Thanks to Jagadeesh Chandraiah of SophosLabs for his behind-the-scenes work on this article.
Last year, we told you about DirtyCOW, a privilege escalation bug in the Linux kernel that allows ordinary users to turn themselves into all-powerful root users. It soon became clear that DirtyCOW didn’t just affect Linux running on Intel processors but was also exploitable on Android (a modified version of Linux) running on ARM chips too.
This raised the possibility of DirtyCOW being used to compromise phones and tablets.
SophosLabs has now found malware, dubbed ZNIU, that does exactly that.
Enter ZNIU
Victims have to stray beyond the safety of the Google Play walled garden to get ZNIU, so attackers trick them into downloading infected apps from untrusted sources with old-fashioned social engineering. This example of ZNIU comes packaged as a porn app:
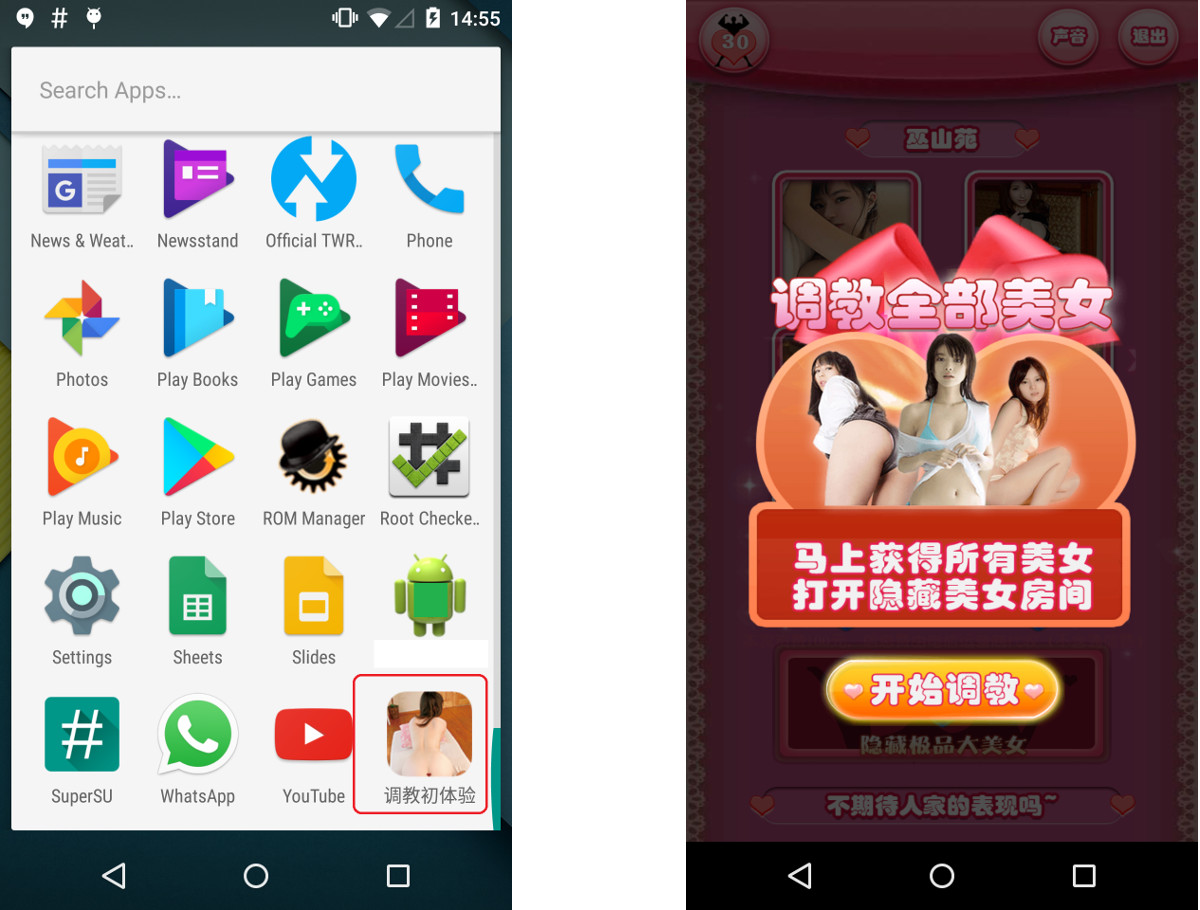
After being installed the app exploits DirtyCOW to elevate its privileges, bypassing the restrictions that would normally stand in its way. Once it infects a device, ZNIU chats with its command and control servers to receive updates and orders. Command-and-control servers are consulted whenever the infected device is connected to a power outlet or there’s a change in connectivity.
