Thanks to Chen Yu, Rowland Yu and William Lee of SophosLabs for their behind-the-scenes work on this article.
Google has had an exciting summer, for good and bad reasons.
The good news: Google just officially launched the eighth version of its operating system, Android Oreo, with enhancements for battery life and security. Last month, it also began rolling out a new feature called Google Play Protect, designed to scan apps that could cause harm to your Android device and data.
The bad news: at least five different types of malware were found in Google Play in August alone, including spyware, banking bots and aggressive adware. Thousands of apps contain these malicious payloads and have infected millions of users.
Yesterday, we reported that Google has had to pull some 500 apps from its Play Store, which together had been downloaded more than 100m times. The apps – which weren’t in themselves malicious – all used a software development kit (SDK) called Igexin. Among other things, the Igexin SDK has the ability to spy on victims “through otherwise benign apps by downloading malicious plugins”. Advertising SDKs make it easy for app developers to tap into advertising networks and deliver ads to their users.
As well as that issue, SophosLabs researchers have identified other threats to your device.
Banking bots
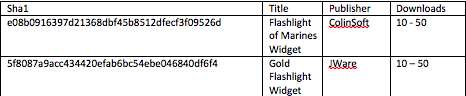
SophosLabs discovered some 20 different apps in Google Play – all detected as Andr/Banker-GUB – and recorded some Google Play download information for two versions:
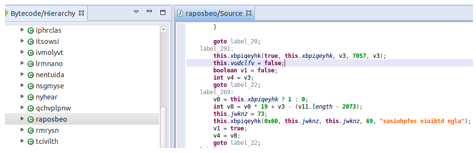
This malware family relies on obfuscation and packers to make reverse engineering more difficult:
It uses a powerful framework called OkHttp to exchange data and information from a website. The framework uses aggressive techniques to navigate systems with multiple IP addresses:
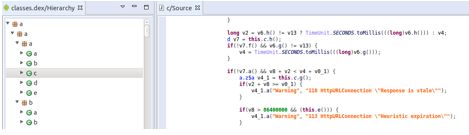
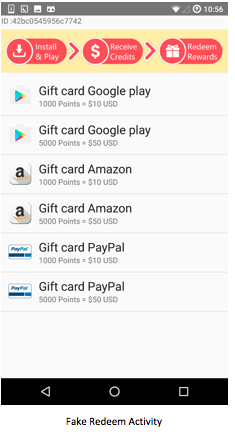
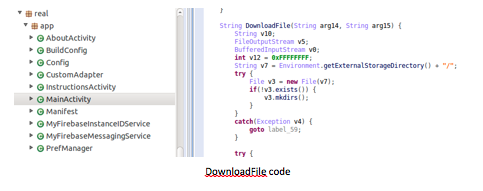
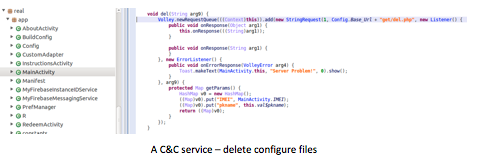
A second bankbot was just discovered few days ago and is able to silently download APK from a remote website, lure users to install APK using fake credit points, and display a spoofed “security update payment” based on the Google Firebase Messaging Service:
GhostClicker
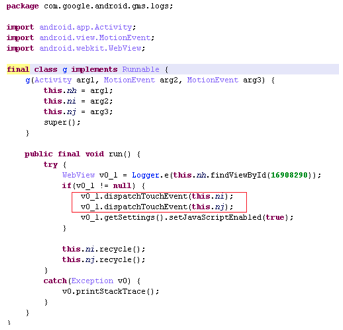
Researchers also intercepted an adware family called GhostClicker, which disguises itself as part of the Google Play service library or Facebook Ads library. It adds itself as a package named “logs” into those libraries. Some variants request device administration permission, and actively simulate click-on advertisements it delivered to earn revenue:
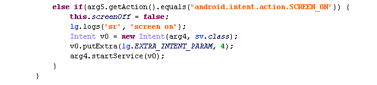
While other variants are more conservative, they register themselves as BroadCastReceiver and pop up advertisements:
Sophos detects the auto-click variant as Andr/Clicker-HO and another variant as Android Adload.
Defensive measures
The continued presence of malicious and compromised Android apps demonstrates the need to use an Android antivirus such as our free Sophos Mobile Security for Android. By blocking the install of malicious and unwanted apps, even if they come from Google Play, you can spare yourself lots of trouble.
In the bigger picture, the average Android user isn’t going to know what techniques the malware used to reach their device’s doorstep, but they can do much to keep it from getting in – especially when it comes to the apps they choose. To that end, here’s some more general advice:
- Get Android Oreo. A rough summer aside, Google’s new OS is certainly an improvement and should do better at keeping out malware going forward.
- Stick to Google Play. It isn’t perfect, but Google does put plenty of effort into preventing malware arriving in the first place, or purging it from the Play Store if it shows up. In contrast, many alternative markets are little more than a free-for-all where app creators can upload anything they want, and frequently do.
- Avoid apps with a low reputation. If no one knows anything about a new app yet, don’t install it on a work phone, because your IT department won’t thank you if something goes wrong.
- Patch early, patch often. When buying a new phone model, check the vendor’s attitude to updates and the speed that patches arrive. Why not put “faster, more effective patching” on your list of desirable features, alongside or ahead of hardware advances such as “better camera” and “higher-res screen”?


R. Dale Barrow
The goto’s in the last code segment make my skin crawl, Ugh!
Anonymous
You guys keep talking about Oreo in the present tense, as though it’s something I need now, can get now, should get now, but even Google’s own official firmware site for Google’s own devices (Nexus, Pixel etc.) doesn’t list Android 8 for any of them. If it can’t even be download yet officially for Google’s “developer” devices, what hope do the rest of us have and how can you be sure it’s good for us?
Laurence Marks
Just wondering whether Sophos AV for Android is built with the “Storage Framework” and can be moved to the secondary SD card. As is the case with many second-tier phones, the primary SD card is tiny (5GB) and easily overflowed. The Play Store doesn’t give this information (except maybe in reviewer comments).