SophosLabs has uncovered an unusual click fraud campaign in which malicious Android apps masquerade as being hosted on Apple devices to earn extra rewards.
Advertising click fraud, where a malicious app or process bombards websites with bogus traffic to earn advertising revenue, is a rapidly growing form of cybercrime on mobile and can be hard to spot.
This may go some way to explaining why Google’s Play store failed to detect the malicious design embedded inside a total of 22 apps which kicked off their click fraud campaign in June this year.
Named Andr/Clickr-ad by researchers, the malicious apps were downloaded a total of two million times with one, Sparkle Flashlight, accounting for half of this.
It’s the second time that SophosLabs has discovered malicious ad fraud apps on Google Play, after noticing the separate Andr/Guerilla-D ad fraud campaign lurking inside 25 apps in March and April.
Fake Apple traffic
What sets Clickr-ad apart from previous examples is its sophisticated attempt to pass off much of the traffic the apps generate as coming from a range of Apple models such as the iPhone 5, 6 and 8.
It does this by forging the User-Agent device and app identity fields in the HTTP request. However, it is careful not to overdo the technique by allowing a portion of the traffic to use identities from a wide selection of Android models too.
The Apple fakery is about making money – advertisers pay more for traffic that appears to come from Apple devices than from the larger volume of more socially diverse Android ones.
The difference is probably only small fractions of a penny but for a business built on click volume, those fractions add up over time.
The ad fraud boom
Ad fraud malware must constantly update itself to remain useful to its makers.
To maximise revenue, Clickr-ad’s command and control (C2) changes the ad profile every 80 seconds and downloads new SDK modules every 10 minutes.
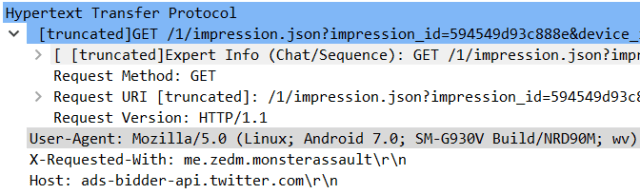
The above example shows the malware posing as a Samsung Galaxy S7 to abuse Twitters’ ad network.
As one might expect from click fraud, a primary concern is stealth: Clickr-ad must hide what it’s doing from the Android user. Writes SophosLabs’ researcher Chen Yu:
Malicious ad calls are made in a hidden browser window, inside of which the app simulates a user interaction with the advertisement.
What to do?
The effect of this kind of app is to drain the device’s battery, generate data traffic users might be charged for, and generally bog down the device by constantly clicking on ads.
Because there is nothing to stop the malware’s creators from installing other malware on devices, SophosLabs’ decided to classify it as malicious rather than merely unwanted.
The apps were removed from the Play store in the week of 25 November but because their C2 infrastructure remains in place it’s likely they will continue clicking away until they are removed by device owners.
Simply force-closing the app won’t do the trick because it can restart itself after three minutes – a full uninstall is needed.
An extra precaution would be to conduct a full factory reset after ensuring all data has been synchronised to Google’s cloud.
To reduce the possibility of a return, we recommend running mobile anti-malware – such as the free Sophos Mobile Security for Android, for example.
Conclusions
Number one, although it’s mostly safer to download apps from the Play store than anywhere else, it doesn’t guarantee that what you just installed isn’t malicious.
Number two, mobile click fraud isn’t going to go away, indeed it will likely continue to grow as a problem. It’s simply too lucrative and Google clearly isn’t on top of the problem despite numerous initiatives to tighten app checking. What’s more, the beauty of Clickr-ad is that it’s a whole platform for ad fraud which could be deployed inside other apparently innocent apps.
Finally, while SophosLabs researchers haven’t detected this malware in Apple’s App Store, it should be noted that iOS apps from the same developers were found on the iTunes store minus the click fraud functions.
The affected apps:
| Package Name | Title |
| com.sparkle.flashlight | Sparkle FlashLight |
| com.mobilebt.snakefight | Snake Attack |
| com.mobilebt.mathsolver | Math Solver |
| com.mobilebt.shapesorter | ShapeSorter |
| com.takatrip.android | Tak A Trip |
| com.magnifeye.android | Magnifeye |
| com.pesrepi.joinup | Join Up |
| com.pesrepi.zombiekiller | Zombie Killer |
| com.pesrepi.spacerocket | Space Rocket |
| com.pesrepi.neonpong | Neon Pong |
| app.mobile.justflashlight | Just Flashlight |
| com.mobile.tablesoccer | Table Soccer |
| com.mobile.cliffdiver | Cliff Diver |
| com.mobile.boxstack | Box Stack |
| net.kanmobi.jellyslice | Jelly Slice |
| com.maragona.akblackjack | AK Blackjack |
| com.maragona.colortiles | Color Tiles |
| com.beacon.animalmatch | Animal Match |
| com.beacon.roulettemania | Roulette Mania |
| com.atry.hexafall | HexaFall |
| com.atry.hexablocks | HexaBlocks |
| com.atry.pairzap | PairZap |

Mahhn
It’s really a shame (and maybe a crime) that google doesn’t notify people when an app they downloaded is identified as malicious. Heck, they don’t even have a publicly available list to see if you got infected from the playstore……
kurt
What should Ad buyers do? Maybe keep ads on google’s search engine only to avoid the click fraud on third party sites and apps.
🇨🇦 SkepticalScott (@ScottDouJohnson)
I like the fact you guys will name the apps. Other sites will not do so.
🇨🇦 SkepticalScott (@ScottDouJohnson)
I gave the mentioned app a try. Slowed the phone down too much. Went back to Bitdefender.
addermc
It seems like the more I read, the more I’m confused. Some”tech” sites say you don’t need an antivirus app for Android cause the device protects itself, basically. Then I read about different virus types being discovered and how you should install an antivirus app, like such and such. Which always is a sponsored app link. So I’m still no closer to figure out what to do…..
Paul Ducklin
We recommend a third-party anti-virus – and not because we have one. In fact, we have one because we think it’s a good idea, not the other way round. Because Google Play only goes so far and malware turns up fairly regularly. (There are so many apps in there that Google doesn’t acutally test each one and vet it thoroughly – the process is automated and mistakes do happen.)
You should find a link in the Free Tools section. It’s free and doesn’t have ads if you care to try it. Anti-virus (treal-time and scan on demand), web filtering and more.