Thanks to Anand Ajjan and Dorka Palotay of SophosLabs, and Paul Ducklin of Naked Security, for the research this article is based on.
Ransomware is a blunt instrument that wants your money and doesn’t usually care if it leaves footprints behind.
So when SophosLabs researchers analyzed a sample of the BitPaymer ransomware family, they were surprised to see it using a malware coding trick that you don’t see very often – one that makes it harder to figure out how the attack unfolded after the event.
While that may sound like cold comfort if your files have just been scrambled, it makes it harder to warn the next victim what to look out for.
This sample uses a feature of the Windows file system called alternate data streams (ADS) so that the malware is less obvious while running.
BitPaymer starts off as a regular .EXE (program) file, but when running the malware copies itself into not one but two alternate data streams where it exists as a sub-component of otherwise empty files.
The malware then transfers control into the new copies of itself in ADS and deletes the more obvious .EXEfile in which it arrived.
(SophosLabs researchers have received a sample of the malware but fortunately haven’t seen it in the wild yet. If it were used, it would likely arrive as a malicious email attachment or link, as is typical for ransomware attacks.)
Sophos Anti-Virus detects BitPaymer as Troj/Agent-AXEG and HPmal/Ransom-Y.
Let’s explore this malware in greater detail…
What are alternate data streams?
Conventionally, a file consists of a sequence of bytes stored under a unique filename. This sequence of bytes is often referred to as a stream.
Windows NTFS (NT file system) files not only have a main stream, referred to by the filename, but can also have any number of alternate data streams stored along with the file and referenced by the filename, followed by a colon, followed by the alternate data stream’s name.
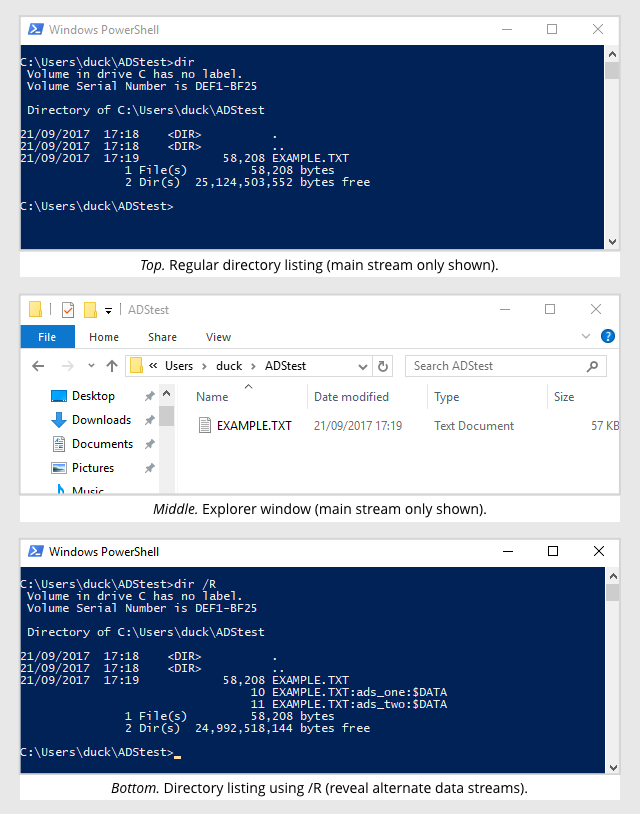
Only the filename of the main stream shows up in regular directory listings or in Explorer.
Because of this, attackers sometimes use ADS in an attempt to hide what they’re doing from security software, but it’s rare to see ransomware using it in this manner.
According to SophosLabs researcher Anand Ajjan, ADS is typically used for storing additional data about the main stream, such as the date and time the file was downloaded from the Internet.
Ajjan said:
ADS adds more stealth. When a process is launched and does something malicious, there are no files backing the process except alternate data streams.
