If an email hits your inbox asking for payment in return for a TV license, be careful: a new social engineering attack is circulating that uses spam messages to trick victims into downloading file-deleting malware.
SophosLabs has seen such cases escalate since early January, when attacks struck two organizations, deleted files on shares and replaced them with .JSE files that took the same names as the original files.
The attack begins when the bad guys send emails to people within the targeted organizations. Technically, it’s not a phishing email, which takes the victim to a fake log-in screen. With this particular tactic, the click simply results in the download of a malicious document.
Those who click are infected with the .JSE worm, which then goes to work deleting and replacing files on your network shares. The worm is roughly the same each time, but the payload has changed in each of the attacks SophosLabs analyzed.
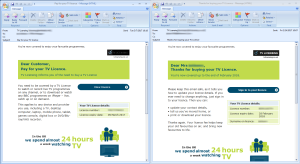
On the left, a social engineering trick
Victims were infected using typical spam emails. Below are two messages about the status of a TV license. Choosing that topic was clever on the part of the bad guys, especially for targeting people in the UK, where such licenses are mandatory. The copy is fairly authentic-looking, until you look more closely.
The one on the left is the spam message, which tells the reader that payment is still needed. There is also no customer name or license number, and the logo is slightly off:
If “view invoice” is clicked, it downloads a file called Invoice.doc, which is infected with Troj/DocDl-IGU. Once the file is downloaded and opened, the user has to enable macros. Before macros are enabled, the file looks like this:
Once macros are enabled, the malware begins its attack.
The worm connects to a command-and-control and pulls down a payload. The payload changes with each attack. In one case it was the banking trojan Dridex (v4). In another case it was a different banking trojan known as Gozi.
Defensive measures
Sophos is blocking the malware on behalf of its customers, but it’s important for organizations to warn employees that these emails are making the rounds. Specifically, companies should:
- Explain what the emails look like and how to tell the real from the fake
- Warn employees not to click anything unless it comes from a trusted source
For this type of infection (doc/script/download) there are other techniques people can use to protect themselves. For example:
- Deploy anti-spam software to stop malicious email from getting to the user
- Employ email gateway attachment policies. For example, blocking inbound Office documents with macro content
- Have an Office group policy that block untrusted macros
- Use application controls to prevent unauthorized use of script engines (wscript in this case)
- Back up files frequently


Leave a Reply