As the world reeled from WannaCry earlier this month, many fingers were pointed at organizations still using Windows XP. As we now know, the contagion actually infected Windows 7 systems the most.
It’s still a bad idea to use XP. It’s no longer supported, has a long history of being exploited, and the latest versions of Windows are far more secure. But making XP the scapegoat distracted security pros from other aspects of the attack that needed to be understood.
SophosLabs continues to investigate why WannaCry couldn’t remotely infect XP nearly as effectively as Windows 7 – if it could at all – and whether the mechanics of the outbreak were the deliberate actions of an attacker or merely a case of buggy code run amok. What they know so far is described below.
Regardless of why Windows 7 was the easier conduit, this much is certain:
- Windows 7 computers were infected because they hadn’t been patched against the Windows SMB vulnerability that WannaCry exploited.
- Like countless attacks before it, WannaCry had no trouble spreading because so many unpatched systems had their port 445 open to the outside.
Failure to patch – again
WannaCry spread because of a vulnerability in Windows Server Message Block (SMB) service, which Windows computers use to share files and printers across local networks. It’s the same type of old-school vulnerability that allowed worms like Slammer and Conficker to spread around the globe more than a decade ago.
Microsoft had addressed the issue in its MS17-010 bulletin in March, but companies using older, no-longer-supported versions of the operating system wouldn’t have seen it unless they were signed up for custom support, ie Microsoft’s special extended – and paid-for – support.
Microsoft has begun phasing out Windows 7, though it continues to offer limited extended support options for business customers. Windows 7 Service Pack 1 will expire in two and a half years’ time, on January 14 2020. Despite that, Windows 7 remains in heavy use and, as the WannaCry outbreak demonstrated, many of those systems are not getting patched in a timely manner.
Unpatched Windows 7 + port 445 = trouble
During its investigation, SophosLabs has confirmed that systems most at risk in the attack had been running unpatched versions of SMB on Windows 7.
Take all those unpatched computers and leave them with port 445 open on a public or even private network and you’re asking for trouble. In that scenario, once a single device is compromised, the attack can spread like wildfire across your internal network.
That’s why the usual advice is to not have open 445 ports looking to the outside.
XP was a poor conduit
