Since Chrome is standard on Android phones, you wouldn’t expect a cracked version of the app floating around outside Google Play to be much of a problem. But in one case SophosLabs investigated recently, the techniques used to pollute the app out in the wild are finding their way into other apps that are in Google Play.
SophosLabs Android researcher Rowland Yu said one such piece of malware found in compromised Chrome versions is Andr/SandRat-C, and it’s built to evade the digital signatures at the heart of modern security procedures.
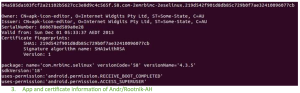
And while the hacked version of Chrome isn’t in Google Play, another piece of malware with the same functionality is – Andr/Rootnik-AH. Yu explained the broader threat to Android users:
The main point is that Google Play allows a compromised certificate [through the associated malware], though they know the certificate has been used to sign rootkit malware.
Compromised Chrome downloads
After further checking, Yu said the lab found more than 1,000 malicious apps distributed outside Google Play. One of them is a hacked Chrome Browser, Yu said.
Labs has seen Andr/SandRat-C-laced versions of Chrome before, with its first detection in 2015. The malicious payload in that case had the same functionalities labs is seeing now – recording audio or other media, reading SMS contents, sending SMS, and querying the phone location. Yu said:
When the first hacked version of Chrome was discovered in 2015, a few people were still downloading apps outside Google Play.
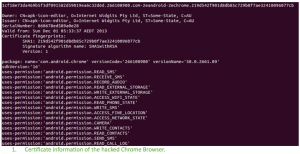
The picture below shows the certificate information in the hacked version of Chrome:
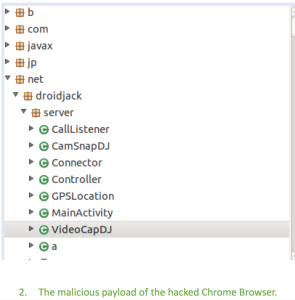
In this case, the same icon and functions are presented as they would appear in a legitimate Chrome browser. Here is the malicious payload of the hacked Chrome Browser:
Moreover, the same digital certificate is used to sign another rootkit with functionality to bypass Android SELinux security (detected as Andr/Rootnik-AH). The rootkit used to be found in Google Play but was removed recently. It means that the certificate in both Andr/Rootnik-AH and Andr/SandRat-C is very likely compromised, Yu said.
Digital signatures are a major part of modern computer security — used to verify the authenticity of digital messages or documents. Yu explains:
In Android, all APKs are required to be digitally signed with a certificate before they can be published and installed. A digital signature consists of a public/private key pair. An APK signed with a developer’s private key can be verified by anyone who can access the public key inside the APK. The developer has the responsibility of maintaining the security of the private key.
SophosLabs realized something was amiss because it couldn’t find any legitimate websites related to the company or developer who created the digital certificate: CN=apk-icon-editor and O=Internet Widgits Pty Ltd, ST=Some-State, C=AU.
Google Play still polluted
Though the hacked Chrome browser was found outside of Google Play, the SophosLabs database shows more than 700 apps signed with the same questionable certificate in Google Play. Of them, Google Play has removed 292. That leaves more than 400 shady apps in Google Play, including this and this. Most of them are junk apps and may not contain malicious behaviors.
Sophos users protected
Since strong evidence shows that the certificate has been comprised, SophosLabs decided to block all of them as potentially unwanted applications — PUA/Android Abused Certificate — to protect its customers. Yu said:
This is because we treat the private key as something of critical importance, both to developers and to users.

Renard Moreau
[ Smiles ] My goodness, I didn’t expect Google Play to be such a mess, because I thought the folks over at Google would have been monitoring those application.
Thank you for the head’s up!