This is the third in a four-part series about SophosLabs’ 2017 malware forecast, released this week at RSA Conference in San Francisco. Part 1 looked at malware targeting Linux and Internet-of-things (IoT) devices. Part 2 examined malware targeting Android. Today’s installment is about malware designed for macOS. Special thanks to SophosLabs researcher Xinran Wu for contributing the research for this part.
Though Mac malware is comparatively rare, Apple computers are not immune, as this year’s SophosLabs malware forecast shows. Mac malware is often technically sneaky and geared towards harvesting data or providing covert remote access to thieves.
What follows are two examples: OSX/KeRanger-A, and OSX/PWSSync-B.
OSX/KeRanger-A
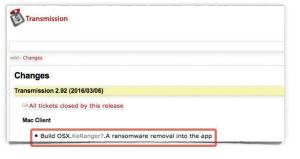
The first official Transmission app (version 2.90) infected with OSX/KeRanger-A was discovered in early March 2016. A couple days later the infected version was removed and placed in a hard-coded KeRanger check that was part of version 2.92.
Attackers essentially copied the ransomware formula that had served them so well on Windows. They set out to:
- Trick users into opening a file they were inclined to trust;
- Install and run the ransomware program;
- Call home to one of a list of control servers for an encryption key;
- Scramble files in the user’s home directory and on currently mounted volumes, adding the extension .encrypted each time; and
- Put a file called README_FOR_DECRYPT.txt in every directory where a file was encrypted.
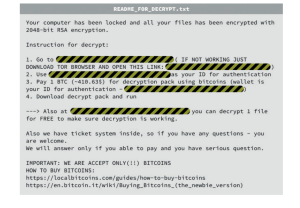
Victims get the following message:
 To prevent getting infected, Sophos at the time recommended the following actions:
To prevent getting infected, Sophos at the time recommended the following actions:
- Consider running a Mac anti-virus that can automatically scan the files you download before you run them for the first time, and that can check out the websites you try to access before your browser gets to them.
- Make regular backups and keep a recent backup copy offline, and preferably also offsite. OS X’s Time Machine backup software can create encrypted backups, so even if the disk they’re stored on is stolen, your backup is safe from prying eyes. That means you can safely exchange backup disks with a friend or family member on a regular basis, so that you each provide the other’s offsite storage.
OSX/PWSSync-B
Another example of trouble for Mac users came in August, when a bogus version of Transmission 2.92 was uploaded that contained malware known as OSX/PWSSync-B. Ironically, the main feature added when 2.92 was released was a malware removal utility for MacOS ransomware OSX/KeRanger-A.
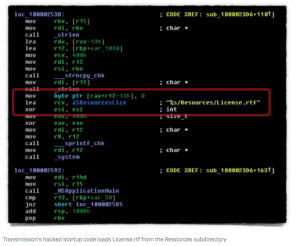
A similar hack applied to the Transmission app occurred that same month. The hacked Transmission program itself contained only a tiny change: a small snippet of code added at the start that loads a file called License.rtf that is packaged into the application bundle. (Last time, the sneaky extra file was General.rtf.)
The file License.rtf sounds innocent enough – what software doesn’t include a licensing document somewhere? – and opening it seems equally reasonable.
Except that this license isn’t what it seems.
It was actually an MacOS executable (program file) that:
- Configures itself as an OS X LaunchAgent so that it runs automatically every time you reboot or log on;
- Steals passwords and other credentials from your OS X Keychain, the Mac’s built-in password manager; and
- Calls home to download additional scripts to run.
Those affected:
- Have a Mac running OS X.
- Downloaded the Transmission 2.92 BitTorrent client on August 28 or 29 2016.
- Actually ran the booby-trapped Transmission app you downloaded.
The bad guys gained enough traction with these attacks for SophosLabs to expect more in 2017.
Coming tomorrow: Microsoft Word Intruders stepping outside Office

Leave a Reply