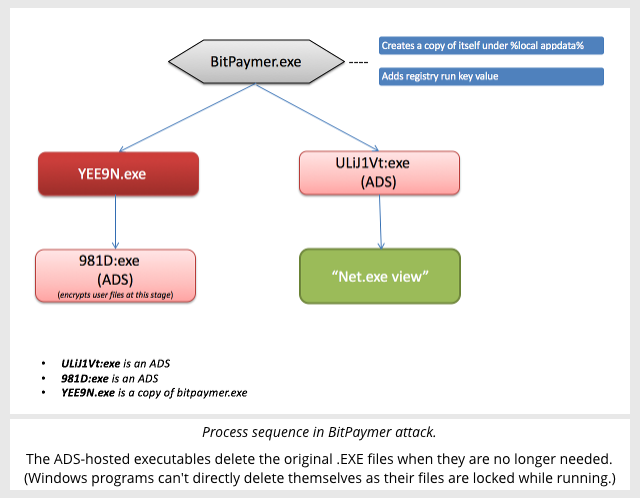
Attack sequence
According to our analysis in SophosLabs, BitPaymer:
- Copies itself into your APPDATA directory, using a random filename and marking the file hidden. This is a location commonly used by malware as a place to “hide in plain sight”.
- Sets an autorun entry in the registry to relaunch the hidden copy of BitPaymer automatically if you reboot your computer. (This means pulling the plug won’t save your data.)
- Spawns a copy of itself from an ADS called
:exein a randomly-named empty file, using this copy to run theNET VIEWcommand to obtain a list of your network shares. - Creates a second hidden copy of itself in the APPDATA directory, then spawns a copy of this copy, again using an ADS called
:exein a randomly-named empty file. This instance of the malware scrambles the data on your disk and network shares.
Because the running copies of the original malware files end up shrouded in two ADSes, they are less noticeable than usual, and can delete the original malware files when they’re finished.
To encrypt files:
- BitPaymer uses a hard-coded RSA-1024 public key, which is imported using the CryptImportPublicKeyInfo function.
- For each file, an RC4 key is generated using CryptGenKey.
- This key is encrypted using the RSA key and the CryptExportKey function.
- The encrypted key is saved at the beginning of the file.
- The full files are then encrypted using the CryptEncrypt function.
- During encryption, the original file is overwritten with “Ooops” and is then deleted
- It replaces with a new file with a
.lockedextension (which contains the encrypted RC4 key followed by the encrypted content).
Most ransomware sticks to encrypting your data files, steering clear of your application directories and program files such as EXEs and DLLs: software that goes missing unexpectedly can cause problems such as crashes and instability. (The crooks want to make sure you can still get online and use your browser after the attack, because that’s how they squeeze the ransom out of you.)
BitPaymer is more aggressive than that, encrypting your apps and program files along with your data, although it carefully avoids the Windows folder to avoid messing with the operating system itself.
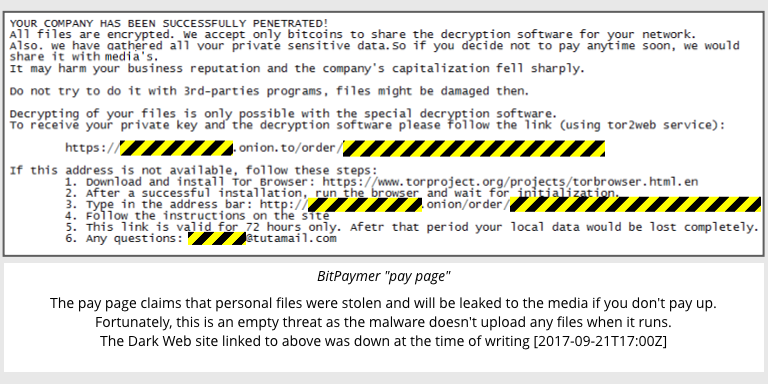
The pay page
BitPaymer, like most ransomware, does its damage quietly with your files getting scrambled invisibly in the background.
You only realise you’re in trouble when your files turn into shredded cabbage and you’re greeted with the message YOUR COMPANY HAS BEEN SUCCESSFULLY PENETRATED:
Defensive measures
As mentioned above, Sophos Anti-Virus detects this ransomware as Troj/Agent-AXEG and HPmal/Ransom-Y.
To avoid the financial and data loss that goes with such an attack, we also recommend regularly backing up files and keeping a recent backup copy off-site.
There are dozens of ways other than ransomware that files can suddenly vanish, such as fire, flood, theft, a dropped laptop or even an accidental delete.
Encrypt your backup and you won’t have to worry about the backup device falling into the wrong hands.
Other resources
Other links we think you’ll find useful:
- To defend against ransomware, see our article How to stay protected against ransomware.
- To learn more about ransomware, listen to our Techknow podcast.
- To protect your friends and family, try our free Sophos Home for Windows and Mac.
Techknow podcast — Dealing with Ransomware:
LISTEN NOW
(Audio player above not working? Listen on Soundcloud or access via iTunes.)


Leave a Reply