Target: Expect More. Pay Less.
Sound familiar? That’s what the US retailer’s tagline is supposed to say.
As opposed to “All Products In One Place”, the tagline glued to a malicious ad that managed to squirm its way to the top of Google search results for Target and then to redirect visitors to a tech support scam.
According to Bleeping Computer, the dodgy campaign was spotted on Friday by a US user who posted his observations to a StackExchange thread.
The user said that a coworker had searched for “Target”, clicked the top result – which was an ad – and was redirected to a phishing page that was rigged up to look like a Microsoft tech support page that wanted him to call a “tech support number”.
The user tried it on his own computer, on a different network, and got the same results. Curiously, hovering over the link should have shown where it really went to, but in this case, it did no such thing, he said:
When I hover over the link, both links show “www.target.com” at the bottom, but clicking the ad link takes you to a malware page and the second link (first search result after the ad) takes you to the real Target.com page.
This is what it looked like, he said:
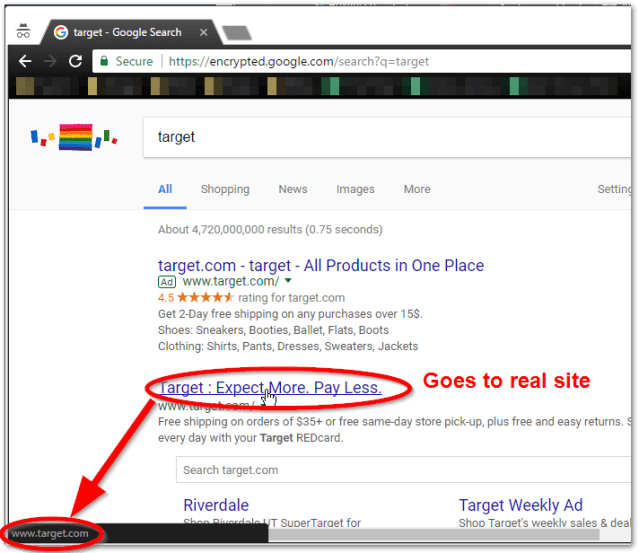
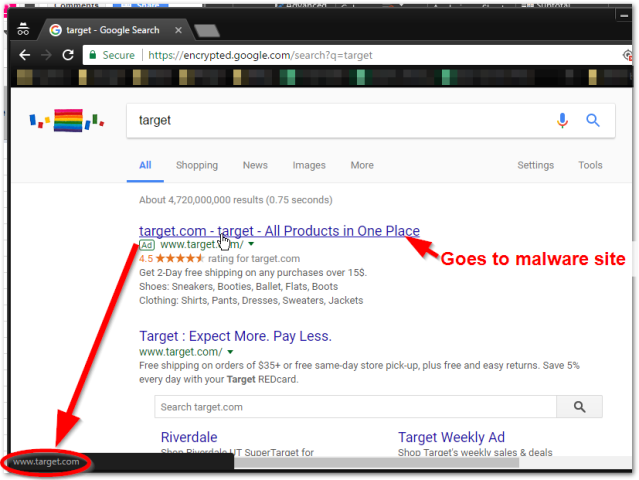
The malicious ad took advantage of a feature of the Google Ads service that allows ad publishers to display one URL but redirect users to another link.
In the bogus tech support ad, the displayed link was target.com but users were redirected to tech-supportcenter.us.
How did that get past Google’s ad quality control service? As the company explains, it allows redirects within the same domain, but cross-domain redirects are forbidden and will result in ad disapproval.
The idea is to allow companies to use proxy pages: as in, exact copies of live, functioning websites used in place of the original site, for the purpose of isolating advertising traffic from all other website traffic.
Such proxies are hosted on a separate domain from the original site (and may contain a different business phone number), but because they provide the same user experience as the original site, they’re permitted to use the original website as the display URL.
