We regularly publish reports about the malicious Microsoft Office documents that are used in attacks. These maldocs are created by criminals who use tools called “builders” that automate the process of embedding any of an a-la carte menu of exploits into the maldocs. Studying these builders often reveals trends that victims are likely to see in the malspam they receive.
The most recent updates to these builders revealed a drastic change: The makers of these builders replaced both the old exploits — and the old exploit builders themselves — with next-generation offerings.
The old, established, dominant “brands” of maldoc builder tools (like Microsoft Word Intruder, Ancalog and AKBuilder) were abandoned, and these previously-dominant builders have been completely wiped out of the ecosystem. One of the most prominent newcomers is The Old Phantom Crypter. Our research paper details the characteristics of this kit and the malicious documents created with it.
We had observed that, as last year came to a close, maldocs created by the top 4 exploit builders were responsible for over 75% of all malspam attacks.
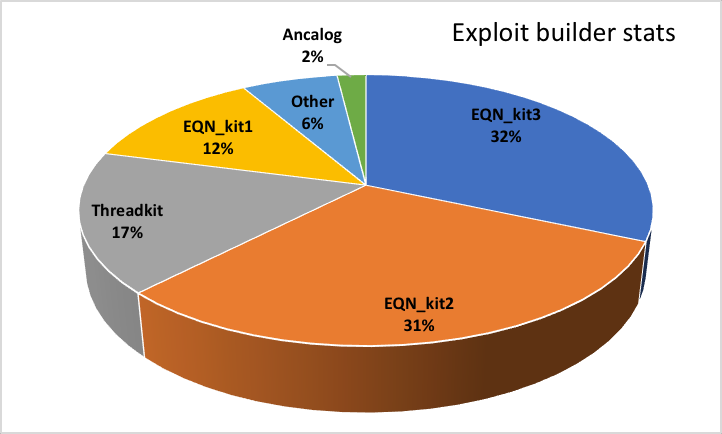
We had previously designated one of the most prevalent kits EQN_Kit2, because we didn’t know its “street name.” Now we know that this kit calls itself The Old Phantom Crypter. This kit generated samples with very distinguishing characteristics and has been very actively used (and updated) ever since.
The Old Phantom Crypter
For the past 11 months, we have seen an increasing flow of documents generated by EQN_Kit2, but we hadn’t been able to identify the source behind it. Until we ran into a black-market tool called The Old Phantom Crypter – then we realized that this is the mysterious kit that generates all these documents.
This kit a two-in-one solution. It originated as a PE cryptor, but later on additional functionality was integrated into it.
This additional functionality provided the means to deliver the protected executable by various methods, including Microsoft Office exploits.
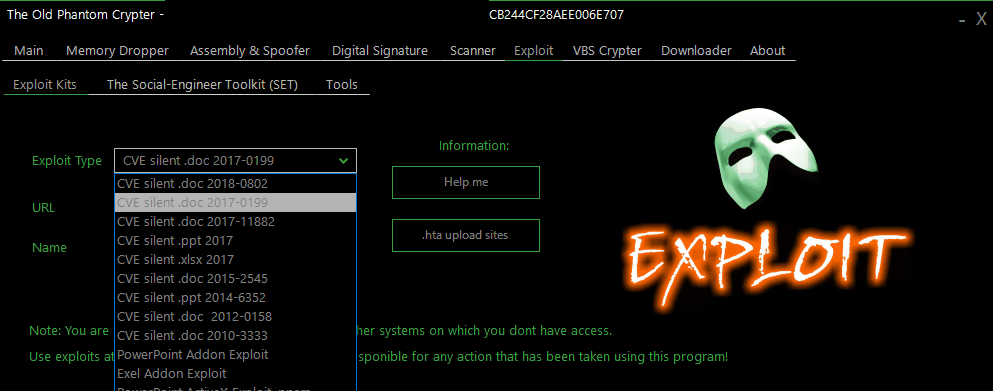
The license for this kit can be purchased via the main distribution web page for $199 per month, which positions it in the league of the most expensive builders in the market.
