Bots run by shady websites are abusing the redirection functionality found in some US government websites to create thousands of phantom “pages” linking to unsavoury content.
Gizmodo reported on Tuesday that it had discovered the flaw on the Justice Department’s AmberAlert.gov website, an emergency broadcast system for sending alerts about suspected child abductions.
A website run by the US Justice Department and used to gather information about missing and abducted children is redirecting visitors to porn sites with names such as “schoolgirl porn” …
Naked Security can confirm that the flaw also exists on a plethora of other government websites too, including: a website operated by the US Congress, websites used to access important federal services and local government sites at the state and county level.
Gizmodo reports that “the Amber Alert site was repaired … efforts [are] underway to address any similar issues affecting other government domains”.
The government websites being abused in this way haven’t been hacked. No pages have been created – it’s just that the way the government sites handle page redirects makes it possible for an attacker to fool Google into thinking they have.
They likely do this in the hope it will improve their chances of being found in a Google search – either because there are multiple URLs for one page, or because it improves the attacker’s PageRank.
Simplistically, Google’s fabled PageRank algorithm treats links from one website to another as a “vote” for the site being linked to. The votes are weighted so that links from sites with a high PageRank are more valuable than links from sites with a low PageRank.
All other things being equal, the better your site’s PageRank, the better it will do in search results.
The attack works like this:
An attacker operating the website attacker.example creates a computer program to crawl the web looking for websites with an open redirect flaw (also known as unvalidated redirects or unvalidated forwards).
During its crawl it finds a government website, we’ll call it victim.example, with a vulnerable redirection page at victim.example/redirect.
The vulnerable redirection page takes a parameter, let’s call it url, that indicates which page a user should be redirected to if they click on or type the link. This allows the attacker to concoct a victim.example URL that will actually bounce users to a page on the attacker’s website:
http://victim.example/redirect?url=attacker.example/page-1.html
And the attacker isn’t limited to one URL. Each redirect is a unique URL that Google will treat as a separate page, so an attacker can generate URLs for every page on their website.
