Today’s huge security SNAFU was the widepsread appareance of swastikas and Nazi taunts all across the Twittersphere.
What made this eruption of online hatred particularly unusual was the nature of some of the accounts that had apparently waded in, openly hashtagging both the Germans and the Dutch with the epithet “Nazi”, and referring to an upcoming constitutional referendum in Turkey.
Amnesty International was one organisation that hit the headlines, as this screenshot from Twitter (now removed as a tweet) shows:
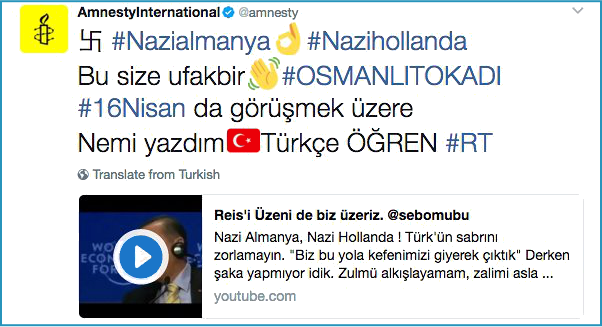
The unauthorised tweets not only included offending icons and hashtags in their body text, but also linked to a YouTube video talking up Recep Erdoğan, the current President of Turkey.
As well as tweeting from affected accounts, the cybercrooks behind this attack also changed the profile pictures on many accounts to an image of the Turkish flag.
Starbucks Argentina is probably the most widely reported of those accounts because it continued to display the Turkish flag long after many other companies had repaired the damage, perhaps because of the timezone difference.
We’re happy to report that @StarbucksAr is back to normal now:

What happened?
As far as we know so far, this wasn’t a breach at Twitter itself.
It seems to have been an as-yet-undisclosed security blunder at a third-party company called Twitter Counter, which offers Twitter services that help you collect analytical statistics, deliver adverts, and more.
Legitimate third-party Twitter apps don’t actually store, or even know, your password, so they can’t take over your account entirely (and dodgy ones can’t try out your password on other sites, either).
But when you activate Twitter services such as Hootsuite, Twitpic, Twitter Counter and many others, you nevertheless authorise them, via a security token issued by Twitter, to perform certain actions on your account.
(Note that when we say “apps” in this context, we aren’t referring only to mobile software packages like Twitter’s own apps for Android, Windows Phone and iOS, but also to online services that you can configure to run your account semi-automatically in your absence.)
If any of those third-party services get hacked, or turn out to have an exploitable vulnerability that lets crooks issue commands to other people’s accounts remotely, then the sanity and sanctity of your own Twitter feed is at risk.
And that’s part of the problem here.
Services that you have authorised to access your account at any time in the past can continue to do so, even after you log off from Twitter in your own browser, or after you logout via the Twitter software on your mobile phone.
What to do right now?
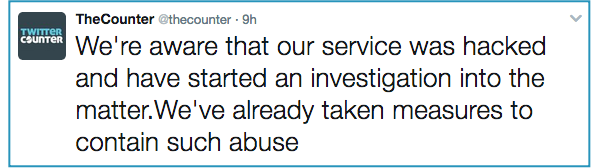
According to reports from Twitter and Twitter Counter, Twitter Counter’s access to existing customer accounts was revoked, thus automatically preventing any further abuse .
At the time of writing [2017-03-15T15:15Z], Twitter Counter’s service appears to be “temporarily down for maintenance”:
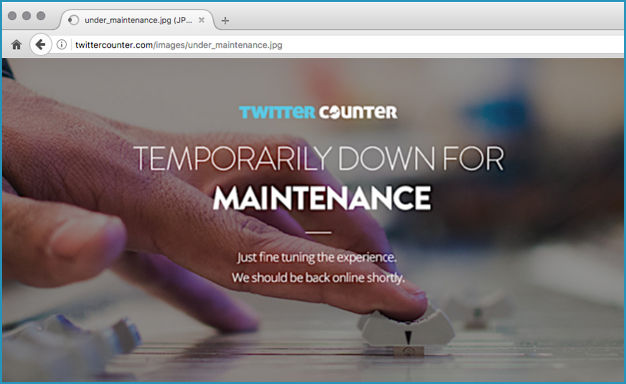
The company rather sweetly says that it will be back online shortly, and is “just fine tuning the experience”.
You’ll have to decide for yourelf whether that makes you feel better or worse about its attitude to security.
Twitter has reportedly deleted all the illegally-sent “swastika” tweets, too, but if you are a Twitter Counter user we recommend you review the appearance of your account anyway if you haven’t already.
Look out for tweets that shouldn’t be there, and make sure your profile wasn’t fiddled with along the way, as happened to Starbucks Argentina.