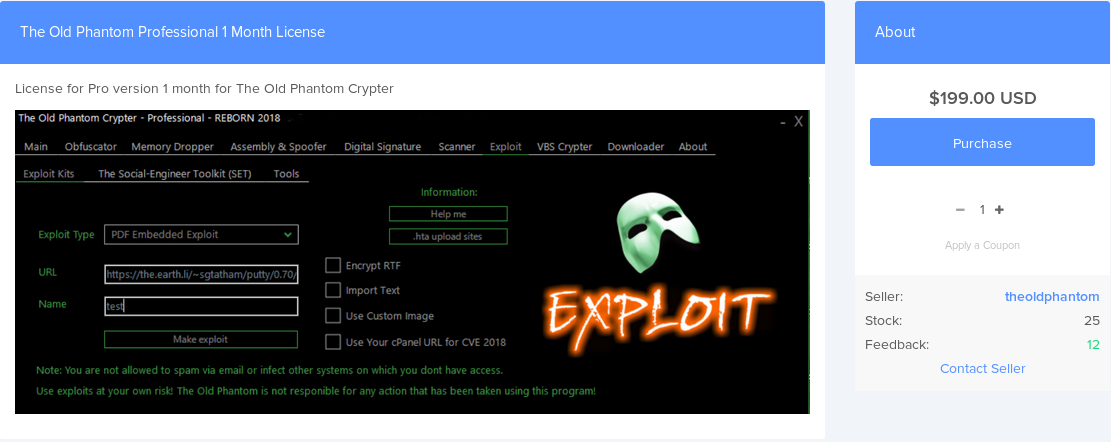
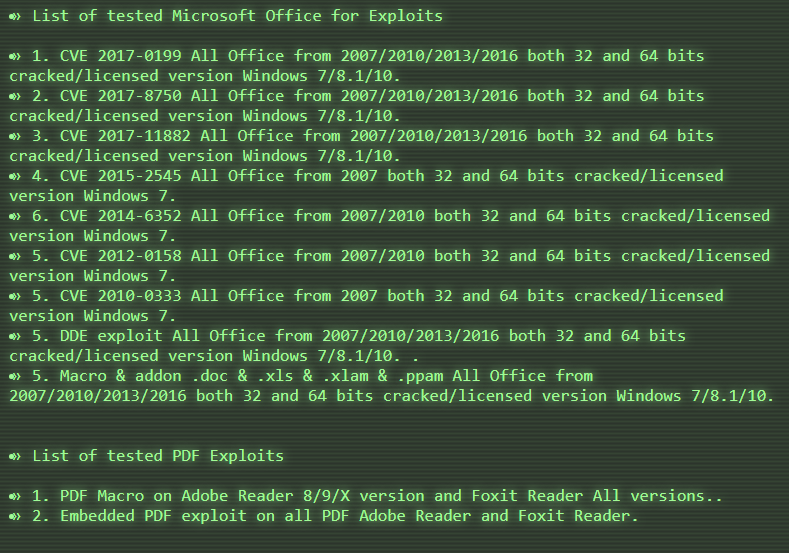
The builder supports a wide selection of Microsoft Office exploits, from the archaic CVE-2010-3333 to the recent CVE-2017-11882 Equation Editor exploit:
The builder itself is a .Net executable hidden form the analysis by using the Enigma Protector to hide the internal details. Enigma is a very powerful protection system.
It is also one of the few that use a software taggant mechanism that helps identify the malicious uses of the protector. It embeds a unique identifier in the protected executables; We can also use that marker to track the use of the product.
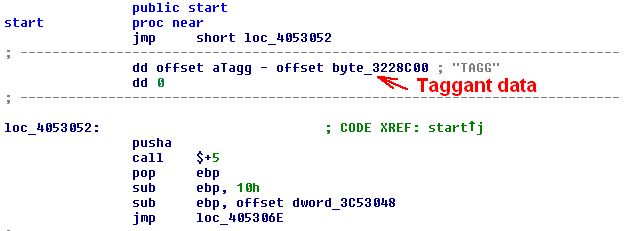
In case of the Old Phantom Crypter we found over 50 versions of other, totally unrelated software product protected by the same Enigma client. It is a possibility that the author of The Old Phantom is also the author of all other products. It is, however, a much more likely explanation that he uses a pirated version of Enigma, shared among many players in the underground scene.
Once the protection is stripped off, the unpacked program stores a collection of skeleton files as resources. These skeleton files serve as building blocks when the actual exploit document is generated.
This approach is not unique among exploit builders: Ancalog used a similar concept of skeleton templates for the exploits. In fact, some of the templates used by The Old Phantom are taken from Ancalog, to keep the legacy alive. There is no similarity in the code itself, but it is quite possible that the overall design was inspired by Ancalog.
Customers and victims
Usually we don’t have insight into the customer base of a criminal software tool – those are sold on underground marketplaces, and both the seller and the buyers are interested in keeping their anonymity. However, due to a (possibly unintended) information disclosure failure we could get a reasonably good insight into the typical customers of the tool.
