If you ever used dial-up networking to access the internet, you probably remember it mostly for being cumbersome and slow.
But it was also astonishingly insecure, because your computer – which was probably running Windows 95, Windows 3, or even good old DOS – ended up with a public-facing IP number, connected straight onto to the internet.
Other users out there could, literally and figuratively, reach out and probe your computer directly.
In recent years, however, we’ve got used to the idea that home computers don’t get plugged directly onto the internet – they typically connect through a router instead, and it’s the router that’s plugged into the internet connection.
Indeed, it’s tempting to assume that home routers came about specifically to address the security risks inherent in connecting laptops and other home devices straight onto the internet…
…but the truth is that the main reason for having a home router is to support multiple devices through connection sharing.
That means your ISP only needs to hand out one IP number per household, rather than one IP number per device.
Connection sharing explained
The “trick” used for internet connection sharing is called NAT, short for Network Address Translation, and it’s a way to allow a single home router to divide up your internet connection automatically between any number of devices.
The NAT software on your router keeps track of which internal devices have made what outbound network requests to which external servers, and sorts out the inbound replies so that they get back to the right place.
But NAT doesn’t work automatically for inbound traffic.
If a brand new network request arrives from the outside asking to be sent to your mail server or your web server, for instance, there’s no way for your router to know in advance where to redirect that packet inside the network.
NAT therefore has the handy side-effect, in theory at least, of boosting security – by default, your internal devices can’t be probed directly from the outside.
Unless and until you configure your router to tell it where and how to redirect inbound connection requests, NAT basically acts as a firewall that causes incoming connections to fail harmlessly.
Invisible by default?
It’s easy to assume that any internal devices behind your router are “invisible by default”, and thus that anything you connect to the private part of your network is safe from discovery and attack – including your computers, phones, tablets, file servers, thermostats, webcams, printers…
..and your Chromecast media streaming devices.
In practice, however, NAT alone simply isn’t enough to keep the crooks out.
Firstly, some routers come with externally-facing services of their own, such as a web interface, turned on by default.
In this case, crooks can attack your network by probing for bugs on the router itself.
If they can figure out how to run unauthorised commands on your router, they can reconfigure the router to enable inbound access for future attacks.
Secondly, some routers come with a system called Universal Plug and Play (UPnP) turned on by default.
UPnP is a protocol that devices inside separate, NATted networks can use to identify and communicate with each other, with their respective routers co-operating to open up the necessary connectivity and packet forwarding automatically.
Thirdly, many routers end up with inbound network ports opened up and then forgotten about.
As a result, crooks can automatically find and potentially exploit services that are accessible through holes that aren’t supposed to be there.
Unfortunately, probing for unexpected remote access holes is as easy as running through a list of IP numbers one by one (or million by million) and seeing what happens if you try to connect.
Sometimes, you will not only find out that a particular port is open on a particular computer, but also receive a snippet of data back that gives away what sort of service is listening, even if the port number isn’t one usually associated with that service.
For example, email servers listen by convention on port 25, and web servers on port 80, but it’s easy enough to spot those services if they’re “hidden” on non-standard port numbers.
In the example below, we’ve probed and found a mail server on port 10025 and a web server on port 10026:
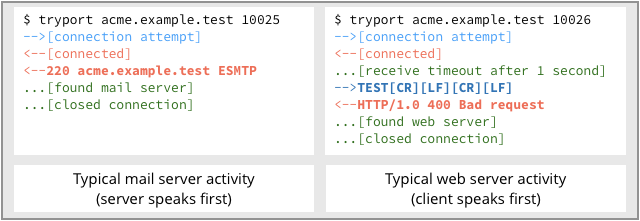
For better or worse, search engines exist that repeatedly sweep through the internet, keeping track of which IP numbers had what network ports open, and what service, if any, seemed to be listening for connections.
By querying these search engines (two well-known ones are Censys and Shodan), would-be hackers can download ready-made lists of networks to start probing – the hackers don’t even need to do the initial reconaissance, known as port scanning, themselves.
