Editor’s note: Sophos customers can follow the technical updates in this Knowledge Base Article, which includes a list of the variants we’re detecting and blocking. This article will also be updated as new details emerge.
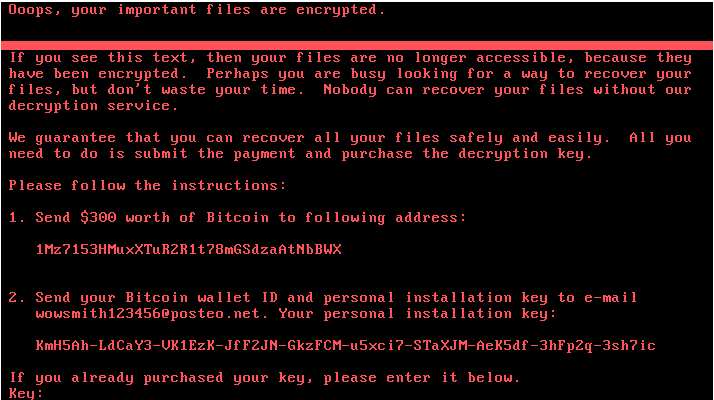
SophosLabs has determined that new variants of Petya ransomware (also known as GoldenEye) are behind the massive online outbreak that spread across Europe, Russia, Ukraine and elsewhere today. Others in the security industry are calling it PetrWrap.
What makes the new threat different is that it now includes the EternalBlue exploit as a way to propagate inside a targeted network. The exploit attacks the Windows Server Message Block (SMB) service, which is used to share files and printers across local networks. Microsoft addressed the issue in its MS17-010 bulletin in March, but the exploit proved instrumental in last month’s spread of WannaCry.
Petya also attempts to spread internally by breaking admin passwords and infecting other PCs on the network using remote admin tools. It can also spread internally by infecting network shares on other computers.
It does so by running credential-stealing code to break user account passwords and deploy ransomware. To infect remote computers, it comes bundled with a legitimate remote admin tool called PsExec from Microsoft’s SysInternals suite.
Sophos protection
Customers using Sophos Endpoint Protection are protected against all the recent variants of this ransomware. We first issued protection on June 27th at 13:50 UTC and have provided several updates since then to further protect against possible future variants.
In addition, customers using Sophos Intercept X were proactively protected with no data encrypted from the moment this new ransomware variant appeared.
Further to that, customers may choose to restrict the use of PsExec and other dual-use administrative tools on their network. Sophos Endpoint Protection provides PUA detection for psexec and other remote administration programs that don’t need to be available on every PC and to every user.
Defensive measures
Here’s what we urge you to do right now:
- Ensure systems have the latest patches, including the one in Microsoft’s MS17-010 bulletin.
- Consider blocking the Microsoft PsExec tool from running on users’ computers. A version of this tool is used as part of another technique used by Petya to spread automatically. You can block it using a product such as Sophos Endpoint Protection.
- Back up regularly and keep a recent backup copy off-site. There are dozens of ways other than ransomware that files can suddenly vanish, such as fire, flood, theft, a dropped laptop or even an accidental delete. Encrypt your backup and you won’t have to worry about the backup device falling into the wrong hands.
- Avoid opening attachments in emails from recipients you don’t know, even if you work in HR or accounts and you use attachments a lot in your job.
- Download the free trial of Sophos Intercept X and, for home (non-business) users, register for the free Sophos Home Premium Beta, which prevents ransomware by blocking the unauthorized encryption of files and sectors on your hard disk.
To avoid cyberattacks that sneak in via email, see:
- To defend against ransomware in general, see our article How to stay protected against ransomware
- To get a better understanding of phishing, read our explainer article
- To protect against JavaScript attachments, tell Explorer to open .JS files with Notepad
- To protect against misleading filenames, tell Explorer to show file extensions
- To learn more about ransomware, listen to our Techknow podcast
- To protect your friends and family against ransomware, try our free Sophos Home for Windows and Mac

Rick Burris
Are there Sophos signatures in place for this?
Kate Bevan
Hello! We’ve just updated our KBA, which is here, and should answer your questions https://community.sophos.com/kb/en-us/127027
jeoff
read the article it clearly explains this !
David
Is Sophos detecting this thread already?
Kate Bevan
Hello! Please see our freshly updated KBA https://community.sophos.com/kb/en-us/127027
steveoliver01
any new for your customers yet? have Sophos released an ide yet?
Kate Bevan
Hello – we’ve just updated our KBA, which is here https://community.sophos.com/kb/en-us/127027 – that should answer your questions.
Anonymous
These information sounds really good, BUT….
