Thanks to Brett Cove of SophosLabs for his behind-the-scenes work on this article.
You might not have noticed, but the amount of spam being sent globally has fallen off dramatically recently.
We aren’t talking about phishing emails, cheap viagra pills and endless surveys where you can win an iPhone that doesn’t exist – those are still spamming inboxes the world over.
We’re talking about the sort of malicious spam that plagues you with information about missed parcel deliveries, fake CVs (resumes) and invoices for services you didn’t use in the hope of tricking you into opening malicious attachments to spread ransomware like Locky or banking Trojans like Dridex.
These attachments come in a variety of forms, such as Microsft Word or Excel documents laced with malicious macros, or more recently JavaScript (.JS) and Windows Script Files (.WSF). The attachments usually follow a similar formula: if you run them, they call home to a server controlled by the crooks and download a malware sample to infect you with, or these days even multiple malware samples.
Something strange has happened in the world of spam, though.
Since just before Christmas 2016, spam levels have dropped by more than half. We have seen outages like this before, but this one has lasted two months now with no sign of spam levels increasing again, although we assume they will at some point.
The chart below represents the spam levels seen in the Sophos spamtrap network, plotted daily, going back to the end of November 2016:
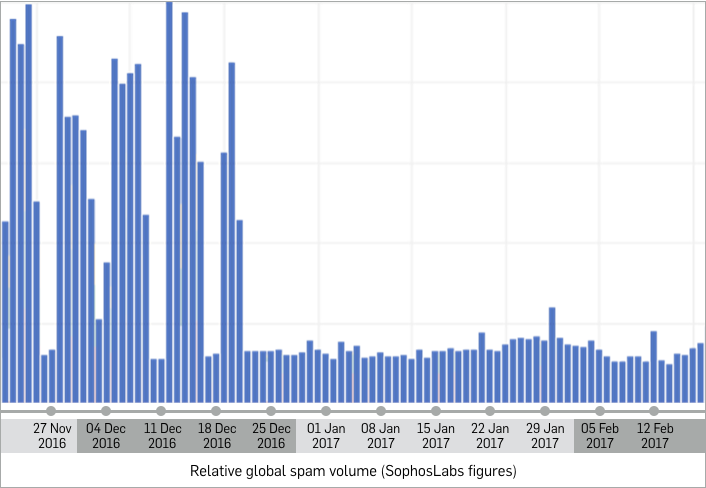
As you can see, the spiky shape of the graph ended just before Christmas 2016 and has not been seen again. (It is also interesting to note that spam levels routinely increased during the working week, from which we assume that even cybercriminals don’t like to work at weekends.)
To rule out the possibility of this being caused by an issue with our own infrastructure, we also looked at publicly available data from CBL, the Composite Blocking List, used by Spamhaus, giving us a graph with a similar shape:
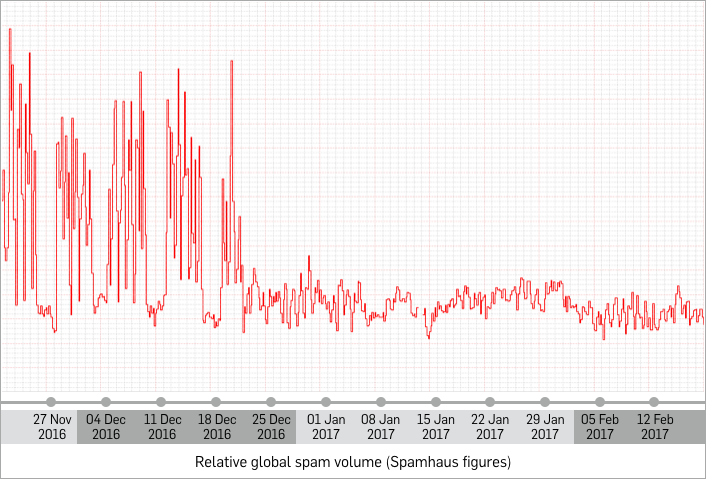
The reason for this has not been conclusively proven, but the evidence points to a notorious botnet called Necurs going quiet.
Necurs is considered by some as the largest botnet ever, with some estimates indicating it consists of more than 6,000,000 infected computers. The majority of infected computers seem to be in India, but almost every country in the world seems to be affected by this malware, with the notable exception of Russia – the Necurs malware deliberately avoids infecting computers set up to use a Russian keyboard.
Interestingly, spam levels also dropped back in June 2016, but, Necurs was back to full strength less than a month later, delivering a new version of Locky.
Why Necurs has gone quiet this time, and how long the “outage” will last, is unknown, as of course is when or if it will return to its former volume.
What we do know is that this hasn’t stopped users being targeted by Locky ransomware or other malware delivered via dodgy attachments or booby-trapped web links, despite the dramatic drop in spam volume depicted above.
We also know that the Necurs botnet isn’t completely dead, just very much quieter than it was. In other words, if your computer is part of the Necurs botnet, it’s still infected, it’s still awaiting instructions, and it could receive a command to wake up and start sending spam again in the future.
What to do?
For starters, make sure your computer isn’t helping the crooks:
- Keep your anti-virus up-to-date.
- Install the latest security patches promptly.
- Be cautious about the attachments you open, the programs you install and the web links you trust.
Additionally, if you are a sysdamin looking after your organisation’s email security, be sure to turn on outbound spam scanning. (You’ll be surprised how many companies don’t bother checking outgoing email, treating spam as a purely inbound problem – even though all inbound spam rather obviously started life as outbound spam.)
If you have zombie computers on your network that are sending out spam, you want to know about it!
After all, some of that spam might be targeting your own business, thus creating a vicious circle of infection.
To see the Locky ransomware in action, and how Sophos blocks it, why not watch our video?

ejhonda
Good to hear, but I looked at our inbound email volume and didn’t see any evidence of a drop off – around this time frame or any other.
Laurence Marks
When I started reading this article I was wondering if Sanford Wallace had a few hospital stays and then died.
Neo
Yes, true.
We also noticed dramatic decrease on rejected e-mails.
We used to reject every week around 10, 000 e-mails and since end of December this number dropped to 5,000.
But what I have noticed increased whaling attacks.
Botkiller
I can speak definitively on this: Yes, it’s Necurs (primarily ransomware payloads) going silent on Dec 22 or thereabouts. Necur’s habit was to spam on weekdays, and would occasionally go silent for a week or two. It previously went down for 6 weeks, there are various speculations as to why it did, but none proven. This time it’s greater than 9 weeks. Again, various speculations, but no proof. it’ll probably come back, but for now be glad it’s gone.