Scanning for mischief
Sadly, some “researchers” can’t resist using port scans for mischief, thinly disguised as attempts to make a serious security point.
For example, in December 2018 a hacker going by the name TheHackerGiraffe decided to “warn” networks with internet-connected printers by printing out a “notification page”, entirely without permission.
The notification message included an advert for a well-known, high-traffic YouTube video blogger called PewDiePie.
PewDiePie, real name Felix Kjellberg, wasn’t the perpetrator of the hack, just the unexpecting recipient of an “endorsement” by the hackers.
At the start of 2019, TheHackerGiraffe couldn’t resist having another go at incorrectly-configured networks, probing for and finding tens of thousands of publicly-visible Chromecast devices.
This time, it seems the Giraffe was aided and abetted by an online chum going by the name j3ws3r (whether that’s an anti-semitic slur or just hacker-style spelling of the word “user”, where the j is pronounced as y, is an open question).
According their own website, the pair identified more than 72,000 vulnerable Chromecast and Google Home devices:

They also unlawfully played “warning videos” on 65,000 of the Chromecasts, once again promoting PewDiePie:

(We’ve redacted the link in the video – when we tried it, it was a rickroll, redirecting to a video of singer Rick Astley performing Never Gonna Give You Up.)
What to do?
- Turn off UPnP on your router. It’s been a recipe for trouble for many years, and you almost certainly neither want nor need to open it up to the outside world.
- Check what network ports are opened up on your router. If you see 8008, 8009 and 8443 open, then any Chromecasts you own are probably exposed. But any open port could spell needless danger, so close any port that you aren’t 100% sure you need to keep open.
- Don’t go around poking sticks into other people’s devices. It’s neither witty nor lawful to access other people’s computer equipment without permission.
If you’re blindly playing videos on random people’s Chromecasts, or printing out unsolicited messages on their printers, then you don’t have permission, and you jolly well know it.
Even if your intentions are good, please don’t mess with other people’s stuff – you might end up regretting it, as the Giraffe himself now seems to do, if a recent post to Pastebin is to be believed:
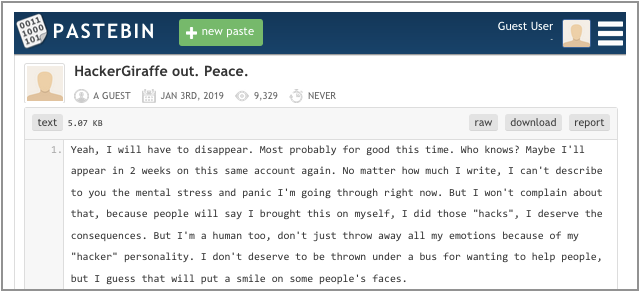
Yeah, I will have to disappear. Most probably for good this time. Who knows? Maybe I’ll appear in 2 weeks on this same account again. No matter how much I write, I can’t describe to you the mental stress and panic I’m going through right now. But I won’t complain about that, because people will say I brought this on myself, I did those “hacks”, I deserve the consequences. But I’m a human too, don’t just throw away all my emotions because of my “hacker” personality. I don’t deserve to be thrown under a bus for wanting to help people, but I guess that will put a smile on some people’s faces.
Chromecast image from Wikimedia commons.

Mahhn
lol “when we tried it, it was a rickroll”
A lot of people are lucky these kids weren’t destructive.
Anonymous
lol! I forgot about the rickroll! Good times…
Simon McAllister
It’s 2019 and some devices still come with UPNP and webadmin from external enabled by default!!!
It’s 2019 and some ISP’s block some ports e.g. for NetBIOS & SMB whilst leaving other, equally dangerous ports unblocked e.g. Virgin Media and mDNS (who then send confusing letters to customers).
Although there are plenty of port scanners out there, I’ve mostly used ‘Shields Up” by Steve Gibson for about 20 years to monitor what’s available.
