Thanks to Dorka Palotay of SophosLabs for her behind-the-scenes work on this article.
A new ransomware strain called Spora has taken the “freemium” model to a new level.
Many ransomware attacks include a try-before-you-buy feature on their pay pages, where you can decrypt one or two files for free as an inducement to trust the crooks.
By allowing you to upload two randomly chosen files and then returning copies of the originals, the crooks are hoping to prove that they do, indeed, have the decryption key they’re offering to sell back to you.
Assuming that the crooks didn’t simply upload all your data – unlikely, given that the upload speed of a typical ADSL home network is just 1 Mbps – and given that they didn’t know which files you’d choose, it’s reasonable to infer that they must have the necessary decryption key or keys for any and all of your files.
Spora adds three new levels to this whole try-before-you-buy angle:
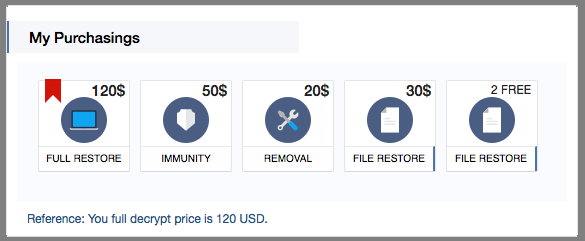
If the crooks are to be believed, you can:
- Decrypt two files for free.
- Decrypt a selection of files for $30.
- Have the ransomware itself removed for $20.
- Buy what they call immunity for $50.
- Get a full restore for $120.
We can’t give you exact details of what you get at each price point, because we haven’t tried paying up to see what happens, and we’re not inclined to do so.
Nevertheless, we’re hoping that there’s a vague silver lining here.
We suspect, or at least we would like to think, that the new immunity and removal options exist because more and more people are backing up their data properly these days.
In other words, the crooks have had to come up with additional payment options that might be of interest even to victims who can recover their data without paying for a decryption key.
How Spora gets in
Spora is clearly intended to be distributed by email, even though we haven’t seen any samples in our own spamtraps.
The ransomware is delivered in a multi-stage attack that unfolds as follows:
- There’s a ZIP file to look inside.
Opening up ZIPs, even if they arrived in an email, is generally regarded as a low-risk exercise, in the same way that looking at a list of files in a folder is much less dangerous than actually opening individual files inside the folder.
- The ZIP contains an HTA file with an enticing name.
HTA is short for HTML Application, meaning that Windows treats an HTA file like a web page that isn’t subject to the sandboxing and other security controls imposed when you are browsing.
If an HTA contains an embedded script, that script gets the same sort of run-time power as a downloaded program (.EXE file).
- The HTA file contains a VBScript program that creates and runs an embedded JavaScript file called
close.js.
Malware components that serve simply to construct and launch the next stage of the attack are known in the jargon as droppers.
Most malware delivery these days is done by a related sort of component referred to as a downloader, which fetches the next stage from the internet instead of carrying it around as a lump of embedded data, but the end result is the same.
Droppers have the disadvantage (to the crooks, anyway) that the content of what they deliver can’t be altered at run-time, as it can with a downloader.
On the other hand, droppers have the advantage that they don’t need an internet connection, so they work even when their victims are offline, and they don’t attract the attention of web filters, either.
- The
close.jsfile creates and runs a randomly-named program that contains the Spora ransomware.
Why so many stages?
If you’re wondering why the crooks didn’t just send the malware executable in the original email and avoid all the extra footwork, the reason is almost certainly down to subterfuge:
- Most users learned years ago not to open EXE files attached to emails, and few organisations let EXEs through their email gateway, anyway. Programs attached to emails are so rarely genuine that it’s an effective precaution to block them all unconditionally.
- ZIPs containing EXEs are similarly considered suspicious, even if a number of innocent-looking decoy files are added to the ZIP so that the EXE seems to have trustworthy company.
- JavaScript files in ZIPs are commonly used by ransomware crooks, so an increasing number of users are learning to be suspicious of them. JavaScript files show up with an icon looking like a scroll of text, but the message is sinking in that the icon represents a script (for which, read “untrusted program”), rather than a document.
- HTA files don’t yet flag up quite the same concerns amongst users as .JS or .VBS script files. However, HTA files, like HTML files, can contain embedded JavaScript or VBScript programs and ought therefore to be considered as dangerous as both those types.
Of course, splitting an attack into a number of stages in this way might help the crooks make each stage look more innocent to the intended victims…
…but it does mean that they give security software more chances of heading off the attack along the way.
