Chrome 70 comes out today.
Most people who use Google’s popular browser will receive the update, and either won’t realise or won’t especially care about the changes it contains.
Next Tuesday, Firefox 63 will be released, and much the same thing will happen for users of Mozilla’s browser.
But one of the changes common to both those products, which have a huge majority of the market share amongst laptop users, may matter very much to a small but significant minority of website operators.
Chrome 70 and Firefox 63 will both be disowning any web certificates signed by Symantec.
From this month, anyone with Chrome or Firefox who browses to a web page “secured” with a Symantec certificate will see an unequivocal warning insisting that the site is insecure:
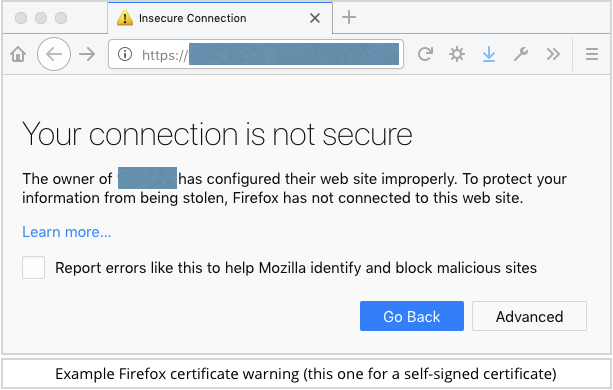
Unless your website is really mainstream and well-known, you should assume that almost all users confronted with a warning of this sort – especially in this surveillance-conscious age – will simply hit the back button and try the next website in their search results.
Simply put: we’ve been teaching people not to ignore certificate warnings for years; browsers have made it harder and harder to sidestep the warnings, in an effort to make users take notice; and people have been taking notice.
Anything that suggests a website might be up to no good – even if the warning is down to a configuration mistake rather than any actual malevolence – is a giant turn-off to prospective visitors, and causes the search engines to mark you down.
There shouldn’t really be any Symantec certificates left in use – Symantec sold its web certificate businesses (it owned several well-known brands) to a company called DigiCert back in 2017, and DigiCert has been reissuing old Symantec certificates since then.
Anyone with a not-yet-expired Symantec certificate can replace it for free – so if you’re one of them, don’t leave it any longer to do your renewal.
You can expect a visible downturn in traffic if you don’t.
Update. An alert reader (see comments below) pointed out that Mozilla recently deferred this change until “later in the year” to give everyone a bit more time. As Mozilla says, “It is unfortunate that so many website operators have waited to update their certificates, especially given that DigiCert is providing replacements for free.” [2018-10-16T17:40Z]
Here’s a quick overview of how we got to this point…
Why do we have web certificates?
Web certificates put the S in HTTPS, and the padlock in your browser’s address bar.
Without HTTPS, anybody could clone anyone else’s website at any time, making it look indistinguishable from the real thing except for booby-trapped or fake content here and there, and you’d be hard pressed to tell the difference.
But when an HTTPS connection is set up, your browser receives a web certificate up front that vouches in some way for the fact that the site really is owned and operated by the company it claims to represent.
Why do we need to get web certificates signed?
Anyone can create a web certificate, and they can put in any ownership information they like.
This is known as a self-signed certificate – jargon that means you are vouching for yourself.
If you only expect three or four people ever to use your site, you could prove to them individually that you really were the person who created that certificate – you could meet up in person, for example – and thereby build a small but strong web of trust.
But that sort of approach is no good if your goal is to attract thousands or hundreds of thousands of visitors from all over the internet, because you can’t possibly reach out in person to all of them in advance.
The solution is to get a company known as a CA, short for Certificate Authority, to vouch for you by signing your web certificate using their web certificate.
Before the CA vouches for you, it’s supposed to do some basic checks to satisfy itself that you really are authorised (and able) to operate the website that the certificate is for.
Basic CA checks, such as those down by the free CA Let’s Encrypt, are limited to testing that you are able to log into and administer the relevant site. For example, before signing your certificate, the CA may tell you to add a random, unpredictable string of text to a new and specially-named page on your site. If the relevant text appears in the right location within a reasonable time, the CA will assume you have full access to the site and will sign your certificate. More expensive certificates, denoted EV for Extended Validation, require additional checks such as looking at company registration records, validating published contact details with real phone calls, and requesting physically signed documents. In short, CAs aren’t supposed to sign certificates only on the say-so of the submitter.
Who vouches for the CAs?
A certificate signed by a CA still isn’t enough – your browser itself needs a list of known-good CAs that it’s prepared to trust to sign certificates for the websites you’ll be visiting.
So every browser includes a list of trusted “root CAs” whose certificates it will accept.
