Ransomware is among the topics at this week’s InfoSec Europe 2017 gathering this week in London. It’s been with us for some time and is considered old news by many security practitioners. But it remains a vexing problem for companies and continues to dominate many a conference agenda.
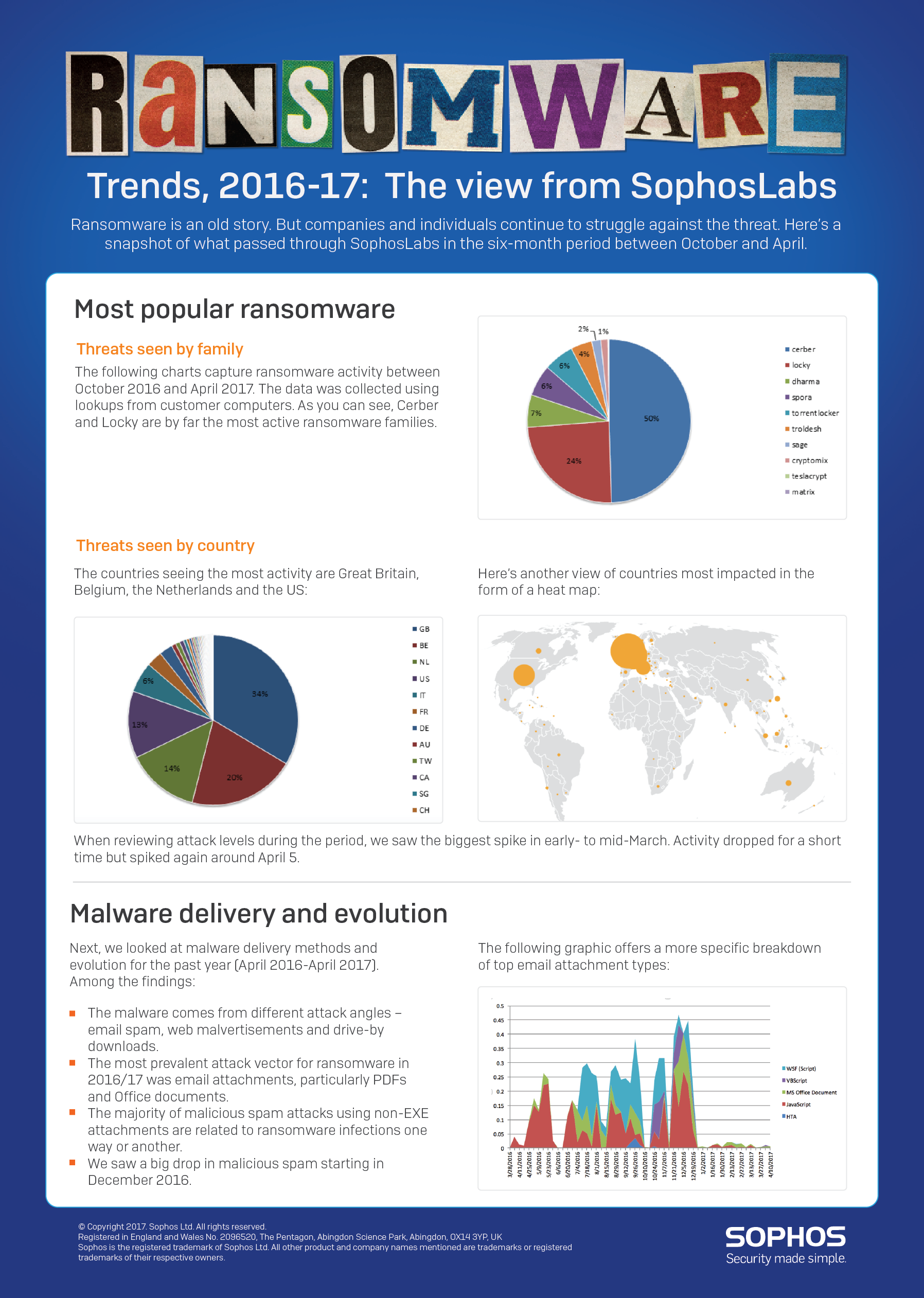
SophosLabs recently looked at the most prolific ransomware families and attack vectors over a six-month period and boiled it down to the graphic below.
In this article we break down the statistics, review some of the ransomware-themed events on the InfoSec agenda and offer up some defensive measures.
Statistics from SophosLabs
The statistics below cover the six-month period between October 2016 and April 2017. It does not include mid-May’s WannaCry outbreak, which came later. (We’ll focus more specifically on WannaCry in an article tomorrow.)
The data was collected using lookups from customer computers. First, labs looked at specific ransomware families and found that Cerber and Locky were by far the most active. Cerber accounted for half of all activity during the period, and Locky made up a quarter of it.
Cerber has undergone many mutations designed to circumvent sandboxes and antivirus. One version spread via spam emails disguised as a courier delivery service. Locky, meanwhile, has a history of renaming the important files of its victims so that they have the extension .locky. Like Cerber, its tactics and make-up have morphed over time.
The countries seeing the most ransomware activity are Great Britain, Belgium, the Netherlands and the US, and the biggest spike of activity came in early- to mid-March. Activity dropped for a short time but spiked again around April 5.
Next, labs reviewed malware delivery methods and evolution for the past year (April 2016-April 2017) and discovered, among other things, that the malware came from different attack angles – email spam, web malvertisements and drive-by downloads.
The most prevalent attack vector for ransomware was email attachments, particularly PDFs and Office documents.
The majority of malicious spam attacks using non-EXE attachments are related to ransomware infections one way or another.
We saw a big drop in malicious spam starting in December 2016.
The exact percentages are captured here (for a closer view, click on various parts of the graphic and use the magnifying glass function):
On the InfoSec agenda
Conferencegoers have multiple chances to learn more about ransomware at InfoSec 2017. Sophos Global Head of Security Research James Lyne is discussing the threat during the presentation Risks, Threats & Adversaries: What (or Who) Should You Be Worried About?
Lyne’s presentation looks at the evolution of ransomware as a service (RaaS) and tackle the question of whether or not victims should pay the ransom. Naked Security has shied away from moralizing about whether it’s always unacceptable to support criminality by paying up, even if you are in a difficult position. But we’ve made two suggestions in the past:
- Don’t pay if you can possibly avoid it, even if it means some personal hassle.
- Take precautions today (e.g. backup, proactive anti-virus, web and email filtering) so that you avoid getting into a position where you ever need to pay.
As well as James Lyne’s talk, there are plenty of ransomware-based talks and events to choose from if you’re heading for InfoSec.
How to protect yourself
The trick, of course, is to keep from getting put in this no-win situation in the first place. We regularly offer advice on preventing (and recovering from) attacks by ransomware and other malware.
Here are some links we think you’ll find useful:
- To defend against ransomware in general, see our article How to stay protected against ransomware.
- To protect against JavaScript attachments, tell Explorer to open .JS files with Notepad.
- To protect against misleading filenames, tell Explorer to show file extensions.
- To learn more about ransomware, listen to our Techknow podcast.
- To protect your friends and family against ransomware, try our free Sophos Home for Windows and Mac.
Techknow podcast — Dealing with Ransomware:


Leave a Reply