Ransomware as a service (RaaS) has been around for a while. But it has typically been found on the dark web. In recent months, its creators have grown more brazen about promoting it on the open web, and that has the potential to change everything.
Few RaaS kits exemplify this the way Philadelphia does.
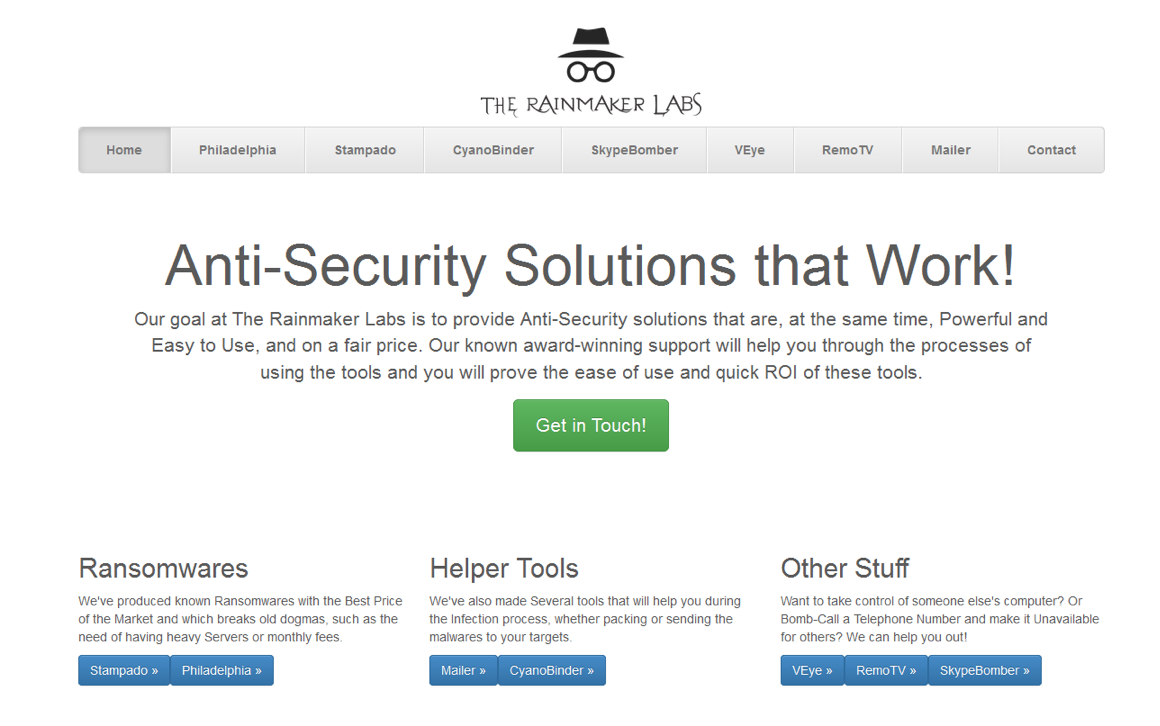
At Black Hat 2017 this morning, Sophos released an in-depth report on the subject, Ransomware as a Service (Raas): Deconstructing Philadelphia, written by Dorka Palotay, a threat researcher based in SophosLabs’ Budapest, Hungary, office. It delves into the inner mechanics of a ransomware kit anyone can buy for $400. Once purchased, the bad guys can hijack and hold computer data for ransom in exchange for payment.
Out in the open
The RaaS kit’s creators – The Rainmakers Labs – run their business the same way a legitimate software company does to sell its products and services.
While it sells Philadelphia on marketplaces hidden on the dark web, it hosts a production-quality “intro” video on YouTube, explaining the nuts and bolts of the kit and how to customize the ransomware with a range of feature options.
A detailed Help Guide, walking customers through set-up is also available on a .com website.
Their first RaaS product was Stampado, which they started to sell last summer for only $39. Based on their experiences by the end of 2016, they developed a much more sophisticated piece of ransomware called Philadelphia, which they currently sell for $389 on their website.
Customers include an Austrian teenager police arrested in April for infecting a local company. In that case, the alleged hacker had locked the company’s servers and production database, then demanded $400 to unlock them. The victim refused, since it was able to retrieve the data from backups.
While ransomware-as-a-service is not new, the glossy, overt marketing of a do-it-yourself ransomware attack is. Palotay said:
It’s surprisingly sophisticated what The Rainmakers Labs is trying to do here. Details about Philadelphia are out in the open on the world wide web as opposed to underground and secretive on the dark web, which is where most other ransomware kits are marketed. You don’t need a Tor browser to find Philadelphia, and the fact that it’s brazenly peddled is sobering and, unfortunately, indicative of what’s to come.
Sophos global security research head James Lyne agreed:
Philadelphia exemplifies the common marketing strategies and features that are making RaaS so popular. By combining the practices of the legitimate software industry, such as documentation, regular feature updates and friendly user interfaces, RaaS services have made it far more viable for those with intent but not technical skill to execute relatively high-quality attack campaigns.
Defensive measures
For best practices against all types of ransomware, Sophos recommends:
- Back up regularly and keep a recent backup copy off-site. There are dozens of ways other than ransomware that files can suddenly vanish, such as fire, flood, theft, a dropped laptop or even an accidental delete. Encrypt your backup and you won’t have to worry about the backup device falling into the wrong hands.
- Don’t enable macros in document attachments received via email. Microsoft deliberately turned off auto-execution of macros by default many years ago as a security measure. A lot of malware infections rely on persuading you to turn macros back on, so don’t do it!
- Be cautious about unsolicited attachments. The crooks are relying on the dilemma that you shouldn’t open a document until you are sure it’s one you want, but you can’t tell if it’s one you want until you open it. If in doubt, leave it out.
- Patch early, patch often. Malware that doesn’t come in via document macros often relies on security bugs in popular applications, including Office, your browser, Flash and more. The sooner you patch, the fewer open holes remain for the crooks to exploit. In the case of this attack, users want to be sure they are using the most updated versions of PDF and Word.
- Use Sophos Intercept X, which stops ransomware in its tracks by blocking the unauthorized encryption of files.
- Try Sophos Home for Windows and Mac for free with family and friends.
-
Check out our webcast on RaaS, scheduled for August 23.


Wilderness
“While it sells Philadelphia on marketplaces hidden on the dark web, it hosts a production-quality “intro” video on YouTube, explaining the nuts and bolts of the kit and how to customize the ransomware with a range of feature options.”
Why didn’t YouTube take the video down immediately? Are they helping authorities track down who has that account?
Mike
I’ll have to ask them to send me a brochure. “Click here to learn everything you need to know about ransomware.”