Yesterday at Black Hat USA 2017, Sophos released an in-depth report called “Ransomware as a Service (Raas): Deconstructing Philadelphia,” written by Dorka Palotay, a threat researcher based in SophosLabs’ Budapest, Hungary, office. It delves into the inner mechanics of a ransomware kit anyone can buy for $400. Once purchased, the bad guys can hijack and hold computer data for ransom in exchange for payment.
Yesterday, we focused on the marketing around Philadelphia and its leap from the Dark Web to promotion on the open web. Today, we focus on how the RaaS kit itself works.
Ransomware analysis
For a ransomware campaign to succeed, attackers must overcome four main challenges:
- Setting up a command-and-control server to communicate with victims,
- Creating ransomware samples,
- Sending the samples to the victims, and
- Managing the attacks (collecting statistical information, checking payment etc.).
When someone buys Philadelphia ransomware, they get an executable. This is the so-called Philadelphia headquarter. The headquarter helps the attackers in the first, second and fourth challenges during their attacks. We have seen examples where developers help their customers in the third step as well.
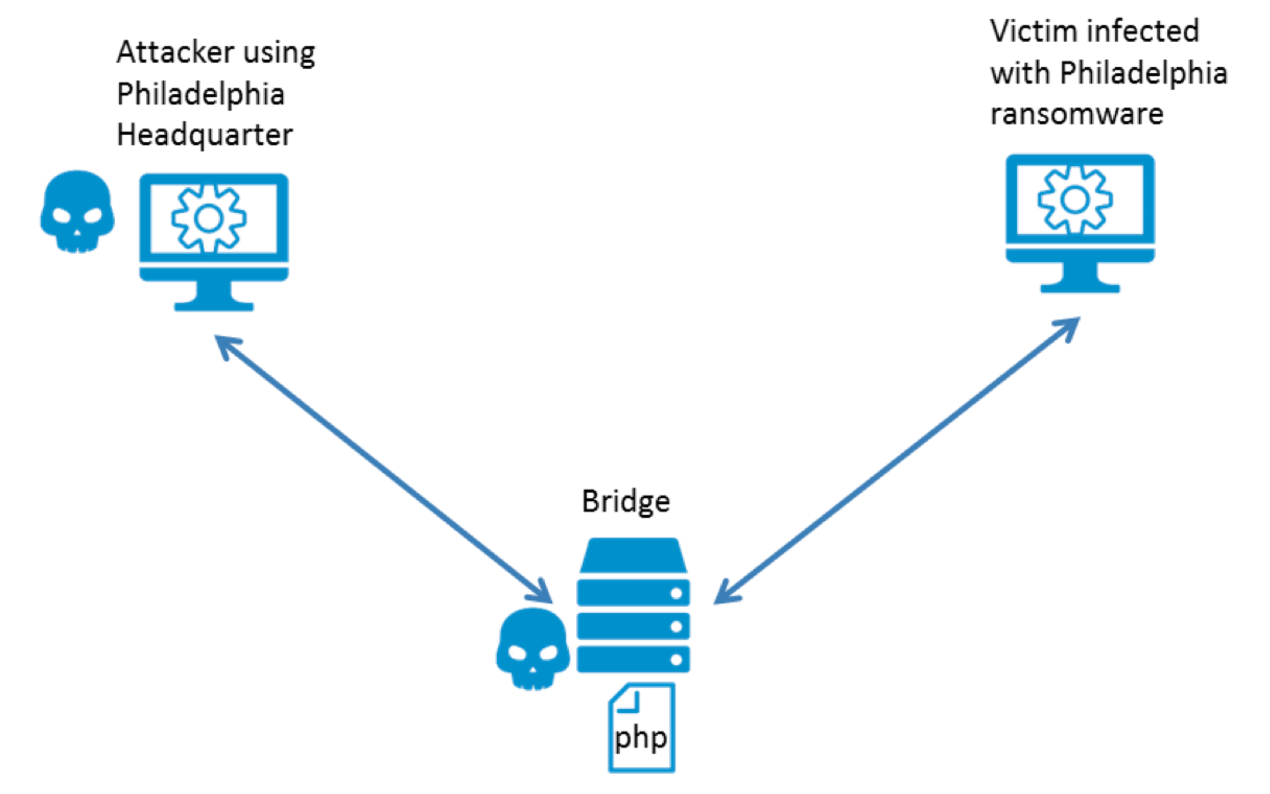
There are three systems involved in a Philadelphia ransomware attack. Two are under the control of the attacker and the third is the computer of the victim.
