Organizations in Russia and Ukraine were under siege on Tuesday 24 October 2017 from Bad Rabbit, a strain of ransomware with similarities to NotPetya.
By evening, the outbreak was reportedly spreading into Europe, including Turkey and Germany. Victims reported so far include airports, train stations and news agencies.
Russia’s Interfax news agency reported on Twitter that the outbreak had felled some of its servers, forcing Interfax to rely on its Facebook account to deliver news.
Starts with social engineering
The Bad Rabbit outbreak appears to have got its start via files on hacked Russian media websites, using the popular guise of pretending to be an Adobe Flash installer.
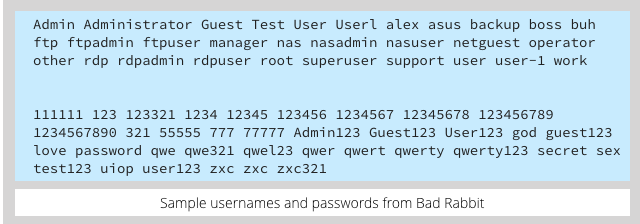
If Bad Rabbit infects your computer, it attempts to spread across the network using a list of usernames and passwords buried inside the malware. These credentials include passwords straight out of a worst passwords list. Another reminder, if one were needed, that all your passwords need to be strong, even the ones you use behind the safety of a corporate firewall.
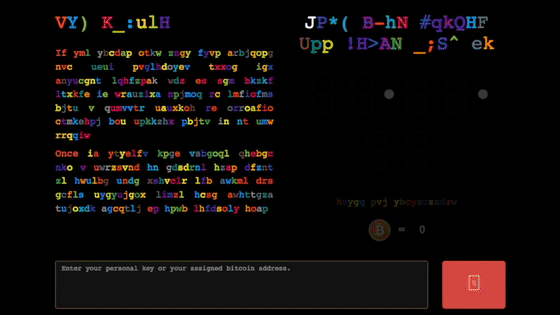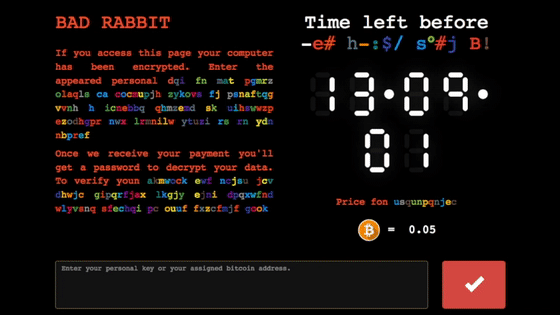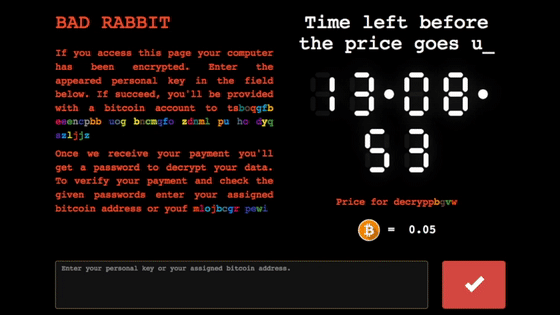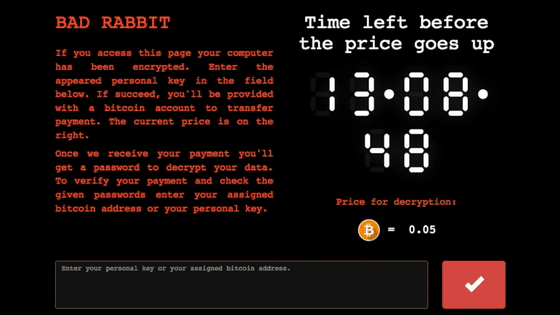
From there, it encrypts not only your files, adding encrypted at the end of each filename, but also your computer’s MBR (Master Boot Record). You are then greeted with the following message and asked to submit payment via a Tor hidden service (an anonymous Dark Web website):
Oops! Your files have been encrypted. If you see this text, your files are no longer accessible. You Might have been looking for a way to recover your files. Don't waste your time. No one will be able to recover them without our decryption service. We guarantee that you can recover all your files safely. All you need to do is submit the payment and get the decryption password. Visit our web service at [redacted]
If you visit the Bad Rabbit website using the Tor Browser, you will be “invited” to pay a fee for the decryption key; at the time of writing [2017-10-25T16:45Z], the crooks were demanding XBT 0.05 (1/20th of a Bitcoin), currently about $280:
Defensive measures
Sophos currently blocks the Bad Rabbit malware as Troj/Ransom-ERK.
Additionally, Sophos Intercept X proactively prevents the malware from attacking your data: the CryptoGuard component stops the ransomware from scrambling your files, and WipeGuard prevents the low-level disk writes that modify the boot sector.
(For further information about Sophos protection, please see our Support Knowledge Base article entitled Bad Rabbit ransomware: What to do.)
