Thanks to Rowland Yu of SophosLabs for his behind-the-scenes work on this article.
Several popular Android apps in Google Play are rigged with a third-party library that continuously pops up ads even if the user tries to force close them.
SophosLabs discovered the library earlier this week and detects it as App/MarsDae-A. So far, more than 40 apps on Google Play use the library, which has been downloaded up to 6 million times. Sophos protects its customers from these apps.
The library supports Android 2.3 through Android 6, along with Samsung, Huawei, Meizu, Mi and Nexus devices. Its primary function is to keep the adware alive even if the user attempts a force close or memory scrub.
- Related article: SophosLabs report examines Top 10 Android malware
SophosLabs found a total of 47 apps in Googe Play that include the MarsDae library. Google Play has removed some of them, but many remain. Here is the list of package names:
cn.etouch.ecalendar.life com.aimobo.weatherclear com.ali.money.shield com.anti.block.porn.safebrowser com.app.fast.boost.cleaner com.app.wifi.recovery.master com.baiwang.facesnap com.block.puzzle.game.king com.booster.ram.app.master.clean com.card.game.bl.plugintheme21 com.card.game.bl.plugintheme22 com.card.game.bl.plugintheme23 com.cardgame.solitaire.sfour com.clean.phone.boost.android.junk.cleaner com.cleaner.booster.speed.junk.memory com.color.paper.style com.corous360.zipay com.desk.paper.watch com.exact.digital.ledcompass com.free.sudoku.puzzle com.freegames.happy.popcandy com.freegames.popstar com.freegames.popstar.exterme com.gmiles.alarmclock com.gmiles.switcher com.insta.browser com.listen.music.pedometer com.ljapps.wifix.recovery.password com.mg.callrecord com.mola.tools.mbattery com.mola.tools.openweather com.mx.cool.videoplayer com.news.boost.clean com.ojhero.nowcall com.phonecooler.battery.cleaner.wifimaster com.picture.photo.editor com.powercleaner com.red.music.audio.player com.riti.elocation.driver com.samll.game.puzzle.plus com.smartx.flashlight com.tool.powercleanlite com.tool.videomanager com.tools.freereminder com.wise.trackme.activity org.mbj.filemanager org.mbj.sticker
What happens
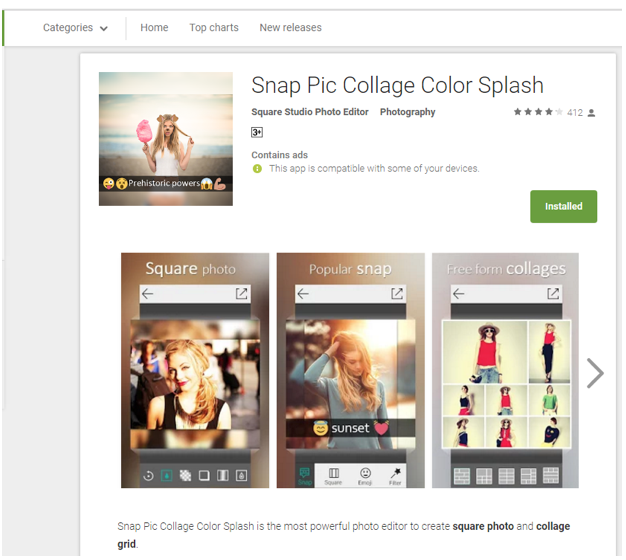
In the example below, we see the library used in an app called “Snap Pic Collage Color Splash.” The app has been downloaded from Google Play more than 50,000 times.
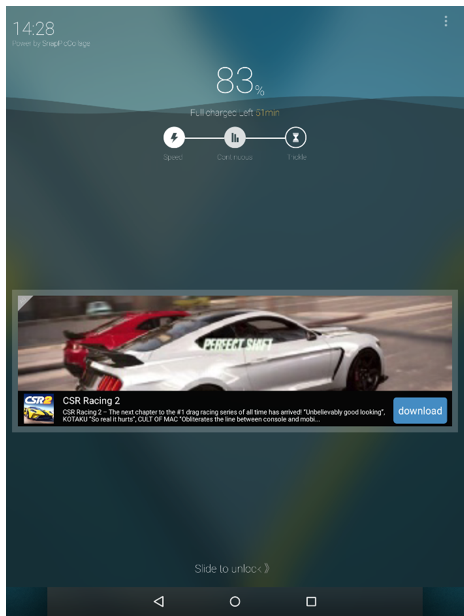
Once the app is installed, it will pop up ads on the user’s home screen like this:
Even if you force stop the app from system settings, the ads will resume after few seconds.
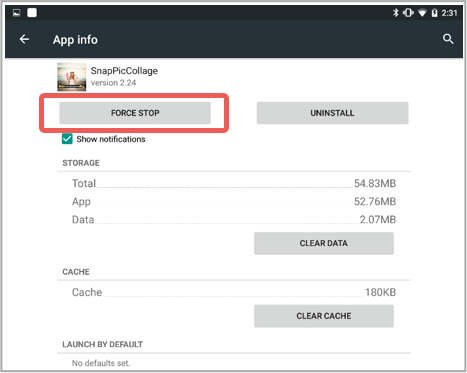
How it works
Once dropped on an Android 5 and 6, the library repeats a series of steps to keep the ads running.
- It runs code that kicks off a number of processes.
- It creates a file, then locks it.
- Each process creates another file. For example, Process A creates a2 and repeatedly checks if Process B has created file b2, and vice versa.