Some browsers, such as Edge and Safari, rely on a list of trusted roots supplied by the underlying operating system; Chrome on Windows and macOS uses the operating system’s certificate store, plus its own list of tweaks to disavow CAs that Google no longer trusts; Firefox on all platforms and Chrome on Linux use Mozilla’s curated list of known-good CAs.
In simple terms: you create an HTTPS certificate to vouch for your website; you choose a CA to vouch for your certificate; and your browser vouches for the CA.
This is what’s known as a chain of trust, and the browser (or your operating system’s certificate store) is where the chain is anchored.
What happens if a CA goes rogue?
If a CA loses the trust of the community, then the ultimate sanction is for the community to agree to remove that CA’s own certificates from the list of known-good roots.
That’s quite rare, because the side-effect of ejecting a CA’s certificate from every browser is that every certificate ever signed by that CA is implicitly disowned, so every website using a certificate from that CA immediately becomes untrusted.
That’s what is about to happen to Symantec certificates in Chrome and Firefox.
Why is this happening now if Symantec sold its CA business last year?
The community became dissatisfied with Symantec’s CA business over a lengthy period.
The company had acquired a number of CA sub-brands (Thawte, GeoTrust, and RapidSSL), and the community wasn’t happy that the parent company was keeping strict enough tabs on how the various parts of its CA business were operating.
Mozilla has published a list of known issues that makes informative reading for anyone who’s interested in what a CA should and shouldn’t be doing…
…but the final outcome is that Symantec sold off its CA business to DigiCert, and DigiCert agreed a timeline for replacing any existing Symantec certificates, thus helping the community get off to a fresh start.
Why is this suddenly worth a news story?
Plenty of time was agreed for the transition from Symantec to DigiCert.
Indeed, many existing Symantec certificates expired during this period, and needed renewing anyway.
Symantec and DigiCert have both been clear and open about the process that affected certificate holders need to follow, and replacement certificates are issued free of charge.
However, a small but significant minority of website owners still haven’t realised that their existing web certificates will essentially be “visually condemned” by both Chrome and Firefox this month.
What to do?
If you run any websites that still have web certificates where the CA who signed it was Symantec or one of its subsidiary brands (Thawte, GeoTrust, and RapidSSL), replace the certificate right away.
If you don’t renew or replace your certificate, you can expect a visible drop-off in traffic over the next couple of weeks: users who suddenly see security warnings when visiting your site are likely simply to shop elsewhere instead.
You can buy a new certificate from a completely different CA, or contact DigiCert, who bought up Symantec’s CA operation.
This is a really easy issue to fix – it should be no more complicated or time-consuming than renewing your driving licence or getting a new library card when you move house.
But it could be an expensive issue to ignore, if you rely primarily on search engines and links from other sites to bring in visitors and to generate new business…
…and who doesn’t?

Matt Parkes
Quite ironic that you mention about “the padlock”. We are all now running around removing this advice from our privacy policies and training materials seeing as these visual identifiers are now disappearing from Chrome & Firefox.
Paul Ducklin
The padlock hasn’t disappeared yet from my Firefox… what version will see it finally removed? The padlock is still a handy icon IMO because you can click on it to get into the “show certificate” popups. That seems an ideal use for it. I get a little “i-in-a-circle” for HTTP connections and a padlock for HTTPS. That’s in FF 62.0.3.
What word/metaphor/easy way of referring to “the thing that reminds you it’s HTTPS aside from the text https” would you suggest instead :-)
Irwin Busk
Site operators that ignore (repeated) notifications from their CA deserve the trouble.
Paul Ducklin
I hear you, but wishing people ill when they haven’t actively done something unethical (or even technically incorrect) themselves is a bit too “previous-era Linus Torvalds” for my taste :-)
Thus this article rather than just a shrug-and-denigrate…
David Pottage
The other bit of advice I would add here, is that all website operators should get into the habit of testing their site using pre-release or beta versions of the major browsers as that way they will be able to see if their site is about to be broken by an upcoming change, security related or otherwise.
I use the Nightly (Alpha) release of firefox to browse on my phone, so I know about sites that will be broken by this change for the last couple of months. I am not sure if the site owners do.
Anonymous
Heads up, that’s not quite accurate.
About a week ago Mozilla backed off on the strict distrust until Firefox 64.
Paul Ducklin
Hmmm. Thanks for that.
Note that the “strict distrust” is now moved up into the 64 Beta version (every 6 weeks, Mozilla moves the previous Beta -> release and the previous Alpha -> Beta), so more people will be using it than before. As Mozilla says in the blog article you referred to, “It is unfortunate that so many website operators have waited to update their certificates, especially given that DigiCert is providing replacements for free.”
[I’ve moved your link to an update in the main article.]
Natsu
No chrome or Firefox fault just a incompetent webmaster.
Peter
I have a number of sites for artists and these certificates add significant cost. More than one has said they are going to abandon their site if forced to pay yet another recurring fee.