Users who clicked on the rogue Target ad might have expected to get more and pay less, but what they got instead was your typical scam, made to look like a Microsoft support page. The scammers were urging users to call a phone number to remove a non-existent “HARDDISK_ROOTKIT_TROJAN_HUACK.EXE” file.
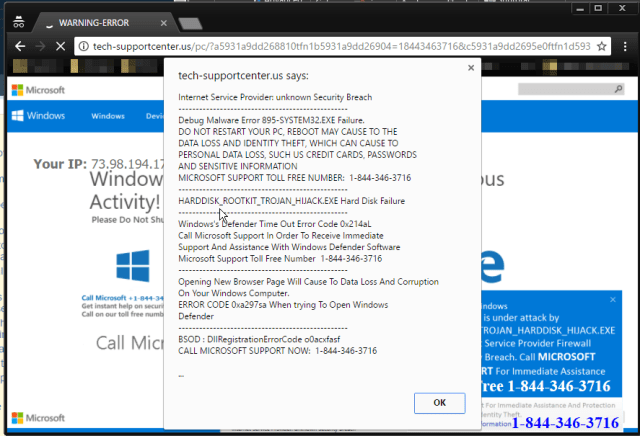
As a StackExchange user pointed out, Google has strict destination requirements for ad links. Ads have to accurately reflect where the user is being directed, and Google disallows redirects from the final URL that take the user to a different domain.
But there are loopholes, including that Google doesn’t control third-party redirectors, and those redirectors can go rogue. An example of an allowed redirect is a company, such as an AdWords Authorized Reseller, using proxy pages.
And then there times when those redirectors go bad. An example, from StackExchange:
After Google has vetted and approved their ads, [third-party redirectors] could simply start redirecting to a different domain without immediately getting noticed by Google. It’s possible that, in [this tech support scam] case, attackers managed to compromise one of these third-party services and pointed their redirects to the scam site.
We’ve seen this happen recently: In February, a bad ad perfectly spoofed to look like a legit Amazon ad sent anybody who clicked on it to a Windows support scam.
We’ve also seen the same type of scam via a Walmart ad, according to user complaints:
came across this same scam on Walmart ad. Lots of scams and clickbait on Google these days.
— Paul Carpenter (@offlineinfl) June 5, 2017
Bleeping Computer reports that the malicious Target redirect ads aren’t up anymore, and the tech support site is also down.
What to do?
If you want to avoid rogue, Google-thwarting ads like this one that sneak up to the top of search results and then fling visitors into tech scam land when they click, the first tip is a no-brainer:
- Don’t click on anything that’s labelled “AD” and pops up right at the top of search results. But if you do click…
- If you receive a web popup or ad urging you to call for support, ignore it.
- If you really do need help with your computer, ask someone whom you know, and like, and trust.
- When searching for Target – or Walmart, or Amazon, for that matter – remember that you don’t need to use Google. Simply go straight to Target.com, Amazon.com or Walmart.com.
DEALING WITH FAKE SUPPORT CALLS
Here’s a short podcast you can recommend to friends and family. We make it clear that these guys are scammers (and why), and offer some practical advice on how to deal with them.
(Originally recorded 05 Nov 2010, duration 6’15”, download size 4.5MB)

LucusLoC
I do not use an ad blocker, and I do not click on any ad links. I know this sucks for content creators that rely on ads, but as long as ads are a reliable vector for scams and viruses I will continue to make every effort to ensure they do not appear on any of my machines. Since ads seems to be moving to more complex forms this does not look like a vector that will ever be adequately secured, so I will likely never see ads again if I can help it.
Larry Marks
I’m disgusted that Google couldn’t bother to program a filter to prevent this redirection. Just as I’m displeased that they can’t be bothered to run a quality A/V on Play Store downloads. What happened to “Don’t Be Evil”?
Undecided on whether to switch to Bing or see if I can set uBlock Origin to hide the Ad results.