- If Process A finds file b2, it means Process B has started and locked file b1. Process A can delete file b2. Process B will do the same thing for file a2.
- Process A keeps monitoring the lock status of file b1 while Process B monitors file a1. If any file is unlocked, it means the related process is dead. Then anther process can restart it again.
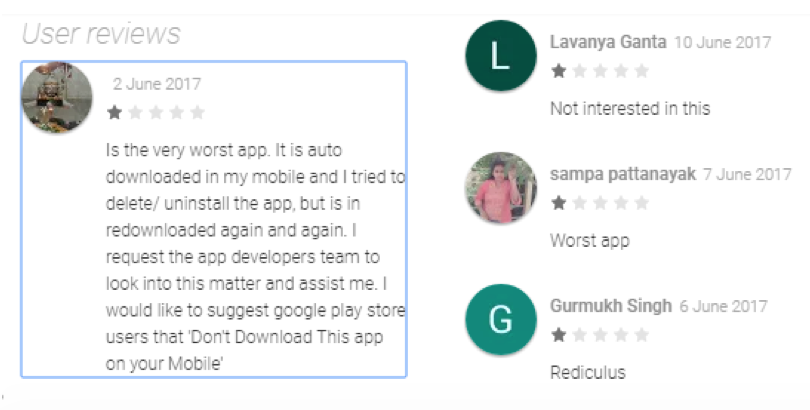
As clever as the technique may be, all it does in the long run is ruin each app’s reputation on Google Play. Annoyed users have made their unhappiness known:
PUAs on Google Play
This is just the latest in a growing list of PUAs (potentially unwanted apps) SophosLabs has found on Google Play. Other recent examples include:
- Star Hop and Candy Link, which look like a couple of harmless games but hide malware that can switch on the device’s wifi and pummel the victim with spam.
- Android XavirAd and Andr/Infostl-BK, which collects the user’s personal information, including email address, and sends them to a remote server.
- Super Free Music Player, which uses sophisticated techniques formerly found in BrainTest malware to bypass detection by Google and security researchers.
Defensive measures
As we mentioned above, SophosLabs has identified and protected Sophos users against this adware library.
Our advice: If you see these apps in Google Play, don’t download them. We’ll continue working with Google to get the remaining apps removed.
The continued onslaught of malicious Android apps demonstrates the need to use an Android anti-virus such as our free Sophos Mobile Security for Android.
By blocking the install of malicious and unwanted apps, even if they come from Google Play, you can spare yourself lots of trouble.

david tua
Awesome reminder article. It was a concern brought up long ago about phone app stores and the stuff bad guys try to pull when you try to get one simple app. Glad there is at least one company is looking out.
Mahhn
Shouldn’t Google notify people that have downloaded malicious apps after it’s discovered/removed from the Play store? (since they have your contact info)
CMaxo
To be honest, the risk of having this kind of Adware to be installed on your mobile phone or tablet is really high whenever you play MOST of the free-to-play online games available on Google Play.
This is due to one major flaws that is willingly ignored by many publishers & developers : Whenever you allow “anything” to be loaded from a remote server in your app, your app can act as a full open door to anything. This is because it’s impossible for any Antivirus to detect the invasion from within an authorized App. A reminder that games apps casually run many Java & C# or C++ scripts and having such script in the advertisement loaded from a server isn’t scanned nor detected by the antivirus.
This is due to the nature of how antivirus works on mobiles. There’s an active protection only when new apps or data stream (like browser) are incoming. Within Apps, all goes around and any action aren’t fully scanned because it would not only take too much memory (considering the games already take plenty of RAM), but would also drain the battery dry in half an hour.
The best kind of situational-example I can give is that Mobile Apps are now like the old days of Javascript & Advertisement on PC’s browser. Do you remember (if you’re old enough) when Google Ads was filled by so many adware/virus filled advertisements (through a tiny javascript inserted in the Ads) that you could catch a virus from most of the website around just by surfing the web and being unlucky? That’s the “same” process we’re living again with mobile Apps. Back then, antivirus were doing mostly a post-active job of finding and removing virus & malwares “after” being detected on the HDD. If a virus or malwares was able to “stay hidden”, the antivirus couldn’t do a thing to stop it. Same thing when an App load an advertisement that has some kind of javascript-based injector into its data. (Remember, games apps has permission to edit and write data on in the memory. That’s a “ticket to it all” for any apps.)
Where does this lead us? Well, with the raise of (indie) independent development, many games are made by people who don’t fully understand the things in their games. They uses anything given to them that seems easy to implement as long as it seems to works well from a standalone point. For example, a free-to-play game will bring money from 2 things : Advertisement & Cash-shop. For the advertisement, the developers (or it could be decided by the publisher if not the same), might run some kind of private servers where the ads’ data is fetched, but let’s be honest… they all goes with the easy way of using the Google Play Ads API. That API is the equivalent to Google Ads from the old days : It’s a semi-open server that allow “anyone” to put their own ads (including javascripts functions) which is overseen by a security software. Whenever a game has an advertisement, it send a fetching request with an unique key. That key act as both an identifier for the source (which determines who get the ads revenues) and also as a quick access to the kind of ads authorized. (Some might agree for “anything except mature content” while some other might agree to “Anything from Google Play” or any other Google services.) Then the Google servers send back a fetching address that allow the app to load the Ads content. It’s a 2-steps easy process that requires almost no understanding of how to fetch and insert ads in your game… Except it’s only secured against immediate threat such as a virus/adware/malware directly placed IN the ads (which would be stupid to do).
Anonymous
Hai