Paul Ducklin
If you already have a current Symantec certificate, DigiCert will reissue it for free. Any recurring fee subsequently payable to DigiCert when the reissued certificate expires is one you’d have had to pay to Symantec anyway. So it is hardly “yet another recurring fee” that you didn’t expect.
If you don’t already have a certificate, or you are no longer prepared to pay when your current one needs renewing, you can get one for free, for example from Let’s Encrypt.
If your customers aren’t prepared to acquire certificates, they might as well abandon their sites because potential customers are going to become ever less willing to visit HTTP-only sites, and search engines are going to be less and less likely to recommend them anyway.
Certificates no longer need to be “a significant cost” – except for being a cost to you if you try to run a website without one.
Some IT guy
This is a certificate issue. Not a browser issue. If your identity were stolen from said non-secure websites and the browser didn’t warn you, you’d be more upset.
Paul Ducklin
Yes. That’s right.
The headline is meant as a bit of a wake up call for the 1% of website certificate holders who need jolting into action.
My own personal opinion is that Mozilla is being a little bit soft by giving that 1% yet another month to do what could have been done a year ago…
…but OTOH the wheels haven’t exactly come off the web in the last year that those old Symantec certs have remained valid, given that the old Symantec CA business stands accused merely of sloppiness rather than dodginess. Perhaps another month is neither here nor there.
Indeed, perhaps Mozilla is simply showing the sort of human kindness that Google’s objective, mechanicsl, hard-deadline-centric world (think of those unyielding 90-say deadlines from Project Zero) is incapable of by design.
Anonymous
Then why this headline that blames the browsers for “ruining business”?
Paul Ducklin
Browser changes security behaviour unilaterally. Visitors to your website drop off, even though you haven’t introduced any new-found danger because of that change…
…the headline isn’t really *blaming* the browser so much as making a blunt statement about cause and effect.
cholling
“How using insecure certs despite repeatedly being warned not to could ruin your online business”
Fixed that for you
Paul Ducklin
To be fair, there’s no evidence I can see of Symantec certs directly contributing to cybercriminality.
IIRC there were some bogus “test certs” that should never have been cut loose, but those have long been revoked and are thus just part of the process that led to Symantec’s demise as a CA.
If the Symantec certs still in circulation are truly “insecure” then the community surely ought to have pulled the plug on Symantec’s root certificates a year ago…
Max
If the certificates aren’t really insecure, just no longer reflecting the proper CA, then why the urgent need to remind everyone to change them? Either there is a significant risk of these Symantec certificates getting abused somehow, in which case there should not be given any leniency to sites still using them, or it is really just a harmless formality, in which case no need for all the fuss.
Paul Ducklin
The urgent need to remind people is simply that less urgent warnings over the past year haven’t worked fully enough.
tjay
Strange.. I get these warnings from Firefox by trying to access Google search and Facebook already. So I have removed Firefox as my default brower.
tjay
Update… I complained to Firefox yesterday and this morning I checked again for the error message and they are both now working. So either Firefox change something… or FB or Google.
Steve
I had a similar experience yesterday afternoon (U.S. Central time) but it resolved itself somehow by evening hours. If it was the same problem, switching browsers wouldn’t have helped; Chrome didn’t do any better than Firefox.
Catherine Jackson
I realize these posts are a year old, so I am a little behind the 8-ball. I am not an IT professional, just an ordinary everyday user. I am a frequent user of Google Chrome with Windows 10 and about a year ago, I began noticing that several websites included the “circle with i enclosed” at the beginning of the URL. I notice such things, so I searched and tried to find out why this was happening. The first explanation I found from several forums was that Google did not like Flash, so they disabled it by default, and that I could click on the “encircled i” and enable flash. The page would then reload, and the site was secure. This worked every time for about 3 months. Then it started working less and less to resolve the problem. Now, it does not resolve the problem at all. Almost ALL of the websites I in Google Chrome that I visit are shown with the “encircled i” at the beginning of the URL. While I know that it will no longer correct the problem, I still go in and enable flash anyway (which Google Chrome is going to discontinue next year anyway), and of course, it does not resolve the problem. I also go to the site settings and see if there is something I might be able to do there, but no joy. I do not have time to do that all day long. As was mentioned in the above article several times, as a user who is not completely technologically impaired, but by no means an expert, I do not feel comfortable staying on a website that is “not secured.” Unless I need significant information from that unsecured site, I will immediately leave a website that bears the mark meaning “not secured.” The norm for me a year later is seeing more websites marked “not secured” than websites bearing the padlock meaning they are “secured”, so this article explains a lot. I would not think that finding a way to remove the mark showing the website is “not secured” is a good idea. I do hope Google figures out a way to correct this problem. If not, I will find another browser to use. As for all of those website owners out there, PLEASE update your certificates.