SophosLabs has discovered a new spam campaign where ransomware is downloaded and run by a macro hidden inside a Word document that is in turn nested within a PDF, like a Russian matryoshka doll. The ransomware in this case appears to be a variant of Locky.
Most antivirus filters know how to recognize suspicious macros in documents, but hiding those document inside a PDF could be a successful way to sidestep it, according to SophosLabs researchers.
What the latest tactic looks like
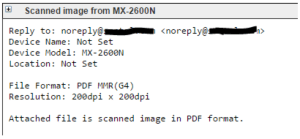
Following the typical pattern, this latest ransomware push comes as emailed spam with a PDF attachment:
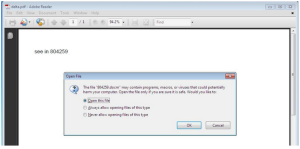
The PDF has an attached document inside, which is trying to get opened by the Acrobat Reader:
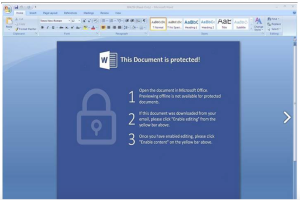
Once the doc is opened in MS Word, it asks you to enable editing through a social engineering attack:
This runs a VBA macro, which downloads and runs the crypto ransomware.
What to do?
There are things people can do to better protect themselves from this sort of thing:
- Back up regularly and keep a recent backup copy off-site. There are dozens of ways other than ransomware that files can suddenly vanish, such as fire, flood, theft, a dropped laptop or even an accidental delete. Encrypt your backup and you won’t have to worry about the backup device falling into the wrong hands.
- Don’t enable macros in document attachments received via email. Microsoft deliberately turned off auto-execution of macros by default many years ago as a security measure. A lot of malware infections rely on persuading you to turn macros back on, so don’t do it!
- Be cautious about unsolicited attachments. The crooks are relying on the dilemma that you shouldn’t open a document until you are sure it’s one you want, but you can’t tell if it’s one you want until you open it. If in doubt, leave it out.
- Patch early, patch often. Malware that doesn’t come in via document macros often relies on security bugs in popular applications, including Office, your browser, Flash and more. The sooner you patch, the fewer open holes remain for the crooks to exploit. In the case of this attack, users want to be sure they are using the most updated versions of PDF and Word.
- Use Sophos Intercept X, which stops ransomware in its tracks by blocking the unauthorized encryption of files.
Sophos detected the PDF as Troj/PDFDoc-C and the payload as Troj/Locky-UP.
Other links we think you’ll find useful:
- To defend against ransomware in general, see our article How to stay protected against ransomware.
- To protect against JavaScript attachments, tell Explorer to open .JS files with Notepad.
- To protect against misleading filenames, tell Explorer to show file extensions.
- To learn more about ransomware, listen to our Techknow podcast.
- To protect your friends and family against ransomware, try our free Sophos Home for Windows and Mac.
Techknow podcast — Dealing with Ransomware:


David Wilkerson
There is no helping someone that falls victim to this scheme. They had 4 chances to say NO and they did it anyway.
1. Don’t read unsolicited emails.
2. Don’t open attachments from unsolicited emails.
3. Don’t open .docm files from unknown origins.
4. Don’t enable macros.
FreedomISaMYTH
there are still users that will fall for it…
woody188
Blaming the victim doesn’t help anyone either. We’re lucky there are people that open these or else it would get really difficult to tell the difference and we’d all be at risk. It’s herd protection.
matthew.hall@metconsultancygroup.com
Is this an issue with all PDF readers or just Adobe???
Paul Ducklin
Depends on the PDF reader. (Sorry, that doesn’t help enormously :-)
This isn’t a bug or misfeature of Adobe or any other reader: PDFs can contain embedded files, just like ZIP files (or, for that matter, DOC files), and by one means or another you can extract the embedded file and open it in its turn.
(You could have, say, an EXE wrapped in a macro stored in a DOC embedded in a PDF in a PDF packaged into a TAR file that’s been GZIPped and then converted into a base64 email attachment that’s been archived into a ZIP file.)
A good anti-virus gateway product will recursively extract files of this sort, or sometimes even condemn then outright for being dubiously complex – what’s often called a “zip bomb”. And a good real-time anti-virus will check each embedded item if ever it is extracted from its cocoon, before it’s allowed to be used by the next application in the chain.
I guess what I’m trying to say is that, even if in this case a non-Adobe PDF reader might not be able to extract the embedded document, that’s won’t generically solve the problem of files embedded in PDFs, becaue that’s a feature of the PDF file format. In just the same way, in our contrived example above, using an unarchiving tool that understands ZIP and GZIP but not TAR or base64 would protect you – but more by accident than by design.
Of course, the good news is that the deeper the crooks try to bury their dodginess, the more steps they have to talk you through to reach the buried badness, and the more opportunities both you and your security software have to go, “This won’t do.”
Mark Davis
A theoretical product with a more permanent solution for threats.
A more permanent solution which adapts quickly is for someone to invent a “virtual computer” like I have with “virtual box” with two additions. One is a “read file” where you can input something – say a document. The other is a write file where you can output a file – eg the same (or modified) document. Input to the virtual computer and output from the virtual computer can thus be “isolated” from the rest of the computer.
The virtual machine is to be totally and completely isolated from the rest of the computer except for these two points of access.
If PDF and word documents (and in the future, other programs) have a vulnerability, then set your word or pdf program to operate in the virtual environment. 99% of the development is already existing. If there is an infection – only the virtual machine is effected, not the entire machine.
It will stop most of the current threats entirely – even for those who do not do security very well.
Yes – there is development work required. But is seems to me to the best of all worlds.
You would have a very VERY large market for said to be developed product!