The big security issue of the week is a remote code execution hole related to the Cisco WebEx service.
WebEx is a popular collaboration tool for online events such as meetings, webinars and videoconferences.
Like many services of this sort, you access online events via your browser, augmented by a special-purpose browser extension.
Browser extensions and plugins allow web developers to extend the software features inside your browser with a mixture of scripts and program code, for example to add configuration options or to support new audio and video formats.
Of course, when you add another layer of programmatic complexity on top of an already-complex browser, it’s easy to add new security holes, too.
Perhaps the best known example of a problematic plugin is Adobe Flash, which has provided cybercrooks with such a fruitful source of exploitable security holes over the years that we have long been urging you to try to live without Flash altogether.
The latest security scare of this sort has been dubbed CVE-2017-3823, and it applies to Cisco’s special-purpose WebEx browser extension.
In oher words, if your organisation uses WebEx, you probably have the browser extension installed, and if you have it installed, you may be at risk.
According to Tavis Ormandy at Google’s Project Zero, who discovered and documented the bug, there are more than 20 million WebEx users worldwide.
So here is our quick checklist to help you decide what to do.
Q. What is the WebEx extension CVE-2017-3823 bug?
A. Opening a web link that contains a special “magic string” (cwcsf-nativemsg-iframe-43c85c0d-d633-af5e-c056-32dc7efc570b.html) automatically activates the WebEx extension inside your browser.
As part of this activation process, the web link can feed executable code to the WebEx extension (essentially, it can tell WebEx to run an arbitrary Windows program), which will run it automatically without any sort of “Are you sure” or “OK/Cancel” dialog.
That’s what is known as Remote Code Execution (RCE) or a drive-by install, one of the most serious sorts of vulnerability, commonly used by cybercriminals to break into your computer and plant malware on your network.
Q. Can I simply look out for the giveaway text of the magic string in my browser?
A. Not really.
If the booby-trapped WebEx URL were a regular clickable link, you would be able to hover over it before clicking on it and thus you could probably spot the subterfuge.
But a savvy attacker would embedded the link in an invisble IFRAME, or activate it by a web script, in such a way that the RCE would be kicked off automatically and invisibly.
Q. Is this bug being actively exploited in the wild?
A. Not that we know of. [2017-01-25:23:59Z]
Q. Which browsers are affected?
A. According to Cisco, Internet Explorer, Chrome and Firefox on Windows are affected.
Microsoft Edge on Windows and all browsers on Mac and Linux are safe.
Q. Is there a patch from Cisco?
A. The most recent update for Chrome is Cisco WebEx extension 1.0.7.
Cisco published a notification about this update at 2017-01-26T19:45Z, having issued and then withdrawn 1.0.3 and then 1.0.5 earlier this week after deeming them “incomplete.”
However, at 2017-01-26T19:45Z, Cisco’s official Security Advisory page says:
Cisco is currently developing updates that address this vulnerability for Firefox and Internet Explorer. There are no workarounds that address this vulnerability.
Q. What can I do while I wait for a fix?
A. Using Microsoft Edge on Windows or any browser on Mac or Linux will shield you from this bug because it doesn’t apply on those platforms.
You can also turn off WebEx support in your browser temporarily, thus preventing the Cisco extension or add-on from activating unexpectedly.
In Internet Explorer 11, click on the Tools cog in the top right corner and choose the Manage add-ons option:
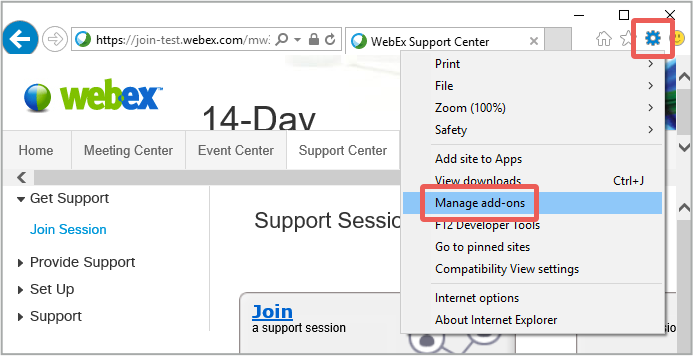
Select the Cisco WebEx LLC add-on and choose Disable to turn it off:
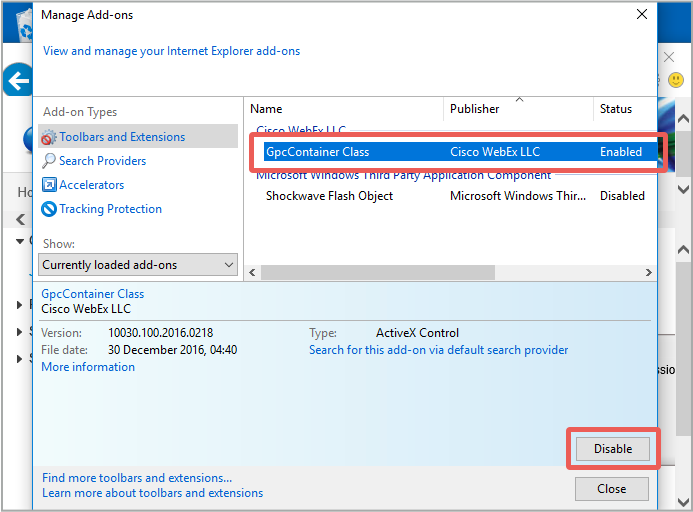
In Chrome, click on the vertical three dots in the top right corner and choose the Settings option:
