Even though it’s a point release, Apple’s macOS Sierra 10.12.3 security update is a beefy 1.05Gbyte download.
(The term point release is a commonly used jargon word that refers to the sort of update that causes the smallest change to a product’s version identifier, and thus presumably the least amount of visual and functional change. Point releases are usually denoted by adding one to the rightmost number in the version string, as in this case of macOS 10.12.2 bumping up to 10.12.3.)
Nevertheless, we think it’s worth getting as soon as bandwidth allows, because the security holes that are fixed are well worth squashing.
As far as we can tell, none of the low-level vulnerabilities, notably the ones described with the ominous words “an application may be able to execute arbitrary code with kernel privileges”, have been seen in the wild.
Instead, they were found and reported responsibly, some by Google’s Project Zero bug-hunting team, and others by competitors in the PwnFest 2016 competition held in November in South Korea.
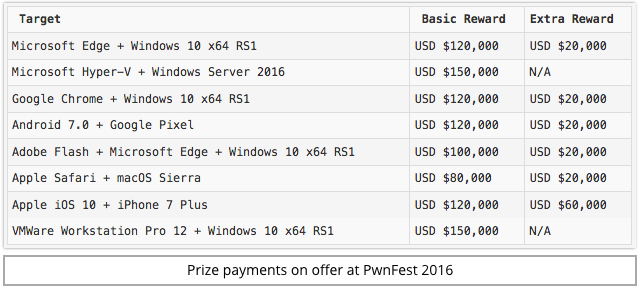
PwnFest is a sponsored competition for serious bug-hunters, with serious prizes offered for what is often a serious amount of work required to get past the defences that modern operating systems and applications have.
Just for the record, Microsoft Edge, VMWare, Adobe Flash and Google’s Pixel phone were also successfully hacked at PwnFest along with Safari on macOS. (In fact, Edge and VMWare were “owned” twice, resulting in two payouts.)
By the way, iOS gets an update to 10.2.1, fixing many of the same bugs fixed in the macOS flavour of Apple’s source code.
In addition, the iPhone update fixes two security problems that perennially face mobile devices: lockscreen bugs.
As we’ve written many times before, today’s lockscreens aren’t what they used to be, because users expect a selectable subset of their regular apps and functions to be accessible, at least in part, from the lockscreen.
In other words, lockscreens don’t so much lock your phone as try to corral it into a restricted mode of operation, often relying on individual apps to modify their behaviour to suit how they’re being accessed.
Unsurprisingly, as we’ve noted before in the case of so-called internet kiosks, which try to provide a regular Windows or Linux computer that’s locked into a walled garden for internet access, adding additional security-related complexity to an already complex app doesn’t always end well.
What to do?
If you have an iDevice, you can check for the update and optionally install it right away using Settings | General | Software Update.
On a Mac, the quick way is to click on the Apple menu at top left, choose About This Mac, and click the [Software Update...] button.
Remember that security updates that don’t contain any so-called zero days (the name used when the patch arrives after a new bug is being actively abused) are a great chance to get ahead of the crooks…
…and, for what it’s worth, we updated iOS and macOS as soon as we saw Apple’s security bulletins, without any apparent problems.
So far, anyway.

Mark
Fine article! Couple of nits:
“In other words, lockscreens don’t so much lock your phone was try to corral it” SB “as try”
and “locked into of walled garden” SB “into a”
Paul Ducklin
Fixed, thanks!