Finnish security researcher Juho Nurminen is a bit of a retweet celebrity right now, for all the wrong reasons.
Not his wrong reasons, but the wrong reasons of Adobe’s Product Security Incident Response Team (PSIRT).
To explain.
Most security teams publish encryption keys so that you can communicate securely with them, using a public key cryptography tool such as PGP or GPG.
Public key encryption, also known as asymmetric encryption, is the sort that uses two keys, rather than one: a public key to lock a file, and a corresponding private key to unlock it.
(You generate these keys, which act as a sort of mathematical function and its inverse, as a pair, and although it’s pretty quick to generate a keypair, it’s as good as impossible – computationally infeasible, in the jargon – to figure out the private key given the public key.)
It’s probably obvious from the nomenclature here that the PUBLIC key is for locking files, and that you share it, well, PUBLICLY so that anyone can encrypt data to send it to you securely.
The PRIVATE key is for unlocking data that was encrypted with your public key, and as long as you keep it, you know, PRIVATE, then only you can ever decrypt that data.
At the risk of labouring the point, you make the public key public, and you keep the private key private.
For this reason, PGP/GPG keys, when converted into text format for easy storage and use, look something like this:
PSIRT PGP Key (0x33E9E596) -----BEGIN PGP PUBLIC KEY BLOCK----- Version: Mailvelope v1.8.0 Comment: https://www.mailvelope.com [redacted] -----END PGP PUBLIC KEY BLOCK----- -----BEGIN PGP PRIVATE KEY BLOCK----- Version: Mailvelope v1.8.0 Comment: https://www.mailvelope.com [redacted] -----END PGP PRIVATE KEY BLOCK-----
When you want to send someone your public key, the ---BEGIN--- and ---END--- blocks are there as a visual clue to help you copy and paste the right one.
Adobe it seems, generated the above keypair within the past few days , giving it a lifetime of one year, presumably to replace last year’s now-expired key.
Of course, a new public key is no use until you make it public, so Adobe popped it onto the PSIRT blog…
…but posted the whole keypair, public and private.
Someone who has Adobe’s private key can not only post messages that apparently have Adobe’s imprimatur, but also decrypt messages that people sent to Adobe under the assumption that only the PSIRT would ever get to read them.
Fortunately, as far as we can see, Adobe’s (now-revoked) private key was itself encrypted with a passphrase, meaning that it can’t be used without a secret unlock code of its own, but private keys aren’t supposed to be revealed even if they are stored in encrypted form.
If you let your your PGP/GPG private key slip, your leak cuts both ways, potentially affecting both you and the other person in the communication, for messages in either direction.
What to do?
- Don’t use Adobe’s public key with the PGP fingerprint shown below to send information to PSIRT.
- Don’t trust any messages signed with this key, even though the leaked private key was encrypted.
- Don’t make this mistake yourself if you use public-key cryptography tools. (It’s an easy mistake to make when you’re copying text – so, to borrow a saying from carpentry, measure twice, cut once.)
We’ll say it one more time: make the public key public, and keep the private key private!
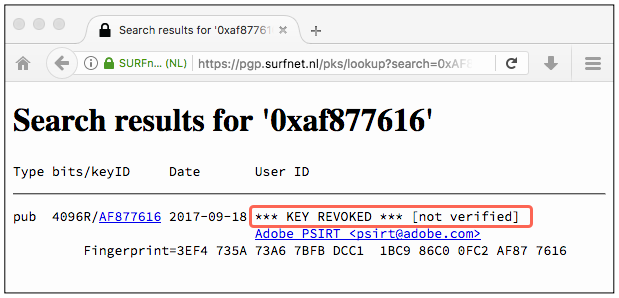
Key details:
Adobe PSIRT <psirt@adobe.com>
public key: 4096R/AF877616 2017-09-18 [expires: 2018-09-18]
fingerprint: 3EF4 735A 73A6 7BFB DCC1 1BC9 86C0 0FC2 AF87 7616

John
I’m guessing the task of “update website with new encryption key” fell to the new guy/gal, who is probably updating their resume now.
Anonymous
Well, the private key was encrypted with a passphrase, a fact that every report I have seen (except this one!) seems to have ignored. Embarrassing and not good but the “leak” was more a PR blunder wouldn’t you say?
Anonymous
It can still be used for social engineering vectors; even if having the private key may not suffice for authentication – hackers can still use the news of the “leaked” key to trick you into doing their bidding.
Mark Stockley
…and a lesson on defence in depth.
Waiting for Adobe to finally close their doors.
John, this is Adobe, home of perennial security issues. Not only don’t I assume the ‘new guy\gal’ was involved, I also don’t assume this was a RGE.
But really, it OUGHT to be true on both counts. There’s a moral here, and it goes something like:
“Adobe knows little to nothing about security”.
Decades of evidence back that up. They’ve been exploit central since AT LEAST them suing Macromedia into oblivion and seizing the products (then mismanaging and expanding all known problems for AGES).