Thanks to Chen Yu, Rowland Yu, William Lee, and Ferenc László Nagy of SophosLabs for their behind-the-scenes work on this article.
Adware is typically viewed as a nuisance that does no real harm. But in recent research, SophosLabs has seen adware in Google Play that does more than just deliver ads. This strain can collect the user’s personal information, including email address, and send them to a remote server.
Sophos detects this adware library as Android XavirAd and the information-stealing component as Andr/Infostl-BK.
XavirAd is found in more than 50 Google Play apps, some of which have more than a million downloads. For all the impacted apps combined, the download number is about 55m, said SophosLabs researcher Chen Yu. One such app is Add Text on A Photo.
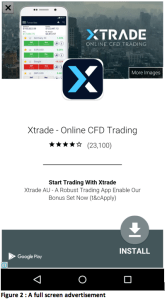
With these apps installed, users will have a full screen advertisement popping up at regular intervals even when the app is closed. For example:
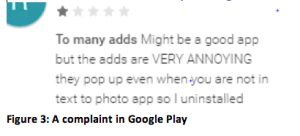
Users have quickly noticed something wrong after downloading these apps, and their discontent can be seen in the Google Play store:
But XavirAd can do more than just popping up ads. Once the app is started, the XavirAd library contacts its server and gets the configuration code:
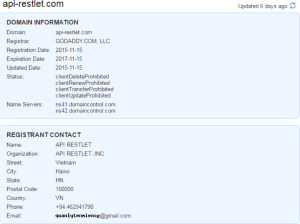
The server responds with advertisement settings including full screen ad intervals, and saves them in shared preferences. The domain api-restlet.com registered for this purpose appears to be a year and a half old, with origins in Vietnam:
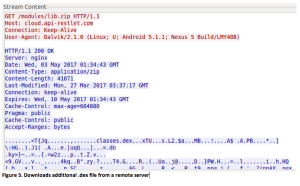
It then downloads another .dex file from cloud.api-restlet.com:
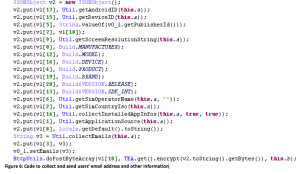
The downloaded .dex file collects the following information from the user’s phone:
- User’s email address for Google account
- List of apps installed
- IMEI identifier and android_id
- Screen resolution
- Manufacturer, model, brand, OS version
- SIM operator
- App installation source
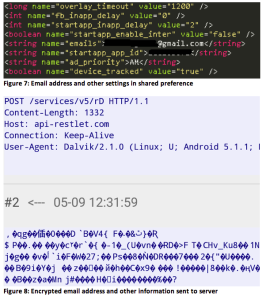
It then encrypts and sends them to a web address:
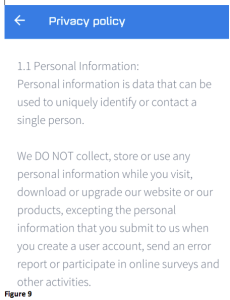
All this happens while the app itself declares in the privacy policy that it does NOT collect any personal information.
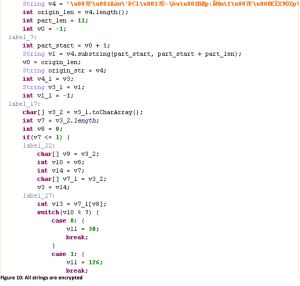
XavirAd works very hard to hide itself from security inspection, Yu said. The strings it uses are all encrypted. Each class has its own decryption routine in the class constructor. Although the algorithm remains the same, the keys are different in each class.
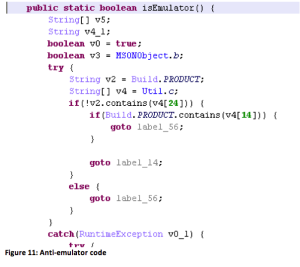
Yu said it also uses anti-sandbox technology to hide from dynamic analysis. It stops the malicious behavior it finds it’s running in a testing environment. First it checks the emulator:
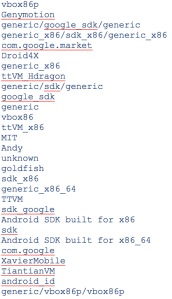
It then checks the following strings for the emulator:
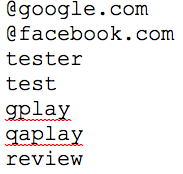
It also checks the user’s email address for another safety net that it’s not run by a tester. If the email address contains the following strings, it will stop the action:
The following Google Play apps contain XavirAd, and users may want to avoid them:



Mahhn
I’m sure that you informed google of the malware laced apps you’re exposing here, as you have done many times.
Question is; if they don’t respond (remove the apps) and peoples systems get exploited, can/should people sue them for intentionally severing malware?
What will get them to properly vet software before they share it with a bogus label of safe?
Laurence Marks
Besides removing the apps from the Play Store, Google should use Google Play Services to delete them from all users’ devices.
Lee
Hi, Google wouldn’t be able to just remove these apps from your device without your permission.
As that would mean they are tampering with your device so they would be no better than the people who have created the apps. Even if they are doing it for your own protection.
Jim
True, but they could send a serious warning message, asking for it to be removed. Better yet, they could simply block the addresses in the OS, so the malware can’t phone home.
qqq
Except they have done that before. Removing apps without permission that is.
nope
They’ve done it MANY times in the past! Read the TOS.
Mahhn
Since that might not be possible, they should “at the least” notify people that downloaded malicious apps. As a log in is required to download anything from GP, they know who downloaded what.
Ed
I like the new focus on calling out apps. Keep it up!
DT
Peel remote (preinstalled on the galaxy s5) started showing full screen ads identical to this even without the app open. Even running a full Sophos scan doesn’t show any issue though. MX player i have also seen do the same thing with the exact ad as shown in your screenshots above…
Full screen and intrusive advertisements are the biggest reason for using an ad blocker – now it seems even that isn’t enough with apps building them in and then siphoning data!
Ivy Iverson
They should advise users if an app they have is bogus, (collects info when they say they don’t or other “info leaks”), so that the users know their info is being stolen, and can either accept the crap that results or delete the app. Unfortunately, that’s locking the barn door after the horse is stolen , but at least we would know.
mattdphotographer
Remember if something is Free then “you” are the product :D