Here are some general tips to raise your defenses againt this sort of outbreak:
- Ditch Flash altogether. Fake flash installers and updates only work as a social engineering tactic if you use or want Flash. By removing Flash entirely you not only protect yourself from Flash zero-day holes , but also eliminate the temptation to download fake updates.
- Patch promptly. Outbreaks such as NotPetya and WannaCry exploited a vulnerability for which patches were already available. Don’t lag behind once patches are available for known security holes – the crooks will be only too happy to take advantage.
- Remember your backups. Make them regularly, and keep a recent backup both offline and offsite, so you can access it even if your workplace ends up off limits due to fire, flood or some other cause not related to malware.
- Don’t make users into administrators. When you want to perform administrative tasks, promote yourself to an administrator account, and relinquish those privileges as soon as you can. Network-aware malware like Bad Rabbit can spread without even needing to guess passwords if you already have administrator-level access to other computers on the network.
For more information about ransomware read How to stay protected against ransomware, or listen to our Techknow podcast:
LISTEN NOW
(Audio player above not working? Download, or listen on Soundcloud.)
If you’re a home user, why not register for the free Sophos Home Premium Beta? This includes the CryptoGuard and WipeGuard features mentioned above that block the unauthorised scrambling of files and disk sectors.

FvSpiegel
other security providers say one can add:
• %windir%\infpub.dat
• %windir%\dispci.exe
• Permissions: everyone deny
Mark Stockley
We never pass on hacks like this because they work right up until they don’t. New variants of malware are released constantly so a trick or a hack that defends against one generation of a particular threat might work now, but not in an hours time.
We also think that if we’re going to advise people to do something that you should also advise them of any likely side effects or unintended consequences. Does the hack work everywhere, for everyone, on any version of Windows, on any size of network?
Is it worth investing the time to find out the answers to those questions when the advice might be redundant before you even get one? Better surely to rely on overlapping layers of complimentary security products that will do the job better whilst also protecting you against a huge number of other threats and threat vectors that aren’t currently grabbing headlines but could ruin your day just as easily.
Anonymous
Unfortunately ditching Flash (while a great idea) wouldn’t have any impact here. Even if you can/do eliminate it that doesn’t mean your users will know or remember that you did. This is social engineering – it doesn’t rely on the victim having Flash. It only relies on them to think they do and to think they need the update.
Educating users on how to spot and avoid attacks of this nature is still something that should be high on the list of preventative measures.
Paul Ducklin
It’s a tip; it’s a suggestion – not a panacea :-)
If you ditch Flash (and remember, this could be at home, doesn’t have to be at work) then you have at least some chance of remembering that it no longer belongs on your computer, no matter who tries to tell you it does.
But if you do have Flash, then the only thing you can be really sure about is that you to need to install a new version regularly, for safety’s sake.
So I can’t see how ditching Flash can be anything other than neutral at worst, and useful at best.
Anonymous
Yep, and that’s why I said it was “a great idea”. ;) Just wanted to point out that you still need to account for user education. We’re running phishing training right now and I can’t tell you how many people click on account password resets for accounts they don’t have or how many people download files from Dropbox from people they don’t know or how many people take messages from Linked In or Amazon to their work email seriously even though their work email isn’t tied to their accounts or … you get the picture.
That someone should know better doesn’t mean they do. If you can get rid of Flash by all means do so. Just remember, though, that your users may not remember you did and take appropriate measures. Defense in depth, right? Kill Flash and educate your users.
Paul Ducklin
+1.
(I am glad you didn’t mix up the objects of the verbs in that last sentence…)
Anonymous
Well, you did catch me on a good day. :P
Lisa Vaas
Somebody, somewhere in marketing has to dub their Rabbit-fighting tools Watership DOWN!
Paul Ducklin
I’m waiting for one called “Holy Handgrenade of Antioch”…
Anonymous
Or Elmer Fudd!
Bryan
And here’s Lisa, awakening from perennial slumber distant and forgotten memories.
Wow, it’s been a thousand years.
Vincent
What is a reasonable alternative for FLASH?
Mark Stockley
As a developer, HTML5. As a user, you’re stuck with whatever choices the developer makes.
Tony Butt
So, BadRabbit was released, they watched it spread for a day, and it doesn’t use annything novel in terms of worm capability.
This looks like another test, to see how the ‘delivery system’ performs, and how quickly the payload can be delivered to how many targets.
This smells like a cyber weapons test, and we should all be worried about what will happen when the real payload is loaded.
Paul Ducklin
Of course, you could say that about almost any of the many new malware samples that show up each day. As for “the real payload”, there are thousands of real payloads each day, if you want something to be worried about. Keyloggers, spambots, data stealers, banking Trojans, cryptocurrency miners – the list is long. The good news is that the same core set of precautions will protect you from a very wide range of malware attacks…so making sure you’re taking those precautions is better IMO than worrying about cyberwhateverbadadjectivecomesnext.
TraderStf
Amazing that Google Finance still uses Flash!