What to do next?
It’s vital to learn how to review the Twitter apps that have access to your account.
Admittedly, if you were an active Twitter Counter customer when this “swastika outbreak” happened, you would have been at risk anyway, because you would have expected the company to have access to your account.
But we’re prepared to wager that many Twitter users have more apps on their access list than they realise, including apps that they don’t even remember, and the purpose of which they have now forgotten.
In other words, we suspect that at least some of the victims in this “swastika” case were surprised to find that the Twitter Counter service still had access to their account, because as far as they were concerned, they were no longer using it.
Here’s how to check which third parties can get at your Twitter:
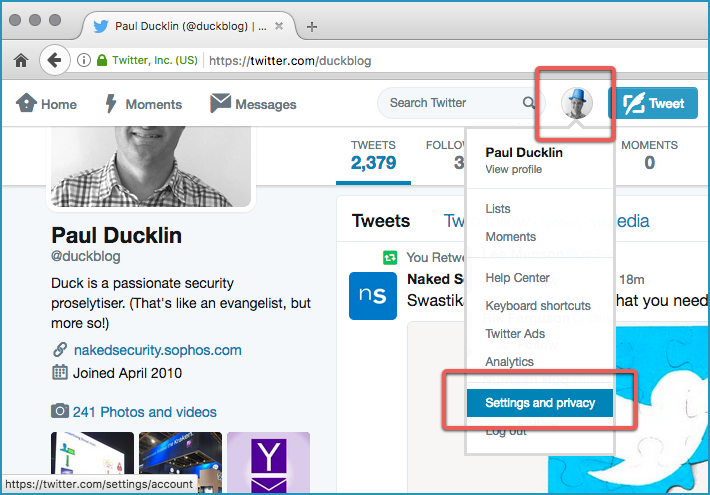
1. Login to Twitter from your browser. (As far as we can tell, the feature you need isn’t available from Twitter mobile applications, though it is available, if a little fiddly, via your mobile phone’s browser.)
2. Go to Profile and Settings. You can use the link https://twitter.com/settings/account, or click on your avatar at the top right and choose Settings and privacy from the pulldown menu.
3. Click on Apps > in the menu at the left hand side.
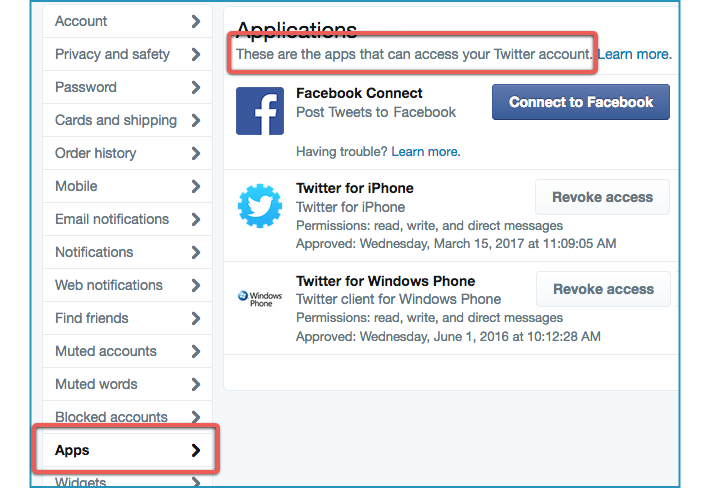
You will see a list entitled “These are the apps that can access your Twitter account”.
For any apps and services you no longer use, no longer trust, or simply can’t remember, use [Revoke access] to do just that. (You can always restore their access later if necessary.)
When it comes to handing over acccount access to other people, follow our adage: “If in doubt, don’t give it out.”
Note that even Twitter’s own mobile apps can have their access revoked from this page.
This is very handy if you are in the habit of leaving your mobile phone logged into Twitter via the app, and then you lose your phone.
Even if the app is currently running on your phone, and someone else is using it, revoking the app’s access stops the person who has your phone from doing anything new to your account – it essentially causes a forced logout.
Try for yourself! Open up your mobile Twitter app, login if you haven’t already, and find a tweet you are happy to retweet. Now revoke access to your mobile phone via Twitter’s website, and hit the Retweet icon on your mobile. The app will figure out it’s no longer allowed to do that, and will immediately prompt for your password. When you have logged back in via the mobile app, it will reappear as authorised on the Settings | Applications page.
Featured image: AlesiaKan / Shutterstock.com

Vog Bedrog
Love the idea of somehow fine-tuning a website using a mixing desk – “Can we turn up the GUI a bit, and maybe filter out some of the basest comments?”