http://victim.example/redirect?url=attacker.example/page-1.html http://victim.example/redirect?url=attacker.example/page-2.html http://victim.example/redirect?url=attacker.example/page-3.html ... http://victim.example/redirect?url=attacker.example/page-9999.html
Note that the victim’s site isn’t breached and no pages have been created on the victim’s site – all the attacker has done is discovered that they can make a URL with a victim.example domain.
Now they have to use that capability, somehow.
They could use the open redirect to create trustworthy-looking links that redirect to phishing pages, malware downloads or other dangerous content, and put those links in emails, tweets or other messages.
In this case though they want to get listed in Google search results so all they have to do is put the links somewhere Google’s web crawler will find them, such as their own website.
When the Google crawler visit’s the attacker’s site it finds a link to the victim.example redirection page. It follows the link and the page that it finds there gives the attacker two bites of the cherry:
- The page includes a PageRank boosting link to a page on
attacker.example - After a few seconds it redirects the Google crawler to the page on
attacker.example
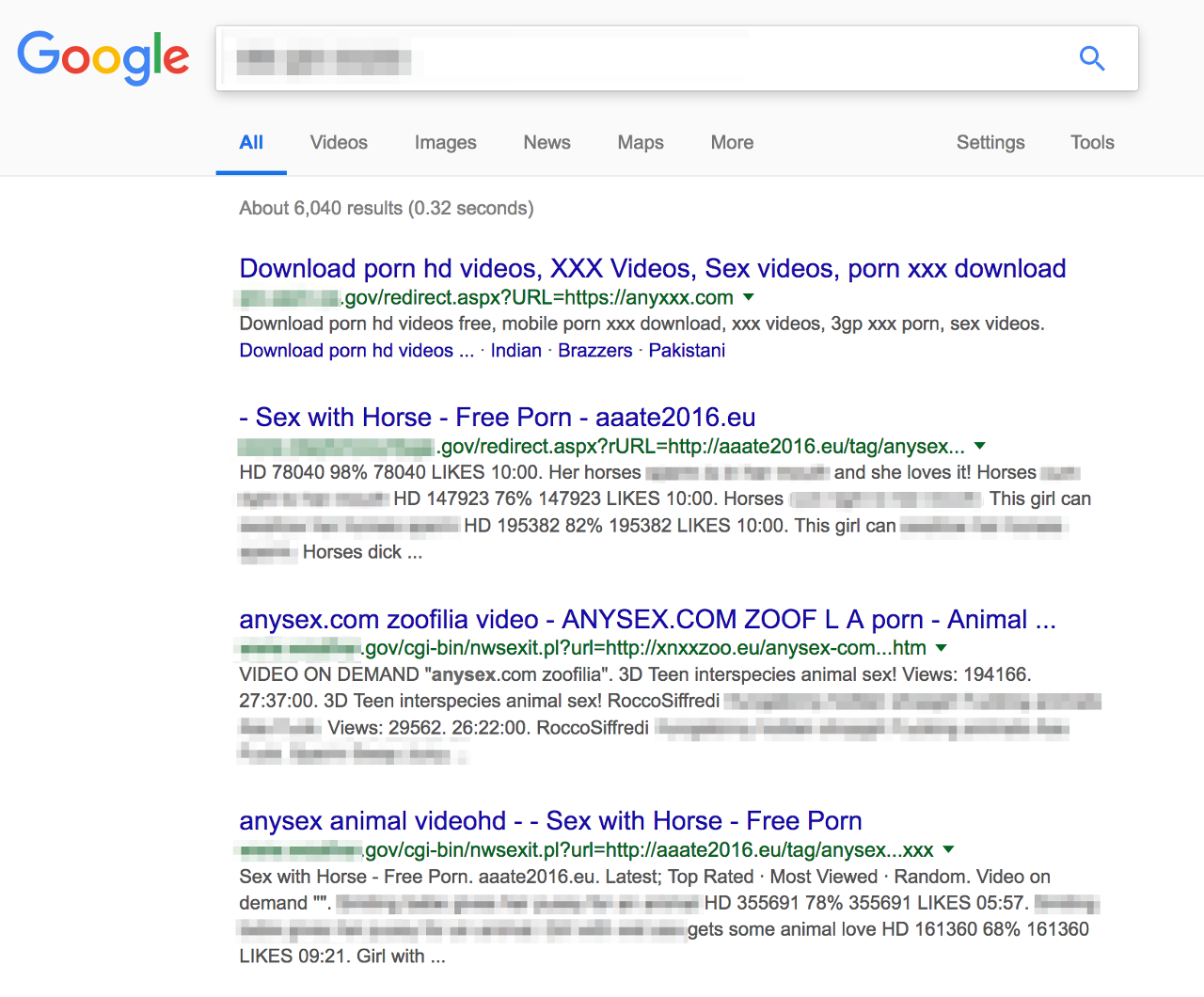
Google catalogues the content it finds on the attacker.example page under the victim.example URL it used to get there, leading to search results that look like this:
The lesson, as ever, is that any and all user input should be treated as hostile until it has been checked and sanitised.
If your website’s redirection code relies on a parameter that users can manipulate, have a good long think about whether that’s the right approach. If you’re sure it is, be careful to reject anything that doesn’t match the strict criteria for sites you’re happy to link to, using something like a closed list of friendly sites or pages.
You can add a belt to your braces and make it difficult for other sites to hijack your redirection code by forcing them to supply a nonce (a “number used once”) known only to your site, along with the URL they want to redirect to.

Some One
Naked Security indeed!
Steve
Your tax dollars at work!
Nobody_Holme
I’m surprised we saw this from porn bots instead of phishermen first.
Bet you a lot it’s been used in a speahphish attempt by the time i post this, though.
Chris
This has been going on for years. I’ve seen this being used in shady SEO at least 3-4 years ago.
william
Because it increase the page rank easily