Cybercriminals have returned to old-school manual hacking tactics to boost the efficiency of targeted extortion, according to research conducted for the SophosLabs 2019 Threat Report.
Ransomware attacks are nothing new, but well known examples like CryptoLocker or WannaCry have tended to be opportunistic and indiscriminate. To penetrate their targets they rely on simple automation, such as boobytrapped attachments sent to a large number of prospective victims via email.
However, the most eye-catching innovation seen by Sophos during 2018 looks more like the opposite of automation – manual control.
Deploying an attack by hand takes time and doesn’t scale well, but it is hard to detect – because it doesn’t necessarily follow a predictable pattern – and hard to stop – because an attacker can adapt as they go.
SophosLabs sums up the advantages of the hands-on approach:
With targeted attacks, the behaviour is inherently unpredictable, and the attackers can respond reactively to defence measures that, at first, thwart them from accomplishing their goal.
The perfect case study in how successful this modus operandi can be is the SamSam ransomware, whose evolution Sophos has been tracking since 2015.
Earlier this year, Sophos researchers discovered that a group or individual has used SamSam to successfully extort $6 million (£4.6 million) out of victims in the two and a half years to June 2018.
After operating on a smaller scale for the first year, in December 2016 the group or individual seems to have realised that its package of efficient ransomware, targeting and manual attack had legs.
Careful targeting
SamSam succeeds over more widely deployed ransomware because of the size of the ransoms the attackers ask for, which dwarf the more opportunistic demands of established ransomware.
SamSam extorts up to $50,000 per attack, a couple orders of magnitude more expensive than the far more common GandCrab ransomware, which only demands a ransom of $400.
Message: the sum is extraordinary because the level of compromise is too, and that’s down to the manual nature of the attack.
Most likely, the victim was chosen because they use the Windows Remote Desktop Protocol (RDP), making them accessible from the internet, and breached by the brute-forcing of a weak password.
Having prised the door open, the attackers run a tool such as Mimikatz designed to sniff the credentials for domain controllers when admins log in.
The attackers can then use system administration tools to map out the victim’s network, disable poorly protected security software and distribute the SamSam encryption malware to as many target systems as they can reach. Cleverly, when the ransomware is finally executed, it happens at night, when few security staff are around to react to the fast-moving tidal wave of encryption.
SamSam’s personal treatment extends as far as the decryption too: each victim gets their own dark web site where the SamSam authors offer a perverse form of technical support.
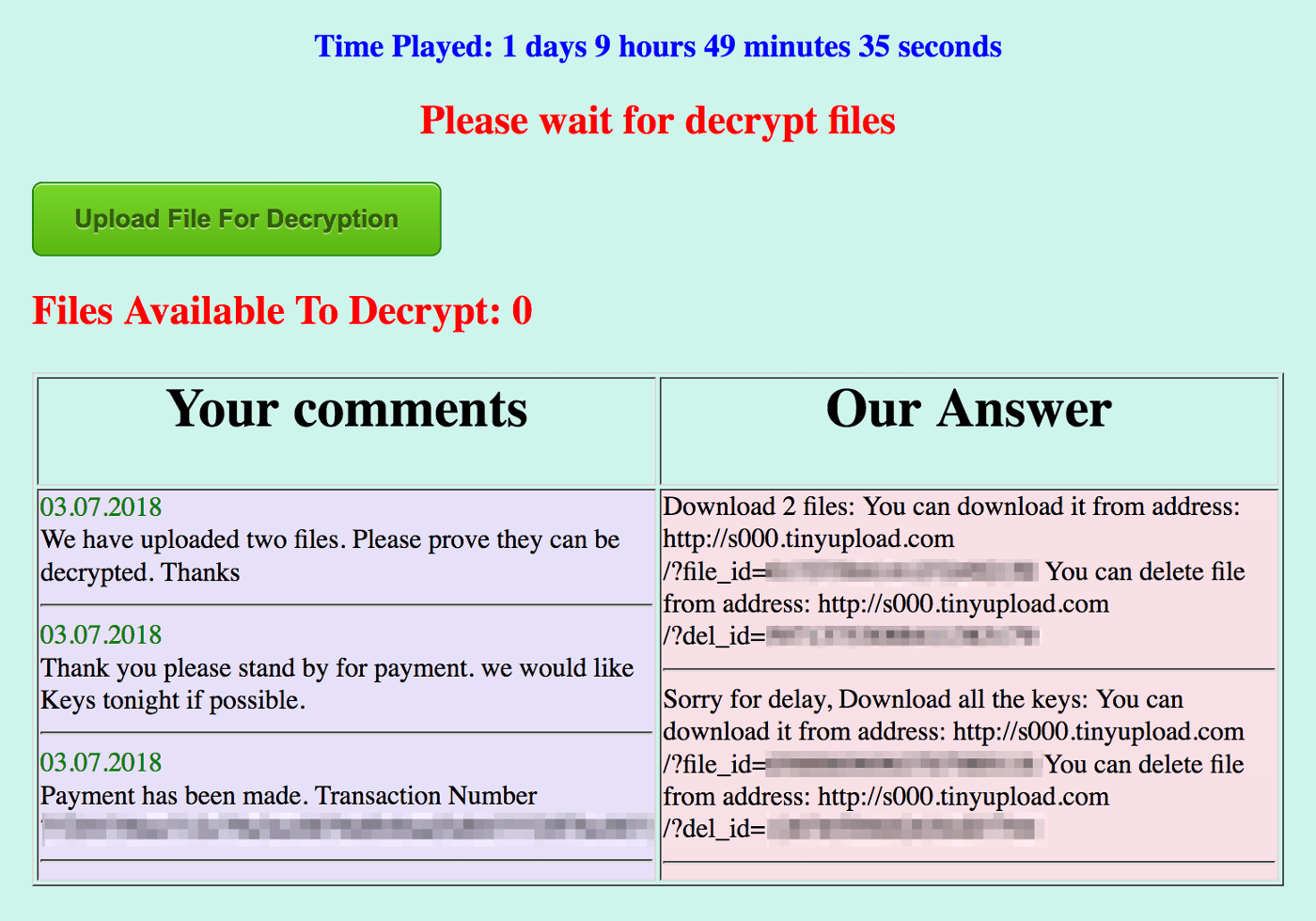
SamSam isn’t the only ransomware used in this targeted manner. Attacks by the elusive BitPaymer malware have been accompanied by ransom demands as high as $500,000, while Dharma appears to be used by multiple groups targeting small businesses.
Their continued success of targeted ransomware, and the recent emergence of copycats like Ryuk suggest the trend for targeted attacks is set to continue through 2019.
Naked Security has already produced extensive advice on defending against SamSam and its ilk, with the first and most important job being to lock down Windows RDP.
SamSam is the devil waiting to take the hindmost, so simple precautions can keep network security teams nearer the front of the chase.
You can read more about targeted ransomware, and how SamSam differs from similar attacks such as BitPaymer, Ryuk and Dharma, along with much more insight from the team inside SophosLabs in the SophosLabs 2019 Threat Report.


Wilderness
Crime is such a colossal drain of resources that might have been put to productive use.