Malicious code contained in APKs (Android Application Packages) is downloaded from remote servers and executed at runtime in the hope of avoiding early detection from malware scanners.
ZNIU also creates a backdoor that can be used for future remote-controlled attacks and has the ability to send SMS messages, which opens the door for money making schemes such as sending spam, phishing or messaging premium rate numbers owned by the attacker.
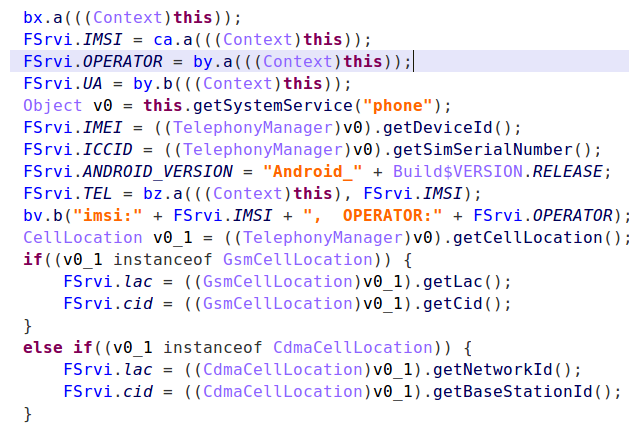
The malware also collects device data:
The DirtyCOW vulnerability
By successfully exploiting the DirtyCOW bug (known officially as CVE-2016-5195), ZNIU is able to grant itself all the permissions it needs to do harm without having to ask the user, or trick them.
The bug is explained in the Red Hat bug database like this:
A race condition was found in the way Linux kernel’s memory subsystem handled breakage of the read only private mappings COW situation on write access.
An unprivileged local user could use this flaw to gain write access to otherwise read only memory mappings and thus increase their privileges on the system.
In other words, the Linux Copy On Write mechanism can be tricked into overwriting a read-only file, which is something of a security catastrophe if that read-only file is a critical system executable or configuration file.
For a comprehensive explanation of DirtCOW, check out Paul Ducklin’s excellent article – Linux kernel bug: DirtyCOW “easyroot” hole and what you need to know.
What to do
The good news is that ZNIU isn’t available on Google Play and only works on devices running older versions of Android that aren’t patched against DirtyCOW.
Google released a patch for Android way back in December but, sadly, the Android ecosystem is badly fragmented and whether or not you get updates is up to your vendor, not Google. Different vendors will release patches at different times and some may not release them at all.
So just because there’s a patch for DirtyCOW, that doesn’t mean you’ve got it. What we can say for sure is that users of the latest version of the Android operating system, Oreo, have nothing to worry about and that Sophos Mobile customers are protected (Sophos detects ZNIU as Andr/Rootnik-AI and Andr/ZNIU-A.)
If you’re concerned about your device, please contact your vendor.
Another tale of patches unapplied
History is littered with cases where attacks and outbreaks have happened because patches were available but weren’t applied. There’s no better example in recent history than the WannaCry outbreak in May 2017. At the time, we noted that it its spread was made possible in part by the unheeded lessons of the past, such as Slammer and Conficker.
The DirtyCOW hole was plugged a year ago so please make sure you have the latest security updates on your phone or tablet.
