufactures and sells online and at retail swimsuits only ) why can’t the same server read my iPad and download my password manager file? It may be encrypted but that is just an extra minimal, tiny, step to deal with.
Paul Ducklin
Decrypting a file you’ve downloaded, assuming that the encryption is correctly implemented, is more than a “minimal, tiny step to deal with.”
If encryption, properly done, were routinely that easy to bypass we wouldn’t have had cases like FBI Versus Apple over decrypting locked phones…
A password manager does, indeed, concentrate your risk. But compared to the risk of using one guessable password on many websites – such that someone else’s security failure could open up your whole online life – a password manager is almost certainly a smarter choice.
(Use 2FA as well for extra security with minor additional inconvenience.)
Steve
Paul, I’m surprised at you; it seems that you missed the opportunity to comment about the fallacy on which John’s question is based.
John Knops, WalMart isn’t peeking into your mobile device to see what you’re up to, and then refusing you access due to their disapproval of your interests. When you are using THEIR WiFi, in THEIR store, they are more or less acting as if they were your ISP. Your page requests have to go through them. If you request a page that they are blocking – rightly or wrongly – you’re not going to get it. But their knowledge of your requested website exists because you requested it THROUGH THEIR SERVICE… not because of any spying into your device!
Paul Ducklin
Well, the OP implied that the router could somehow access, retrieve or intercept files in or from your device and then they could be decrypted later because encryption is a minor hurdle to crack offline (how I read it, anyway).
Perhaps the implication was that because the router sees your traffic it can extract passwords in transit? But as long as the site at the other end uses HTTPS, you should get a website certificate warning if the router tries to trick you by decrypting the traffic on the way. (The router would need to pretend to be the site you are visiting, which would mean it would need to forge that website’s security certificate, which is harder than it sounds.)
Anonymous
Thanks Paul. I get it now. But has Sophos ever done an article comparing the various pass word managers? Or, are they all essentially the same?
Paul Ducklin
Try searching for “password manager” with the magnifying glass above – there are a fair few good hits to get you started.
We’ve never done a full, side-by-side technical breakdown (that’s a huge and specialised job to do rigorously) but you should find a mix of how-tos, why-so-its, news about bugs and patches, and more, covering the best-known products.
HtH.
Anonymous
One variation of the sshd on a different port. What about configuring sshd to listen on different protocol, as in IPv6? I did this on a virtual server I am running, granted I can’t connect from wherever I want but I can connect from both home and work and that is fine for my usage.
Paul Ducklin
As long as you don’t rely on security through obscurity as a primary defence – e.g. as long as you don’t change to a weird port number to avoid picking a proper password – then being less obvious to the “low hanging fruit among the crooks” won’t hurt. (And when it comes to ssh login attempts could save you a LOT of log entries!)
More on this in Ep. 027 of our podcast (first section [01’25”]):
https://nakedsecurity.sophos.com/2019/04/10/ep-027-honeypots-gps-rollover-and-the-myspace-data-vortex/