Here’s a new twist to sextortion, the cybercrime that gets its name because it melds sex with extortion.
Usually, the approach is to send you an email saying, “We infected your computer with malware, we snooped via your webcam, we monitored your browsing…
…and we recorded you on a porn site, so send us money or we’ll send the recording to your friends and family.”
To reinforce the claim to have remote control over your computer, the crooks often add some personalised content into the email they send you.
For example, the crooks may include a password from one of your accounts, list your phone number, or set the From: line in the email to make it look as though they sent the message directly from your own email account.
Don’t panic if you see “personal” data in one of these spams. The passwords and phone numbers almost certainly come from a data breach – in fact, you might recognise the password as an old one you had to change because the service provider got hacked. And the From: header in an email is essentially part of the mail message itself – the sender can set it to anything they like.)
But there’s a new sort of sextortion message going around, and instead of asking you to pay to have a video file deleted, it’s inviting you to pay to have a corrupt law enforcement official modify your docket so you don’t get charged with a serious criminal offence:
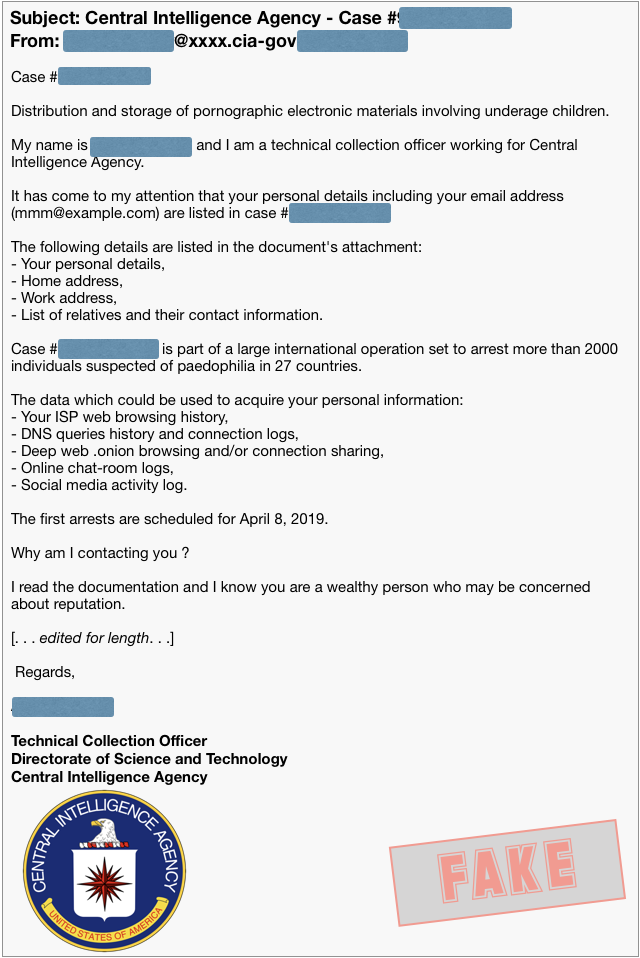
Having set the scene, the allegedly crooked CIA officer says:
I am one of several people who have access to those documents and I have enough security clearance to amend and remove your details from this case. Here is my proposition.
Transfer exactly $10,000 USD (ten thousand dollars – about 2.5 BTC) through Bitcoin network to this special bitcoin address:
3XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
Upon confirming your transfer I will take care of all the files linked to you and you can rest assured no one will bother you.
Please do not contact me. I will contact you and confirm only when I see the valid transfer.
The case number, “agent’s” name and Bitcoin address change every time, but the rest remains the same: send money to buy your way out of a criminal case.
The good news, if you can call it “good”, is that in this instance the crooks are going too far to be believable – while a significant percentage of internet users do watch porn, fortunately only a tiny number are disseminators of child abuse material.
We’ve checked the Bitcoin addresses in a few samples of this scam and have found no evidence of anyone having paid up.
Nevertheless, it’s the thought that counts, and the way that the crooks are thinking here is both intimidating and disturbing – they’re not just insulting you but the CIA too, by presenting themselves as corrupt officials who will take a bribe to alter the course of an investigation.
As always: don’t engage, and don’t reply – not even if you think you have something cutting remarks you want to say to the crooks.
They’re crooks, after all, who are happy to make false accusations, to demean public officials, and to solicit bribes.
Delete the email, offensive though it is, and move on…
LEARN MORE: WATCH OUR VIDEO
(No video showing above? Watch on YouTube.)

STobias
This isn’t new. The first time I saw it was about 10 years ago. They used to turn on the cameras on laptops as well. smh
Paul Ducklin
That wasn’t quite the same thing – those ‘we know who you are’ attacks were generally delivered via a web link (they needed JavaScript in the web page in order to turn on your webcam) that claimed to be officially and overtly levying a ‘fine’, rather than arriving in an email that offered to fudge the evidence behind the scenes.
I take your point that the underlying theme is not new – but the example above does represent a new and current burst of scam emails currently circulating, and that’s the issue we want to draw attention to here.
The best-known example of the web-based attack you mention was probably Reveton:
https://nakedsecurity.sophos.com/2012/08/29/reveton-ransomware-exposed-explained-and-eliminated/
That flavour of attack lasted a few years, until the Reveton gang got busted:
https://nakedsecurity.sophos.com/2013/02/14/reveton-ransomware-gang-arrested-by-spanish-police/
Wil
because the CIA is going to come and arrest you… even if they had a domestic charter, they sure as hell wouldnt warn you ahead of time. this is so full of LOL
Paul Ducklin
I thought that but [a] the whole thing is OTT anyway so a detail like that hardly matters [b] the samples I have were sent to people outside the US, where the letters CIA sound in many ways more likely than FBI [c] the arrests are said to be planned in many different countries – that’s not unusual in global cybercrime busts and would involve each country’s own police service acting on shared evidence.
David Pottage
It would be more convincing if the email claimed to come from middle ranking officer in the local police. Perhaps add a convincing backstory about the officer needing quick cash for a divorce or gambling debits.
What did the CIA press office say about the story?
Michael
I had this happen to me a week ago. Freaked me out in all honesty. They had most my information incorrect but they had my correct IP address and debit card number! That freaked me out the most!
Long story short. Cancelled my card and started looking to see if this has happened to anyone else.