Thanks to Ferenc László Nagy, Jason Zhang and Jagadeesh Chandraiah of SophosLabs for the behind-the-scenes work on this article.
A fake copy of the popular Chinese game King of Glory is being used to spread ransomware and uses a warning screen that mimics one used in last month’s WannaCry outbreak.
Aside from that bit of window dressing, this ransomware has none of WannaCry’s functionality. But since King of Glory has millions of users, it’s a serious problem in its own right.
SophosLabs is investigating the ransomware, which has sparked warnings like this in Chinese forums and websites:
![[Emergency release] domestic posing as "king of glory" auxiliary blackmail virus](https://news-sophos.go-vip.net/wp-content/uploads/sites/2/2017/06/image11.png)
First signs of trouble
After running the initial app, it hides its original icon and then reappears as “Lycorisradiata” (Red Spider lily):

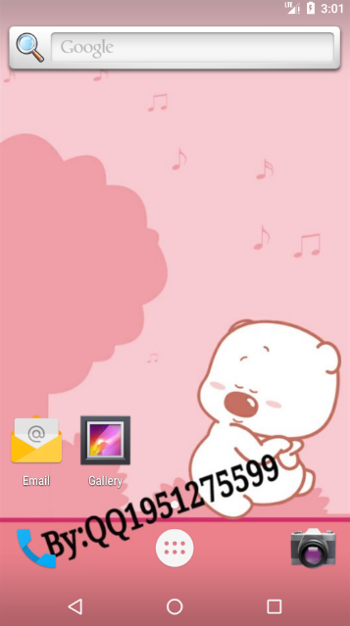
The home screen changes, with an ID possibly related to the malware author:
Infection and encryption
The ransomware encrypts the files on the device and renames them, adding long and unreadable file extensions like this:
![]()
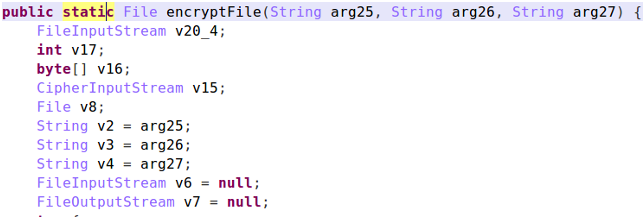
The encryption code itself looks like this:
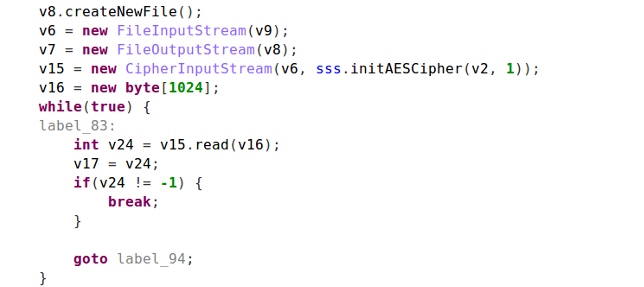
The ransomware tries to avoid encrypting system files (because a victim can’t pay a ransom with a broken phone) by looking for filenames that including strings like /., android and com..
The look of WannaCry
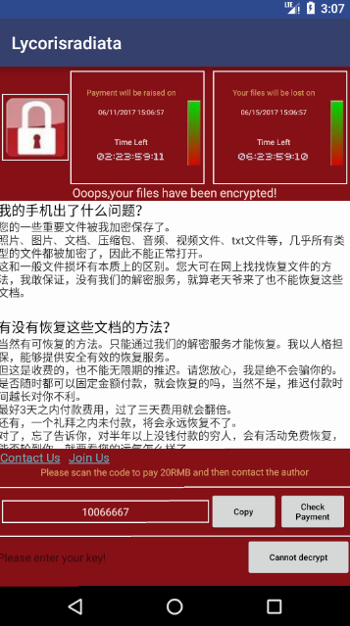
Up pops a ransomware message much like the one seen on WannaCry-infected Windows platforms. Instead of being asked for bitcoin though victims are asked for 20 RMB:
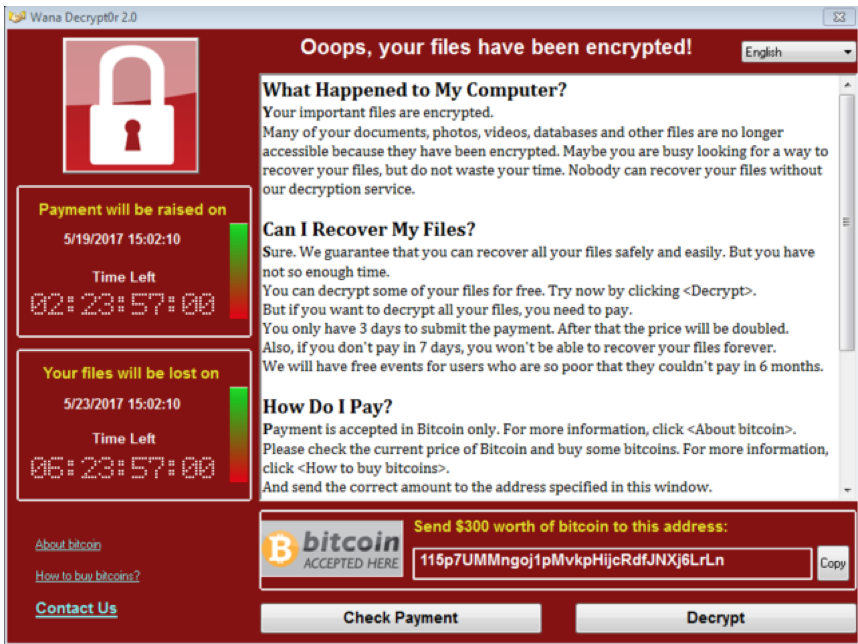
And, for comparison, this is what WannaCry’s warning message looked like:
The fake game aims to spook the user with this threatening message:
We strongly suggest that, to avoid unnecessary troubles, please stop any anti-virus software and don’t uninstall or delete this software before the recovery ends. You might not be able to recover your data after your payment in case the software gets deleted due to whatever reason.
The attacker directs the victim to make pay the ransom through the China-based Wechat, Alipay and QQ payment methods.
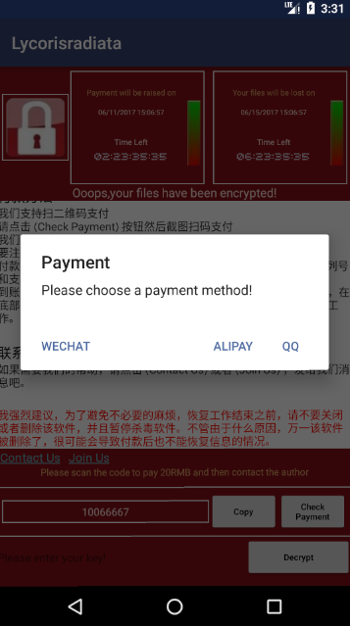
