Thanks to Chen Yu, Rowland Yu and William Lee of SophosLabs for the behind-the-scenes work on this article.
There’s been a lot of focus lately on the so-called “Judy” adware found hiding in more than 40 Android apps on Google Play – although they have since been banned from the store. It uses the devices it infects to spread a massive volume of fraudulent ad clicks.
SophosLabs detects all Judy samples as App/Adload-NL and has blocked its command-and-control server. Sophos users are therefore protected.
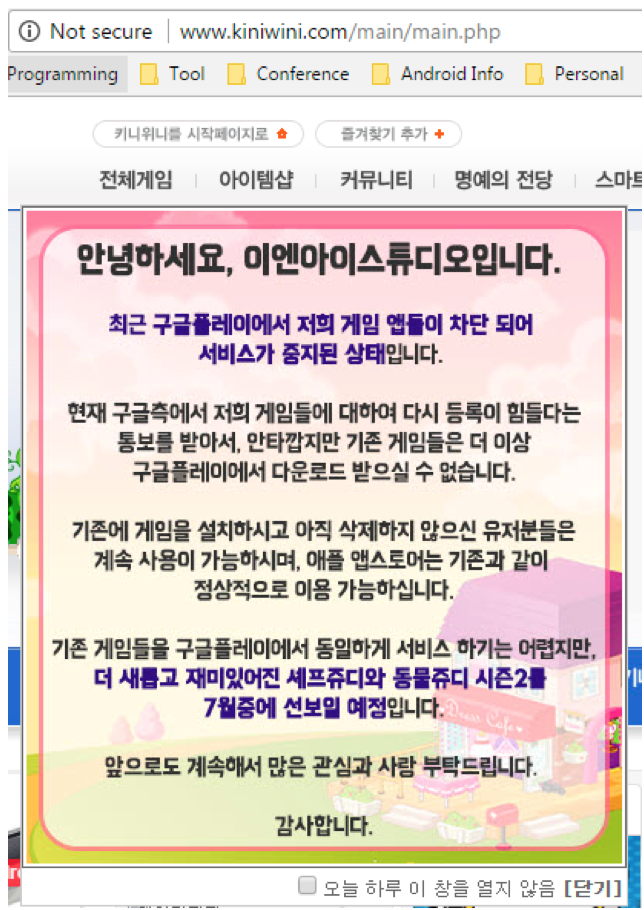
The Korean company behind the apps has acknowledged the adware and released the statement below on the company website. Translated, it says:
Customers cannot download our Android apps from Google Play as they are blocked by Google. New Android versions will be released in July.
Judy serves as a reminder that:
• Potentially Unwanted Apps (PUA) are a growing problem on all platforms, whether it’s Windows, Android or Mac.
• Separating PUAs from malware on Android is hard. It’s tricky on Windows, but Android is even more complicated.
What follows is a look at what SophosLabs found. Ultimately, Judy breaks Google policies and Android users need to be aware of it. But in terms of damage, the biggest problem is its unethical use of bandwidth.
Technical analysis
When examining the adware samples, SophosLabs noticed that:
1. The apps contained a net.shinhwa21 library and had connected to its command-and-control server in March, 2016 or even earlier.
They seem two have two bits of similar code:
• feae890d6a5cf1ebdcb4b5d25625bf1df5b922ab, added to Google Play in March 2016
• b622747335e9dce50ed4cb4d859a2ca3d88dfacb, added to Google Play in Apr 2017
They obtain a URL, user agent string, rReferer, and javascript to run in webview from the command-and-control server.
2. The publisher, ENISTUDIO corp., released 285 apps on Google Play, but most of them are confirmed with the net.shinhwa21 library app.