Though the lack of patching and exposure of port 445 were easily identified problems, the reasons why Windows 7 was an easier target than XP remain somewhat clouded.
During testing, SophosLabs found that XP wasn’t the effective conduit for infection via the EternalBlue SMB exploit that many thought it was, while Windows 7 was easily infected. The research showed that WannaCry ransomware can affect XP computers – but not via the SMB worm mechanism, which was the major propagation vector for WannaCry.
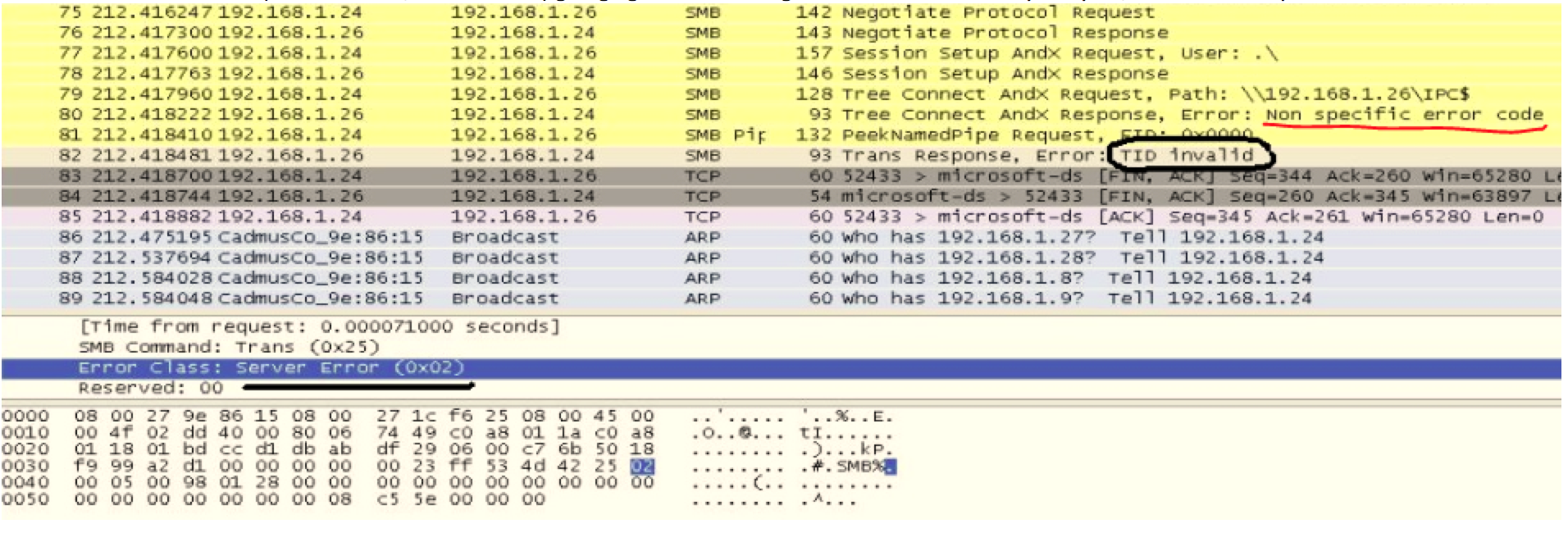
The screenshot below shows the attack (at the network level, in Wireshark) going against an XP target. You can see that very early on, the servers respond with an error and it fails to proceed any further:
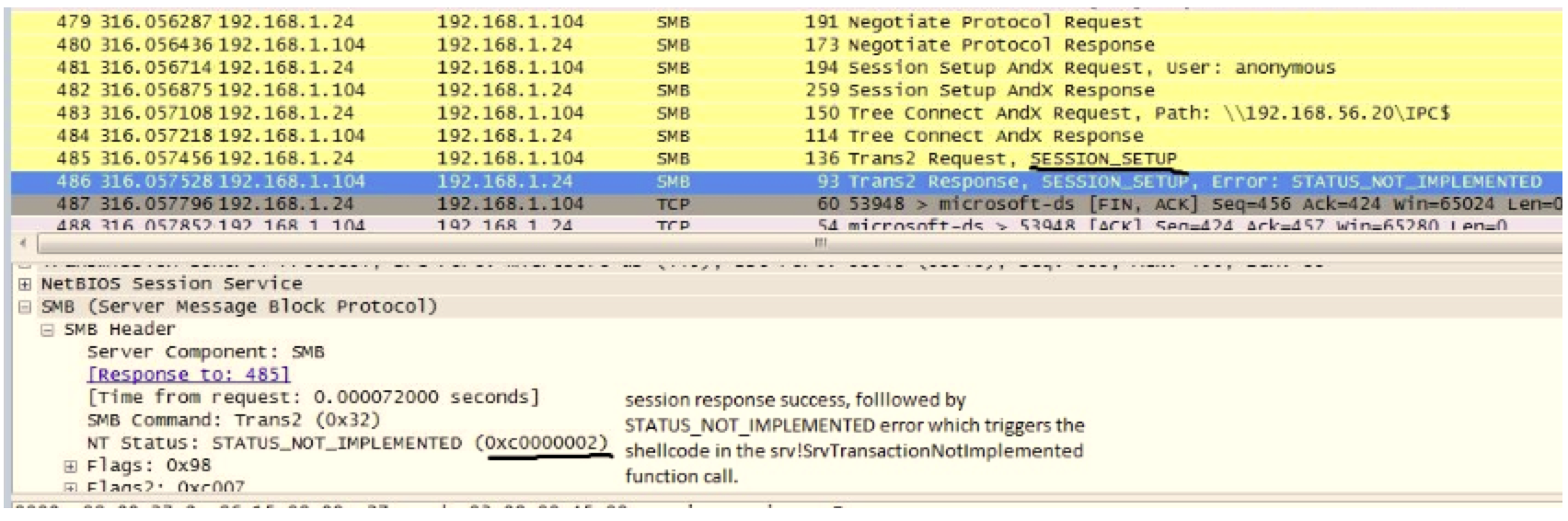
Here is the same attack on Windows 7. Note that the same error does not appear in this case:
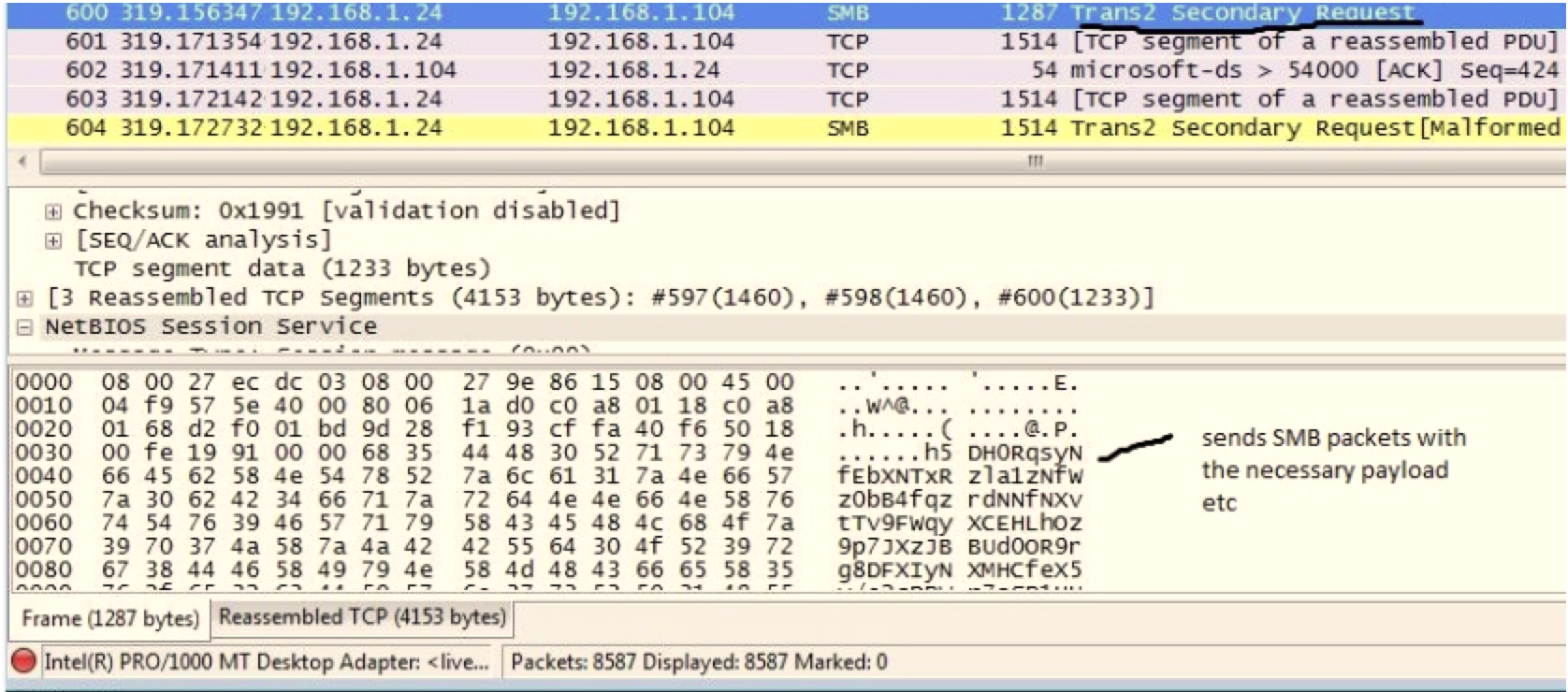
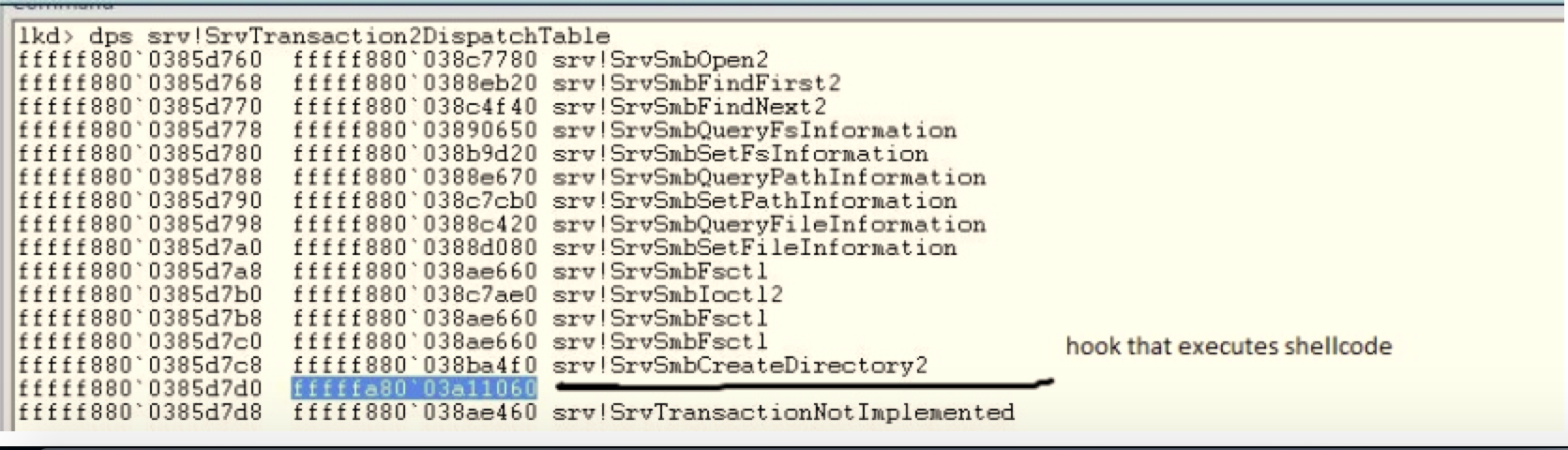
The Windows 7 infection then continues to an actual payload state:
Various security companies arrived at a similar conclusion, putting the infection rate among Windows 7 computers at between 65% and 95%. SophosLabs puts that number even higher: our analysis of endpoint data for the three days that followed the outbreak shows that Windows 7 accounted for nearly 98% of infected computers.
That percentage came as a surprise to some, since XP was almost universally cited as the exploited operating system. Microsoft even took the highly unusual step of making a security update for platforms in custom support (such as Windows XP) available to everyone.
The tiny amount of XP computers reporting WannaCry detections were likely test machines or PCs infected through a different vector.
A difference of SMB drivers?
Early in the outbreak, researchers determined that both SMBv1 and SMBv2 packets were used in the attack. Since both versions of SMB were in play, it could be theorized that Windows XP proved hard to infect because it does not include SMBv2, which was introduced in Windows Vista.
But so far, it’s hard to reach that conclusion with 100% confidence.
Lessons learned
For organizations still running Windows 7 and other versions of the OS, recent events highlight an important lesson that continues to go unheard: that organizations must keep a close watch for patch updates and deploy the fixes immediately.
Some will criticize organizations that are slow to patch or use the latest Windows versions. It can be especially easy to blame the victim. But slow patching or the use of outdated versions of Windows isn’t always the result of laziness or apathy.