Our Servers and Clients were up to date and we use Sophos AV and SGN as well.
Now we are not able to boot up the clients and servers.
Be the force with you…
Micky3
Interesting …My devices use Sophos AV as well and were protected, however we did learn a lesson from the previous Eternalblue/Wanna episode and patched our systems also blocked exploit leveraging tools such as sys-internals etc. I’d suggest contacting Sophos to confirm you have your system correctly configured?
BTW SGN doesn’t protect against these sort of attacks it just ensures your data is encrypted if stolen.
kev whelan
Hi Bill
Notice in the above you do not mention Windows 7, which of course was the hardest hit O/S in the WannaCry attack.
Do you have any data on the profile of infected machines at this time?
Our current understanding, which may be inaccurate is that the infection vector is unpatched Office CVE-2017-0199, then spreads via MS17-010 (and other means, see below).
Since we are very paranoid and cynical types, we have had a look at the Github stuff (edited to remove link: please don’t post external URLs! – editor)
and notice that EternalBlue is not necessary for lateral infection because the system uses oldschool LSAdump priv stuff. Jus wondered what your thoughts are.
With the very best regards
anon
So I must:
(1) look up the Knowledge Base Article (always need education thanh you),
(2) turn off Windows PsExec service (already have no local network and turned off remote admin controls)?
(3) and not go to work on a computer in HR.
Windows users can block authorization for encypting data, files, and disk segments themselves. No?
Adam
Hi Bill, any chance you include psexec into Sophos Endpoint application control database as well so it can be blocked?
Bill Brenner
Adam, Dav: PsExec is detected as a PUA so Sophos Enterprise Console customers need to ensure they have that scanning enabled (it is by default) and that they haven’t then authorized PsExec. For Sophos Central customers t will be blocked already, they just need to check they haven’t manually added it to the exclusions list.
Hope that helps. If not, let me know and we’ll go from there.
Dav
You say “Consider blocking the Microsoft PsExec tool from running on users’ computers. A version of this tool is used as part of another technique used by Petya to spread automatically. You can block it using a product such as Sophos Endpoint Protection”.
I use Sophos Central for EndPoint, Servers with InterceptX but I dont find how to block PsExec !
Anonymous
Hi Dav,
PSExec is blocked by Sophos Endpoint Protection as a PUA, On Sophos Central PUA protection is on by default so as long as you don’t have an exclusion in place for PSExec, you’ll be receiving this protection. Please see the KBA for more details
Cheers
Chris McDonnell
In the article you mention that Sophos Intercept X users are protected from this ransomware but is that definitely the case seeing as the actual encryption takes place during boot?
Anonymous
The encryption doesn’t happen during boot. it happens before the boot. file and mbr. Then the machine will reboot automatically, which is generally when you would notice what has happened. Intercept X stops both types of encryption.
Paul Ducklin
The file encryption happens before the reboot, using regular Windows API calls. CryptoGuard blocks that.
Petya’s sector encryption doesn’t happen immediately, as you say, but it requires the boot-time scrambling code to be written to the boot sector first, and WipeGuard stops that. So the sector scrambling never happens because the scrambling code never gets written in the first place.
There’s a bit more on this stuff here:
https://nakedsecurity.sophos.com/2017/06/28/new-petya-ransomware-all-you-wanted-to-know-but-were-afraid-to-ask/
Edsin
Hi,
News keep coming about new ways of preventing from spreading ransomware once your network is being compromised. One way is to create read-only file (perfc) under Windows directory. Is sophos endpoint protection able to determine this files(created by users – your costumers) are ok, so it does not delete them?
Thanks,
Regards
Paul Ducklin
The immunisation file you create called “perfc” won’t be malware – it could even be zero bytes, or just a text file saying, “Ha!” So it won’t be detected as malware, and will indeed be left alone. FWIW, the “perfc” immunisation trick depends on the malware DLL name itself being “perfc.something”, so this is a version specific trick…but I can’t see it doing any harm, because there isn’t an existing file called “perfc” that you need to overwrite to make this work. So the placeholding “perfc” file should be irrelevant except in this context…
Steve
How do I block PsExec on our network ?
I have exempted it once, which allows it – but now am being told to prevent it
Edsin
Go to your Anti-Virus and HIPS policy that you have, right click on View/Edit Policy. In window that opens, click “Authorization…”, there on the first tab you will see “Known adware and PUAs” and “Authorized adware and PUAs”. Move “PSExec” from Authorized PUAs by selecting it and pressing “Remove” button. Click OK twice and wait for policy to apply. Repeat steps for every Anti-Virus and HIPS policy that you have, if you have multiple, except for ones you need PSExec.