This is the second in a four-part series about SophosLabs’ 2017 malware forecast, released this week at RSA Conference in San Francisco. Part 1 looked at malware targeting Linux and Internet-of-things (IoT) devices. Today’s installment is about malware designed for Android devices. Special thanks to SophosLabs researcher Rowland Yu for contributing the research for this part.
When security experts recently raised concern about President Trump using an outdated Samsung Galaxy phone for his tweeting, there was a good reason.
Samsung Galaxy devices have traditionally used the Android operating system, and attackers are constantly targeting Android with malware, including ransomware.
SophosLabs examined a lot of Android malware in the last year, and the details are outlined in the 2017 malware forecast released Monday.
SophosLabs analysis systems processed more than 8.5m suspicious Android applications in 2016. More than half of them were either malware or potentially unwanted applications (PUA), including poorly behaved adware.
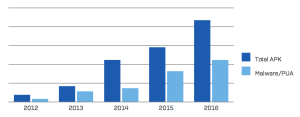
The highest malware count of the last five years
The APK packages analyzed in 2016 were the most of the last five years, as was the amount of malicious content discovered. The count has increased each year since 2012:
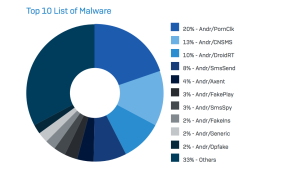
When the lab reviewed the top 10 malware families targeting Android, Andr/PornClk is the biggest, accounting for more than 20% of the cases reviewed in 2016. Andr/CNSMS, an SMS sender with Chinese origins, was the second largest (13% of cases), followed by Andr/ DroidRT, an Android rootkit (10%), and Andr/SmsSend (8%). The top 10 are broken down in this pie chart:
From the end of 2015 to March 2016, SophosLabs saw a sharp increase in PornClk malware. There was a quick drop for a time, but activity picked back up and steadily rose in the last eight months of the year.
PornClk makes money through advertisements and membership registrations. It takes advantage of root privilege and requesting administrative access on the device. It then:
- Downloads additional APKs
- Creates shortcuts on home screens
- Collects sensitive information such as device IDs, phone numbers and models, Android versions and Geo IPs.
Snapshot: Andr/Ransom-I
One ransomware specimen SophosLabs examined was Andr/Ransom-I. Concentrations of infection were greatest in Europe and North America. One percent of the cases we reviewed and protected customers against were of this malware family.
To trick users, Andr/Ransom-I pretends to be an update for the operating system and such applications as Adobe Flash and Adult Player.
Ransomware is an old topic in information security circles. Attackers have been hijacking computers and holding files hostage for years now, typically demanding that ransom be paid in bitcoins. SophosLabs did not see a surge in ransomware in 2016, but cases of it remained steady. We continue to see a lack of public awareness on the subject, and reports of cases where the victim is paying the ransom are increasing.
Just last month, for example, Los Angeles Valley College (LAVC) paid a public record of $28,000 (£22,500) in Bitcoins to extortionists after ransomware encrypted hundreds of thousands of files held on its servers.
Therefore, any ransomware that lands in the lab will be subjected to scrutiny.
Coming tomorrow: Attackers target MacOS with ransomware

amariesilver
Wow! So now, you’re at risk for malware if you don’t update software and also at risk if you update software that’s malware disguised as a legitimate software?