The attacker needs a computer on which to run the headquarter, and also needs a web server to communicate with the victims. In the following sections we explain what happens on these three systems during the preparation and successful execution of an attack. The figure below shows the three systems and the communication channels between them. The propagation of the malware is not included.
Track victims and (maybe) give mercy
In addition to the marketing, the product itself is advanced with numerous settings buyers can tailor to better target how they attack their victims, including options to “Track victims on a Google map” and “Give Mercy”. Tips on how to build a campaign, set up the command-and-control center and collect money are also explained. It’s all right there.
Ironically, the “Give Mercy” feature is not necessarily to help victims, but is instead there to help cybercriminals get themselves out of a sticky situation, says Palotay. It’s also there in case friends of an attacker accidentally find themselves ensnared or if the crooks want to test their attack.
The option to track victims on a Google map which sounds creepy, gives a glimpse into how cybercriminals determine the demographics of those they’ve deceived. This information could help them decide to repeat an attack, course correct the next attack or bail with the Mercy option.
Extra features for extra money
The Mercy and Google tracking options and other features in Philadelphia are not unique to this ransomware – but they aren’t widespread, either. These are examples of what’s becoming more common in kits and, as result, shows how ransomware-as-a-service is becoming more like a real-world software market. Palotay said:
The fact that Philadelphia is $400 and other ransomware kits run from $39 to $200 is notable. The $400 price tag, which is quite good for what Philadelphia buyers are promised, includes constant updates, unlimited access and unlimited builds. It’s just like an actual software service that supports customers with regular updates.
Philadelphia also has what’s called a “bridge” – a PHP script to manage communications between attackers and victims and save information about attacks.
Additional features that Philadelphia buyers can customize include the text of the ransom message that will appear to victims, the color of the text, whether the message appears before a victim’s data is encrypted, and “Russian Roulette,” which deletes some files after a predetermined timeframe. “Russian Roulette” is common in ransomware kits, and is used to panic users into paying faster by randomly deleting files after a number of hours.
Having customization options and bridges brings in more profit and adds a whole new dimension to cybercrime that could increase the speed of ransomware innovation, says Palotay.
In other RaaS cases SophosLabs examined, pricing strategies ranged from splitting a percentage of the ransom coming from victims with kit customers to selling subscriptions to dashboards that follow attacks.
Stolen code
The report also reveals that some cybercriminals have “cracked” or pirated Philadelphia and sell their own ripped-off version at a lower cost. While cracking is not new, the scale is interesting. Ready-made threats that don’t require attackers to know what they’re doing and are easily available for purchase are constantly evolving. Sophos expects this trend of upping the ante and committing fraud against fraudsters to continue. Palotay said:
It’s not uncommon for cybercriminals to steal one another’s code or build upon older versions of other ransomware, which is what we saw with the recent NotPetya attack. The NotPetya attack combined Golden Eye, a previous version of Petya, with the Eternal Blue exploit to spread and infect computers globally.
Defensive measures
For best practices against all types of ransomware, Sophos recommends:
- Back up regularly and keep a recent backup copy off-site. There are dozens of ways other than ransomware that files can suddenly vanish, such as fire, flood, theft, a dropped laptop or even an accidental delete. Encrypt your backup and you won’t have to worry about the backup device falling into the wrong hands.
- Don’t enable macros in document attachments received via email. Microsoft deliberately turned off auto-execution of macros by default many years ago as a security measure. A lot of malware infections rely on persuading you to turn macros back on, so don’t do it!
- Be cautious about unsolicited attachments. The crooks are relying on the dilemma that you shouldn’t open a document until you are sure it’s one you want, but you can’t tell if it’s one you want until you open it. If in doubt, leave it out.
- Patch early, patch often. Malware that doesn’t come in via document macros often relies on security bugs in popular applications, including Office, your browser, Flash and more. The sooner you patch, the fewer open holes remain for the crooks to exploit. In the case of this attack, users want to be sure they are using the most updated versions of PDF and Word.
- Use Sophos Intercept X, which stops ransomware in its tracks by blocking the unauthorized encryption of files.
- Try Sophos Home for Windows and Mac for free with family and friends.
-
Check out our webcast on RaaS, scheduled for August 23.

Leave a Reply