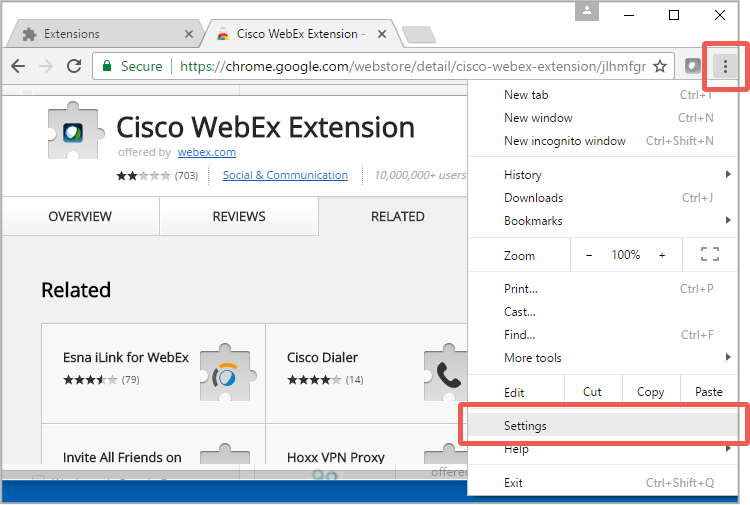
Go to the Extensions pane and untick the Enabled box to turn off the Cisco WebEx extension:
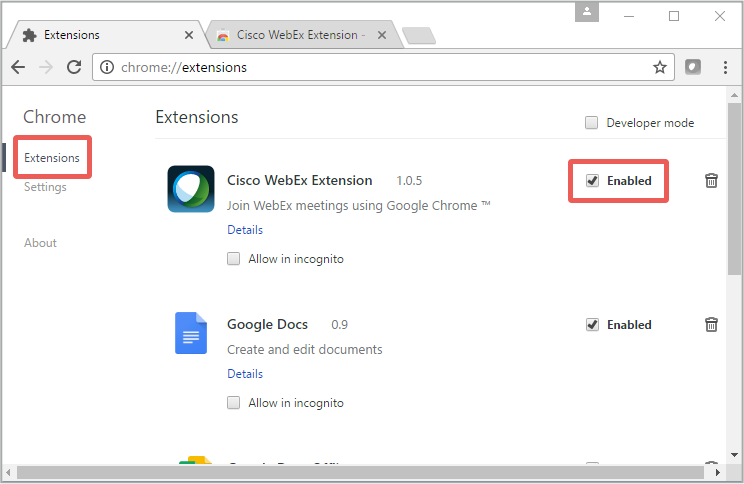
Q. Can I block the magic string in my web filter?
A. Many web filtering products, such as the Sophos UTM, can be configured to block access to any URL that includes the magic string that activates the WebEx extension:
cwcsf-nativemsg-iframe-43c85c0d-d633-af5e-c056-32dc7efc570b.html
This will provide an additional layer of protection on top of disabling the buggy extension in your browser, until a full patch is available from Cisco.
(If you rely on WebEx in your business, remember that blocking the magic string in your web filter for all users will also stop Mac, Linux and Edge browsers from connecting to WebEx, which may not be what you want.)
Q. How will I know when Cisco delivers a usable fix?
A. Keep your eye on Cisco’s cisco-sa-20170124-webex advisory page.

Dominique
Hi Paul
Thanks for the article. Two questions:
a) in relation to your suggestion “Many web filtering products […] can be configured to block access to any URL that includes the magic string that activates the WebEx extension”: will that work on sites that use SSL? I assume not, as using SSL restricts the web proxy’s visibility to the domain, and all page URLs are within the encrypted flow. Is this correct?
b) Can AV agents (Sophos Endpoint Security and Control or others) block attempted exploitations?
Regards,
Dom
Paul Ducklin
Errrr, yes, that’s a good point for URL blocking in general. When TLS/SSL is used you have to decrypt the traffic to see the URL because it’s inside the HTTP request, all of which is encrypted when it’s HTTPS. So for HTTPS traffic you need to have your product’s “scan content inside HTTPS” option turned on even for URL filtering, because the URL is part of the content.
As for whether Sophos endpoint exploit-blocking products can spot possible exploitation… the problem here is that this bug is more of an accidental backdoor (like a secret password in a router), so there isn’t really an exploit. Having said that, our products can and will block whatever an attacker does with this pseudo-backdoor, such as trying to implant and launch malware.
Paul O
Hi there,
I don’t have the WebEx Plugin installed so I can’t test this. But can you give any indication as to whether people can actually use the WebEx service without installing the Plugin/extension?
Paul Ducklin
I’m not a WebEx user, so I am not sure, but WebEx’s own documentation says that on Windows you need “Active X enabled and unblocked for Microsoft Internet Explorer (recommended)”; on Macs you need “plug-ins enabled in Safari [and] Java 6.0 or later”; and on Linux you need “Java 1.6 or later.”
https://www.webex.co.uk/support/support-system-requirements.html
The mention of “Java” implies that WebEx requires programmatic support from outside your browser – but it’s not clear if “recommended” instead of “required” on Windows mean that you can join meetings from Internet Explorer without any special browser extension loaded (albeit with limited functionality). I’d have thought that Cisco would have mentioned the option of “extensionless support for WebEx” as an official workaround if it were possible.
Any WebEx users able to enlighten us? I am guessing that if even you can join meetings without a plugin of any sort you’ll need one to *host* a maeeting, but that’s a guess.
Dominique
Not that I am a specialist, but the WebEx service does offer the option to run a temporary app rather than install/deploy an extension (we’ve tested this on IE & Chrome – the message is different depending on the browser used, but the option is definitely there). I assume the code used is (slightly?) different from that used by the extension, but even if the vulnerability is still present, at least it would restrict the exposure to the period of time during which WebEx is on (i.e. if the user browses in another browser window at the same time as the active WebEx session) as the application closes down after use.