It’s long been the case that IT shops hold back some patches because they need to tweak their systems for compatibility. Otherwise, they risk deploying a patch that breaks other programs. Meanwhile, some organizations have continued to use old versions of Windows because:
- They lack the financial and human resources to upgrade.
- Their legacy systems simply aren’t yet equipped to work with the likes of, say, Windows 10.
There are other reasons, but those are two big challenges.
But as Sophos CTO Joe Levy noted shortly after the outbreak, there are cases when a patch shouldn’t be viewed as optional, no matter what the company’s patching policy – like when the vulnerabilities fall into the category of common-mode failure.
Patch often and block port 445
The bottom line: if you use older versions of Windows, you’re at greater risk for attacks like these.
The best advice is still for organizations to keep their patching up to date and use current versions of Windows. Or, if you must continue using older versions for compatibility reasons, sign up for Microsoft custom support so you continue to receive security updates.
Just as importantly, for the reasons stated above, organizations need to set their firewalls to block access to port 445.

funnyThings
One thing I have not heard much about is that Microsoft changed the way it rolls out patches in the past year. (last fall i think) This doesn’t sound like a big deal but it was and to an extent still is.
I have come across admins that are scared to roll out patches and with the new monthly roll-ups they are somewhat confused. Obviously the answer is to ALWAYS install at minimum the security patches, have a full test environment, etc. That said, there are plenty of admins still scared that it will break-something…
gregory flattery
Its no surprise that the NHS was hit so hard, I was shocked to see Windows 7 running on A & E computers as recently as 2015.
What are IT support doing at these Hospitals, to be so out of date.
Paul Ducklin
Windows 7 is still supported, so it isn’t out of date. (Yet!)
Lee
Its not just the NHS that are using Win7 they are huge amount of companies that are still using Win7.and as mentioned it is still supported.
The problem is that there are so many applications that need to be run on these systems that the NHS can’t simply upgrade to Windows 10 without these applications being upgraded to support Windows 10 first. The applications are 99% 3rd party companies that are out of the hands of the NHS IT departments and they are slow to keep up with the OS systems for one reason or another.
The other problem is funding for the hardware to be upgraded to support the latest software and then the licenses for the OS and other MS products along with the thousands of licenses for the NHS systems across the country. This is obvioulsy not cheap!
So before putting the blame on to the NHS departments just think of the bigger picture…which like most things normally comes down to a cost.
jane cobb
Microsoft have effectively discouraged many people from patching W7 mchines because it is no longer possible to control which patches are installed nor to delete individual patches if those cause problems. After the W10 promotion fiasco there are a lot of us who are very wary of letting M$ foist their malware on our machines again.
TLV Press
When the CDC wants to protect the populace against the latest flu bugs, they hope to inoculate everyone, not just all those not yet 10 years old. Why should XP not be protected agaist exploits just because it’s over 10 years old? Makes no sense.
Paul Ducklin
Sorry, but the analogy with flu vaccines simply doesn’t hold. Computers aren’t people, Microsoft isn’t part of the US public service, human flu viruses don’t work like malware threats, and flu vaccines just don’t work like security software.
Max
Uhm, because typically you can’t just buy a younger person that is already immune to a lot of the viruses out there to replace the older person that might still be at risk. With people you don’t have an alternative. With software, you do. If you have a 50 year old car you can’t expect the manufacturer to update it to current safety standards. Either buy a new car that adheres to those standards, or drive the old one at your own risk.
Anonymous
Thank you.
gregory flattery
Further to my unpopular view of what NHS IT support was doing using Windows 7, could someone explain why so many NHS hospitals were hit and could not function for days, if it comes down to not patching or an open port, surely this needs investigating and a report should be published, which can be read by joe public.
We are dealing with peoples lives here, A & E is the first acute port of call and therefore should be the utmost secure from hackers.