The Luxembourg government’s web servers have been slowed to a crawl since the start of a DDoS attack Monday, according to state-owned IT provider Centre des Techniques de l’information de l’Etat (CTIE).
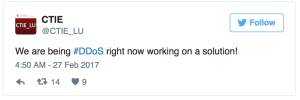
CTIE confirmed the attack in a Tweet Monday morning:
The attack started around 9:30 am Monday and knocked down some 100 web servers used by state authorities and offices. CTIE director Gilles Feith told the Luxemburger Wort that the attack was ongoing and that “we are working with all the relevant services to repel it”.
He said it could be hours or days before everything returns to normal.
Who launched the attack and why is still unknown, Feith said.
In a denial-of-service attack, an attacker attempts to overload or shut down a service so that legitimate users can no longer access it. Typical DoS attacks target web servers and aim to make websites unavailable. No data is stolen or compromised, but the interruption to the service can be costly for an organization.
The most common type of DoS attack involves sending more traffic to a computer than it can handle. There are a variety of methods for DoS attacks, but the simplest and most common is to have a botnet flood a web server with requests. This is called a distributed denial-of-service attack (DDoS).
Government systems are a popular target. Typically, such attacks are done to protest the actions of a particular nation. Security experts have long warned of such attacks being made into a tool of war — used to disrupt the military networks of an adversary.