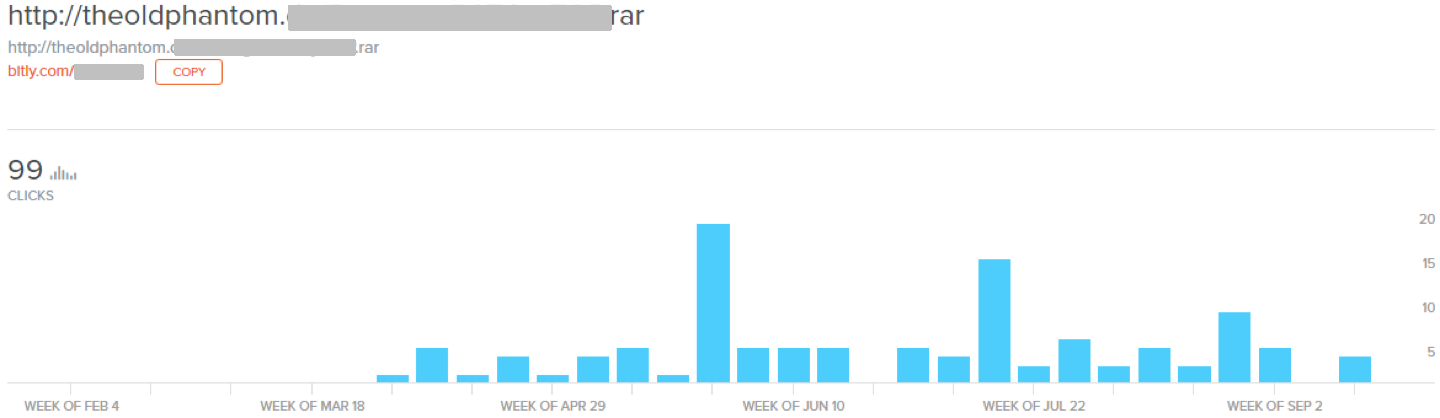
From this we can conclude that the distribution may have started mid-March 2018, which matches the first large scale appearance of samples generated by the builder. Additionally, we can estimate the number of customers to be around 100.
Further data is available about the locations of the people who downloaded the tool (assuming they didn’t use a VPN).
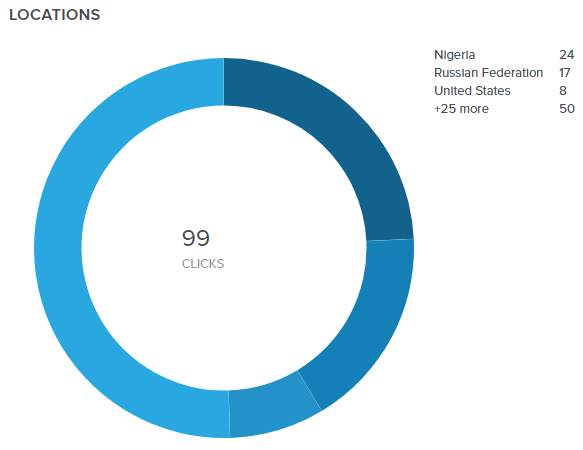
There is no surprise here, the major users of the builder are the usual suspects: cybercriminals based in Nigeria and Russia.
Our 2018 Q3 stats also revealed the major targets of the infection campaigns powered by Old Phantom generated Office documents, which are mostly victims from the USA and EU.
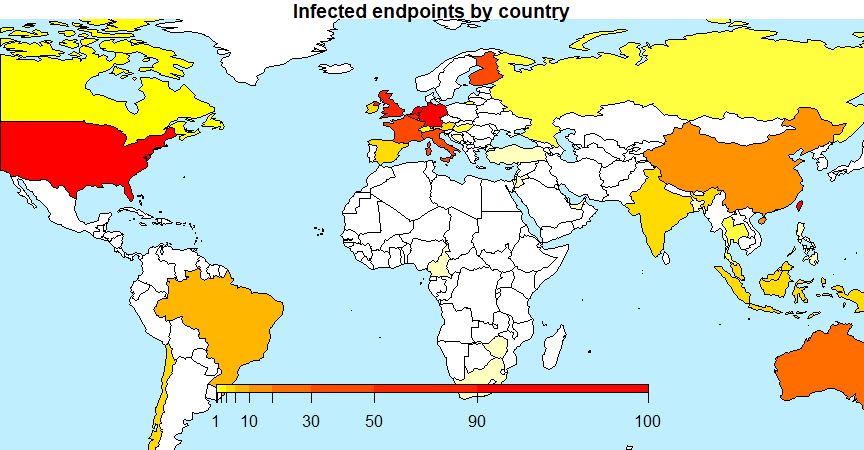
With reasonable confidence we can say that the Old Phantom Crypter is mostly used by a few dozen Nigerian and Russian criminals for attacking victims in North America and Western Europe.
Further details on the Old Phantom Crypter can be found in our technical paper.

Leave a Reply