In the last two weeks, Sophos researchers have kept an eye on a vulnerability in Microsoft’s Dynamic Data Exchange (DDE) protocol used to send messages and share data between applications.
Yesterday, new developments revealed an additional dimension to this attack.
Early on, we noted that attackers could exploit DDE to launch malware via tainted Office attachments, for example in Word and Excel files, but without using macros.
On Friday, independent reports surfaced showing that it’s possible to run DDE attacks in Outlook using emails and calendar invites formatted using Microsoft Outlook Rich Text Format (RTF), not just by sending Office files attached to emails.
In the original attack users had to be coaxed into opening malicious attachments. By putting the code into the email message body itself, the attack comes one step closer, meaning that the social engineering needed to talk a recipient into falling for it becomes easier.
The good news is that whether a DDE attack comes via an attachment or directly in an email or a calendar invite, you can stop the attack easily:
Just say no
Attachments, emails and calendar invites pop up two giveway warning dialogs before triggering a DDEAUTO attack; if you say “No” at either dialog then you prevent the attack. (SophosLabs is not yet aware of any mechanism to bypass these dialog boxes.)
First, you’ll see a warning like this when DDE is used:
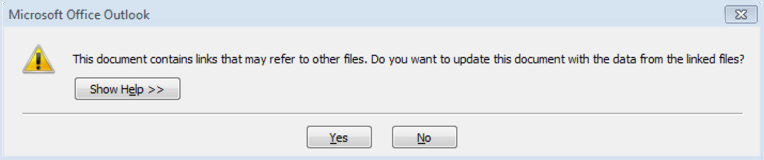
This document contains links that may refer to other files. Do you want to update this document with the data from the linked files?
Clicking “No” will stop a DDE attack from running.
If you click “Yes” at the first dialog, you will see a second dialog warning that a command is about to be run (the text in parenthesis and the program names referenced at the end will vary):
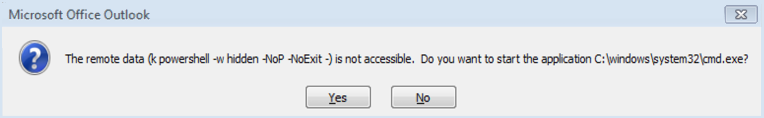
The remote data (k powershell -w hidden -NoP -NoExit -) is not accessible. Do you want to start the application C:\windows\system32\cmd.exe?
Again, clicking “No” will stop the attack.
You can also neuter DDE attacks embedded directly in emails by viewing all your messages in plain text format, regardless of the format they were sent in.
Note, however, this will disable all formatting, colours and images in all messages, including those sent in the popular HTML email format. This will make some messages harder to read and may prevent you seeing content that the sender is expecting you to to see.
Please check the Microsoft Support website for details of how to view all emails in plain text format in Outlook.
For more information, here’s a short video we’ve published on Facebook Live:
Just say “No!” – how to stop the DDE email attack
https://www.facebook.com/SophosSecurity/videos/10155119823700017/
(Can’t see the video directly above this line? Watch on Facebook instead.)
(You don’t need a Facebook account to watch the video, and if you do have an account you don’t need to be logged in. If you can’t hear the sound, try clicking on the speaker icon in the bottom right corner of the video player to unmute.)
- CXmail/OffDDE-*: emailed attachments and booby-trapped messages.
- Troj/RtfDDE-*: booby-trapped RTF files.
- Troj/DocDl-DJV: DDE attacks that try to download additional malware.
Note: Security threats involving DDE exploits were first reported by researchers at SensePost in May 2016.

eunicepomfret
Might you also prevent this by using a Mac?
Paul Ducklin
As far as I know, the trick doesn’t work on Macs.
I’ll ask the SophosLabs guys to make sure – but DDE is a Windows thing, and even if there is DDE-like equivalent that works between Microsoft apps on a Mac, I don’t think that the DDEAUTO “feature” (bug?) would allow Mac scripts to be launched. But, like I said, I am thinking aloud here, not speaking from certainty.
brownj00
How many years will go by before Mac (or Linux) users stop chiming in with the cheap shots every time a new vulnerability with a Microsoft platform is discussed?
Mac/Linux, Android, IOS, etc. all have viruses or other security issues. The nah-nah comments were old and tired 20 years ago. Let’s all move on to be more constructive.
theGunner
Yeah but you just login to macs root account with no password so there is not really much point going to all the trouble of social engineering/exploiting anyway lol
Paul Ducklin
Not any more… Apple fixed that root password bug PDQ. Thankfully :-)
https://nakedsecurity.sophos.com/2017/11/30/apples-blank-root-password-fix-needs-a-fix-of-its-own-here-it-is/
rabih
is there any windows patch for it ?
Mark Stockley
Microsoft doesn’t consider this a bug and so we’re not expecting a patch. We respectfully disagree with Microsoft on this – DDE is only supposed to allow communication with software that is already running but for these attacks to work it has to start the linked application.