A Congressional task force has put out a report looking at what it will take to improve cybersecurity in the problem-plagued healthcare industry.
One thought? The Feds and the industry might want to set up some kind of cash for clunkers program to financially prod healthcare organizations into clearing out insecure, legacy medical systems and equipment.
“Cash for clunkers” was the common name for a 2009 US government program that involved giving Americans vouchers to get out of our polluting fuel hogs and into higher-efficiency new cars. The program paid out from between $2,500 for a new car that was 7 mpg more efficient than a trade-in on up to $4,500 for one that was 13 mpg more efficient.
Translate that financial incentive to medical devices: that’s just one of a host of action items and recommendations that came from the Health Care Industry Cybersecurity Task Force in its report, which it released to members of the Senate and House of Representatives on Friday.
There are incentive models already out there that could serve as models. The report mentioned the Montreal Protocol, which aims to protect the Earth’s ozone layer, and the Federal IT Modernization Fund, which subsidizes rapid IT modernization.
Why do we need to buy up all the medical clunkers? Because healthcare cybersecurity is pretty sickly, for various reasons besides legacy devices and technologies, according to the report and to plenty of headlines that back it up.

One case in point is WannaCry. The recent ransomware outbreak took a heavy toll on UK hospitals, with phone lines and IT systems held hostage.
As we came to find out, the attack took advantage of a Windows vulnerability Microsoft had released a patch for months earlier. WannaCry also revealed (although failed to effectively exploit) the surprising number of no-longer-supported Windows XP machines still used in the NHS (National Health Service).
So why the glacial progress in upgrading old Windows machines and patching newer ones? Some places are stuck on older Windows operating systems: they may lack the security personnel, the money to upgrade, and/or their legacy systems simply aren’t yet up to working with the likes of, say, Windows 10, for example.
Another problem in healthcare cybersecurity is a lack of secure development practices among medical device makers. The report urged device makers to get up to speed with secure development and says they should be encouraged to publish a “bill of materials” that accounts for all hardware and software used in a device, including third-party software.
After all, how can you secure something if you’re not even sure what it’s got running under the hood? Recommendation 2.2 from the report:
Having a “bill of materials” is key for organizations to manage their assets because they must first understand what they have on their systems before determining whether these technologies are impacted by a given threat or vulnerability. Moreover, this transparency enables health care providers to assess the risk of medical devices on their networks, confirm components are assessed against the same cybersecurity baseline requirements as the medical device, and implement mitigation strategies when patches are not available.
Take pacemakers, for example. A recent study found there are more than 8,000 vulnerabilities in the code that runs in seven analyzed pacemakers from four manufacturers.
And that’s just a subset of the overall medical device scene, in which devices have scarcely any security at all. A second, separate study that looked at the broader market of medical devices found that only 17% of manufacturers have taken serious steps to secure their devices, and only 15% of healthcare delivery organizations (HDOs) have taken significant steps to thwart attacks.
The report released to Congress on Friday by the Task Force came to similar conclusions. The Task Force collected 151 potential risks across what it calls the “value chain.” It provided a table that breaks those risks down by the categories of confidentiality, availability, integrity, and patient safety:
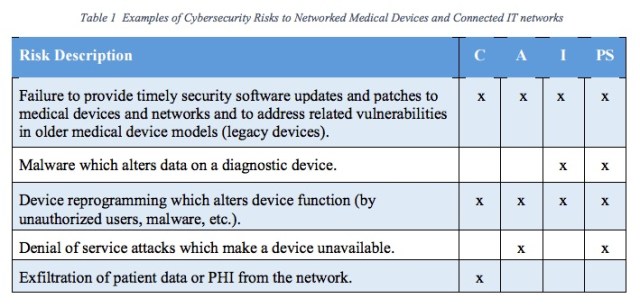
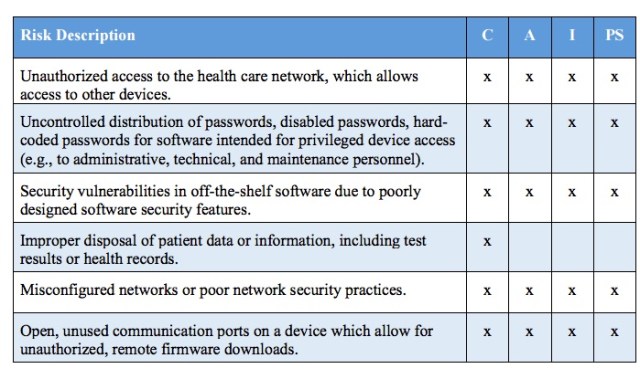
It’s a “life or death issue for both device manufacturers and healthcare delivery organizations, according to Dr. Larry Ponemon, co-author of a study entitled Medical Device Security: An Industry Under Attack and Unprepared to Defend.
One of the members of the Health Care Industry Cybersecurity Task Force – which Congress established with the passage of the Cybersecurity Act of 2015 in March 2016 – is Joshua Corman, the Director of the Cyber Statecraft Initiative at The Atlantic Council and a founder of the group I Am The Cavalry.
Corman told The Security Ledger that many healthcare organizations rely heavily on poorly secured, internet-connected medical devices. But maybe they shouldn’t, given that they’re small, cash-strapped outfits that often don’t have the security chops to secure them, Corman said:
Healthcare is target rich and resource poor. If you can’t afford to protect [internet-connected healthcare equipment], you can’t afford to connect it.

Marie
Cash for Clunkers, what a farce. All the US gov’t did was get folks into new cars that they couldn’t afford while crushing perfectly good vehicles. Now there is a shortage of affordable used cars. Typical gov’t blundering claptrap