We don’t know why the criminals behind this software copied WannaCry’s interface – perhaps they were just lazy, or maybe they were trying to cash in on its notoriety.
WannaCry hijacked hundreds of thousands of computers across the globe last month. SophosLabs has determined that it probably didn’t start the way a typical ransomware attack does, i.e. as a phishing email carrying a malicious attachment or link the user is tricked into opening. Instead, the outbreak was a worm from start to finish, with a ransomware payload.
In the case of this latest Android ransomware, the only real similarity is the look. While WannaCry exploited a Windows zero-day and spread because of its worm-like capabilities this ransomware was spread via internet gaming forums and downloaded and installed by unsuspecting gamers.
Can the real WannaCry spread on Android?
In the weeks since the WannaCry outbreak, we’ve been asked if Android devices are vulnerable. The answer is no, for a simple reason: WannaCry targets Windows.
SophosLabs offered up an explainer of that in a recent article.
How to protect yourself
Sophos customers are protected from this ransomware, which SophosLabs detects as Andr/Ransom-EAC. Additionally, users can protect themselves by following this advice:
- Stick to Google Play. It isn’t perfect, but Google does put plenty of effort into preventing malware arriving in the first place, or purging it from the Play Store if it shows up. In contrast, many alternative markets are little more than a free-for-all where app creators can upload anything they want, and frequently do.
- Consider using an Android anti-virus. By blocking the install of malicious and unwanted apps, even if they come from Google Play, you can spare yourself lots of trouble.
- Avoid apps with a low reputation. If no one knows anything about a new app yet, don’t install it on a work phone, because your IT department won’t thank you if something goes wrong.
- Patch early, patch often. When buying a new phone model, check the vendor’s attitude to updates and the speed that patches arrive. Why not put “faster, more effective patching” on your list of desirable features, alongside or ahead of hardware advances such as “cooler camera” and “funkier screen”?

charlyy
This ransomware will make lot of people cry :-( , good find
kylo
people cry? you mean infect lots of people ?
sndy23@gmail.com
hand shake icon is also from wanna cry, love it how these guys have lifted everything off the other one :-)