And the only other point I would make is that; whilst blocking unnecessary incoming connections is good security practice, let’s not forget that internal devices that are allowed to connect outbound can still pull data in to your device/network. E.g. my Samsung TV’s are blocked from connecting outbound to everything apart from YouTube servers. I temporarily jump to my guest Wi-Fi for firmware updates.
Whether your using a Chromecast or not, this article is a good heads up.
PS: No, I probably wouldn’t like it if my devices started showing content that someone else threw up, but… I would certainly prefer to know that there was a security issue that way, before something more sinister were to happen.
Reaching for my coat :)
Jon H
What utility is that being used to test? I’ve never seen “tryport”
Paul Ducklin
It’s really there only as a simple visual representation of how port probing might work. The tryport ‘utility’ itself is just a tiny Lua script of mine that connects, probes for a reply, and matches any response against a short list of likely protocols being spoken at the other end (SMTP, HTTP, SSH, TLS).
Sara
Google support told me I had to make the following changes to my router settings in order to get my Chromecast (we have 2) to work:
Enable: Universal Plug and Play (UPnP), multicast, Internet Group Management Protocol (IGMP)
Disable: AP/client isolation, virtual private networks (VPNs), proxy servers, IGMP Proxy
I don’t know really what those changes are going to do, but they say it won’t work otherwise.
Epic_Null
Sad, they don’t acknowledge the principal of minimum privelages
Paul Ducklin
I can understand UPnP *inside* your network, but I guess that the easiest way to make that work is just to “turn it on altogether”, which is not (as @Epic_Null points out) very least-privilege-friendly.
As for client isolation, that’s a neat and easy feature to make your router keep your devices apart on the network – this means if you let guests on your Wi-Fi and they’re infected with malware, their computers can’t snoop on the rest of your network, which is useful.
Presumably the easiest way to tell your router that your devices should all be able to see the Chromecast so they can stream to it is just to let everything device see every other device – sort of like using an AR15 to punch a hole in a tin of soup. Reminds me of the bad old days when software vendors told you to “turn off your anti-virus when running our application” because it was the path of least resistance – a form of technical debt that made you choose functionality over security.
RH
Always love a good rickroll.
Mainstream media deserves to die
How is it a thinly veiled disguise for mischief? They did nothing harmful, the people that were notified by them are probably now taking precautions to be more secure.
tkellerkingschoolscom
Thanks for the click bait. This story is misleading
Paul Ducklin
Not sure quite how you were misled… the article [a] describes a recent hack against tens of thousands of Chromecast devices that were open to the internet; [b] explains some of the ways that TCP ports inside your network can end up reachable from outside; [c] advises you what you can do to reduce the external accessibility of your internal devices.
Perhaps you were disappointed not to read about something more elborate and more deeply hackery, such as an attack that could jailbreak Chromecast devices and exfiltrate data from a TV…
…fortunately, not this time.
Brian Gunn
The Chromecast requires UPnP to be enabled on the router. That send to be the biggest problem here. When I turn off UPnP, my phone can see the Chromecast but can’t connect to it. That finally got me to unplug the Chromecast and stop using it.
[URL removed]
Sandra Garcia
I think it’s funny as hell. I have two Chromecasts and my view may have been different had mine been the devices in question, but I still see more mischief than any intent to harm. What they did was call attention to some potentially really bad consequences of improper security and the higher ups didn’t like being called out on it.
igarden2
Could j3ws3r be interpreted as ‘juicer’ ?
Anonymous
Aye that’s what I was a-thinking.
Paul Ducklin
IIRC, the owner of the account himself suggested the reading “user” (J to be given the pronunciation used in almost every Germanic language other than English, and 3 used for E).
M Limo
Okay so the article is good but where is the part where you tell us what programs to run to keep our inbound traffic monitor what programs do we download for Android for Windows to keep our computers from being infiltrated on the inbound side what programs do we use to keep traffic from getting in etc etc
Paul Ducklin
This article is mainly concerned with configuring your router to keep your Chromecasts off the open internet, so it isn’t meant to be a review of endpoint firewall products.
