Exploits are the techniques that attackers use to gain access and control of computers. Common bugs and vulnerabilities found in popular, legitimate software can be leveraged as exploits to steal data, hold files for ransom, perform reconnaissance, or simply to deploy malware.
Attackers rely on exploits the same way video game characters rely on their weapons toolkits: without them, it would be like going into battle unarmed. And despite being extremely popular for attackers, many defenses remain vulnerable to exploits, since the software often being exploited – Microsoft Office, Adobe Reader, and the like – is generally considered “safe” by security products.
This would seem to make exploit testing a no-brainer for vendor comparison services. The problem, however, is that due to the constantly evolving nature of software vulnerabilities, exploit-based attacks are some of the most difficult scenarios to test.
Fortunately, MRG Effitas managed to develop reliable and repeatable exploit testing scenarios and has recently released its “Exploit and Post-Exploit Protection Test” report. Commissioned by Sophos, this report compares the exploit-stopping abilities of nine different endpoint products.
As you can see in the chart below, Sophos far outperformed other vendors at stopping exploits: Level 1 means that the product blocked the exploit, and Level 2 means that the exploit was missed but the attack was stopped via other methods.
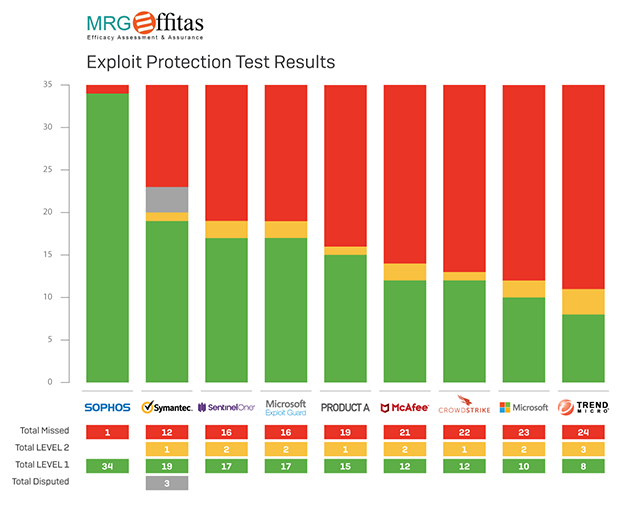
Sophos blocked 34 out of 35 exploits tested, while the next highest score was 22 out of 35. In fact, most vendors weren’t even able to stop half of the exploits that Sophos was able to stop.
This test was a follow-up to MRG’s previous report on malware protection. In that commissioned report, Sophos ranked #1 for both malware protection and potentially unwanted application (PUA) protection.
To summarize the test results from the two MRG Effitas reports:
- Sophos ranks #1 in exploit prevention
- Sophos ranks #1 in malware protection
- Sophos ranks #1 in potentially unwanted application prevention

Leave a Reply