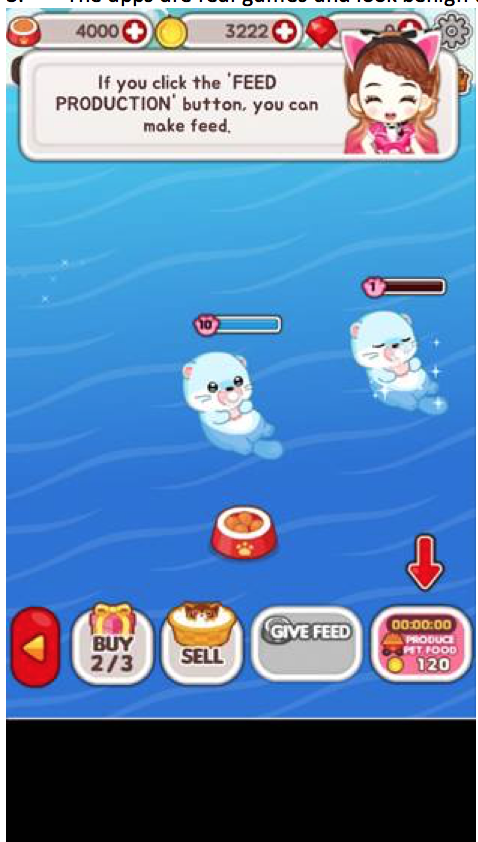
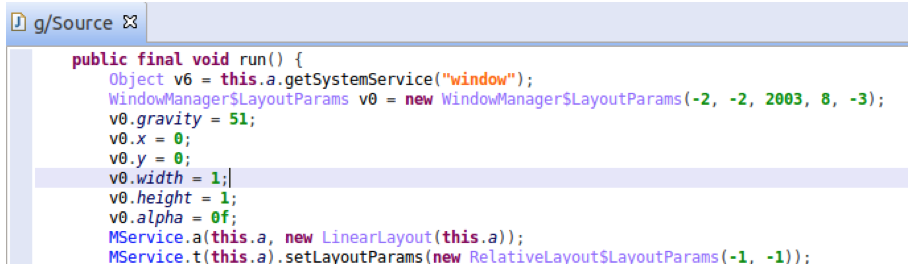
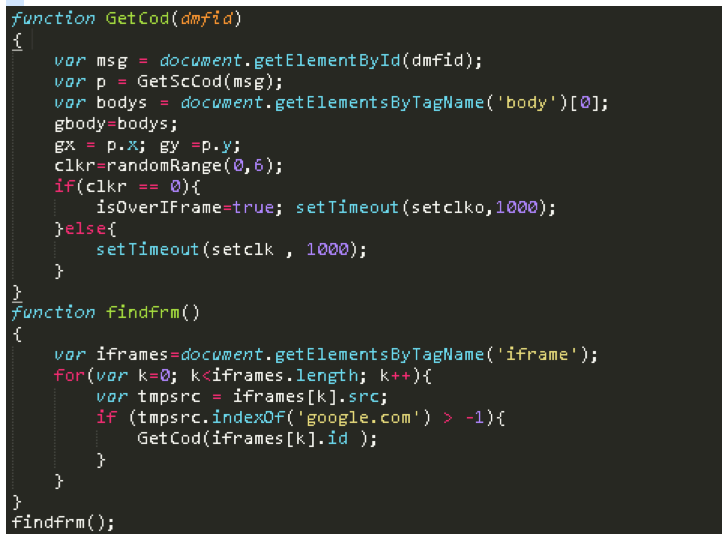
3. The apps are real games and look benign to the user. On top of the visible game view, the apps add another webview to load a URL and JavaScript. The webview is set as minimum size (shown in the code below), so it’s invisible to the user.
Sequence of events
It registers broadcast receivers for PACKAGE_ADDED, PACKAGE_REPLACED and BOOT_COMPLETED actions. When a new package is installed or updated or the system reboots, it will start a service.
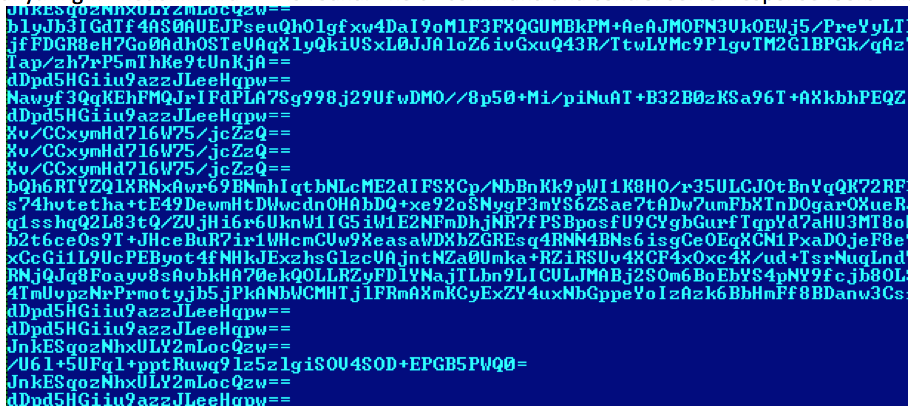
The service contacts the command-and-control server to get the URL, user agent string, rReferer, and javascript. It includes other configurations, including the time intervals to run auto-click javascript.
It also checks if there’s net.shinhwa21 activity running. It won’t do anything if net.shinhwa21 is found. The command-and-control server response looks like this:
The app then opens a URL in the invisible webview on a time interval and loads the Javascript payload to search for an iframe that contains Google ads and clicks on the links:
This PUA is pervasive
This analysis underscores the growing scourge of PUAs on all platforms – Windows, Android, Mac, etc.
The Judy apps obviously broke Google’s policies and abused Google Ads. However, the apps are not a concern for users other than the unethical use of bandwidth. As a result, Sophos categorized “Judy” apps as a PUA.
Defensive measures
As we mentioned above, SophosLabs has identified this as App/Adload-NL and has protected Sophos users against it.
Our advice is to not download these apps. We’ve told Google Play about our findings and they have already been removed, but they may well still be in other Android app marketplaces.
While we continue to work with Google Play to help keep malicious apps away from your devices, it’s a never-ending game of cat and mouse, so it’s a good idea to use our free anti-malware, Sophos Mobile Security for Android, to protect your phone.

Leave a Reply