Both Windows and Android have build in “packet shielding” features; if you want additional security you can add a third party product to watch for dodgy behaviour (you will find a link to Sophos’s free security software for various systems including Android, Windows, Mac and iOS just underneath the main text of the article).
As an earlier commenter noted, blocking inbound connections alone is not enough – a lot of malware gets in because you make an outbound connection on purpose (e.g. to read your email or browse a website), download stage 1 of the malware by mistake, and it then connects out from inside to “update” itself…
Allan Reiman
Chromecast requires UPnP. This article seems to be less than worthless, since it tells me to turn off UPnP to protect my chromecast, but chromecast will stop working if UPnP is turned off. If there is a workaround, tell us about it.
Paul Ducklin
You don’t need to allow UPnP traffic into/out of your network from the internet, though… do you?
Epic_Null
I honestly would not be surprised. You have to turn location on for the home to “find nearby wifi connections”. Yes, I know exactly how rediculous that sounds.
Simon McAllister
My view, Allan, is that Google should provide the workaround.
I don’t understand why a Chromecast requires UPnP enabled on the router. There are plenty of security issues with UPnP, which have been resident since it emerged – searching google for ‘chromecast upnp’ first shows the issue that this article highlights as well as many other ‘heads ups’. Steve Gibson (a very well respected computer/Internet security expert) created a utility called “Un-plug n Pray” to easily disable UPnP on Windows XP when it launched (back in the day when home users’ firewalls were mostly just routers performing NAT).
UPnP was designed to minimise the technical work required to get connectivity for devices – and was not designed for use over the Internet. If you buy a device that you want to run on your private home network AND want to connect to it from outside, you would ‘open’ or ‘forward’ ports. You would need to know ‘which’ ports and ‘how’ to do this on your router. UPnP does this for you (if enabled). But that simplicity introduces security concerns; malware or any rogue application ‘could’ also open ports on your router – then who knows what’s flowing in an out.
For what it’s worth, XBOX’s and Playstations claim to need UPnP (so my kids tell me) but they work fine with UPnP OFF on my router.
So, why does a Chromecast device need to use UPnP to setup and accept incoming connections? Forgive my naivety, but aren’t they just making outbound connections to stream data in? Much the same as when watching a video on Youtube website?
Mike T
I have two chromecasts that work perfectly with upnp switch off on the router. I have always switched off upnp and never had a problem with anything working. Upnp can be a potential risk to business – left that old server running to test web pages? It may be opening up ports on your router!
Pizza
Not really, works great for me with UPnP disabled (always been, always will). You can even put it in a different subent/VLAN using mDNS.
Max
That’s not really related to chromecast then, is it? I mean, if your router is misconfigured any device may be exposed. So its a router issue.
Paul Ducklin
Well, the article was written because of widespread abuse of open Chromecasts, so it’s related to Chromecast on that account… we do make clear that our advice is good for this particular hack *and many other potential attacks*.
As several other commenters have pointed out, Google’s own advice for “how to make Chromecast work” does seem to include advice that could lead to problem #3 above, where we warn: “…Thirdly, many routers end up with inbound network ports opened up and then forgotten about. As a result, crooks can automatically find and potentially exploit services that are accessible through holes that aren’t supposed to be there…”
So you are right – this is a router issue. But I think we are right too, and the headline serves a useful purpose – this variant of the story is related to Chromecast.
Chris
Holy shit, you guys really buried the lede in this article!!
Paul Ducklin
Well, it’s not meant to be news, it’s meant to be a security-centric discussion of what-how-where next that leaves you with a better understanding of the issues.
Anyway… sounds as though you found the “lede” (to speakers of British English, I think that is American journo jargon for “headline topic”) so thanks for sticking with the article -)
Pino
uPnP required? I Disabled uPnP in my router, verified it with grc.com. My Chromecast is still working fine and I can still stream to it and control it with my phone.