All the steps in the attack have to succeed in sequence for the crooks to win; in contrast, if you can block any one of those steps, the crooks lose.
Sophos products block this attack as follows: Troj/HTADrp-I (ZIP and HTA files); JS/Drop-KI (JS file); Troj/Ransom-ECL (EXE file). Even if the EXE file were to run, Sophos Intercept X would block the malware and recover your files automatically, reporting the attack generically as Ransomware.
What happens next?
If Spora runs, it carries out an all-too-familiar ransomware attack that scrambles all files with the following extensions:
.1cd .7z .accdb .backup .cd .cdr .dbf .doc .docx .dwg .jpeg .jpg .mdb .odt .pdf .psd .rar .rtf .sqlite .tiff .xls .xlsx .zip
Spora works entirely offline – unlike a lot of other ransomware, it doesn’t call home to a server run by the crooks to acquire or to report the encryption key to use in the attack.
Somewhat simplified, the encryption process goes like this:
- Spora generates a public-private RSA keypair that is unique to your computer.
- Spora then generates a random AES symmetric key for each file and encrypts the file.
- Spora encrypts each file’s AES key with the public key generated for your computer.
- Spora encrypts your unique public-private keypair with a public key stored in the ransomware file.
Asymmetric or public key encryption such as RSA uses its public key to lock data, after which only the corresponding private key can unlock it. Asymmetric encryption is very slow so it is usually used only to secure small amounts of data, such as other encryption keys. Symmetric encryption such as AES uses the same key to lock and unlock data. It is much faster than public key encryption and is used for most bulk cryptographic tasks such as file and full-disk encryption.
Neither the AES keys used to encrypt your files nor the private key needed to decrypt those AES keys are stored in unencrypted form, so you can’t simply undelete them after the ransomware has finished.
Spora also deletes your Windows shadow copies (online backups) so you can’t easily roll back and recover your files that way.
Additionally, Spora breaks the shortcuts in your Start menu, to make it harder to open the Control Panel or to run a command prompt, as well as preventing you from rebooting into reovery mode, in order to frustrate any invesitgation you might want to do into what just happened.
To recover your files, you need the AES key for each file; to recover the AES keys you need the private key that is unique to your computer; and to recover your own private key you need the global private key that matches the global public key stored in the ransomware program file.
(Don’t feel bad if you need to read the above paragraph more than once.)
Of course, only the crooks have that global private key, so once your files and keys are scrambled, the crooks have the keys to your castle, literally and figuratively.
Paying up
Spora creates two files on your desktop; an HTML file that explains how to pay, and a KEY file that contains the encrypted copy of the private key you need to unlock your computer:
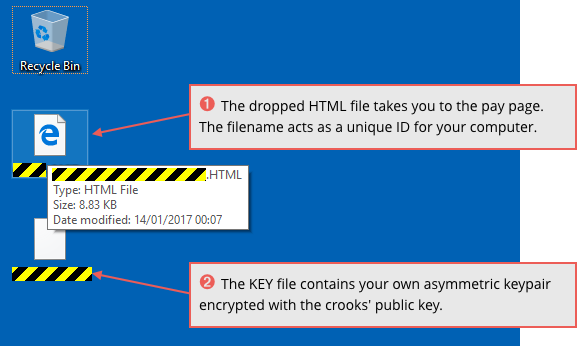
The ransomware loads the HTML file:
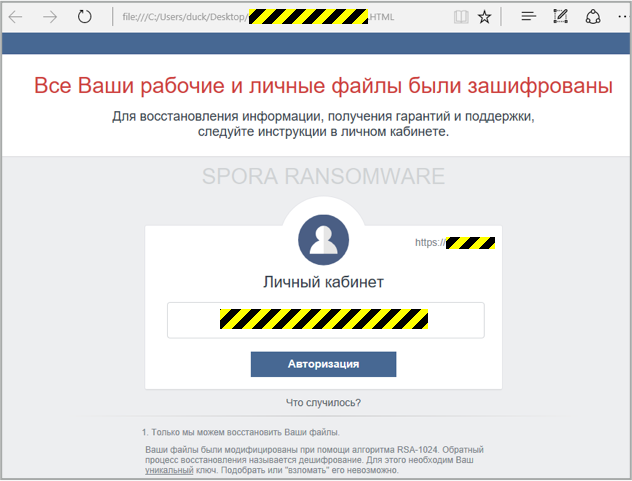
This local web page takes you in turn to a special portal page operated by the crooks.
This web server interacts in the background with a hidden service on the Dark Web, the identity of which is never revealed, and allows you to upload your KEY file to begin the payment process:
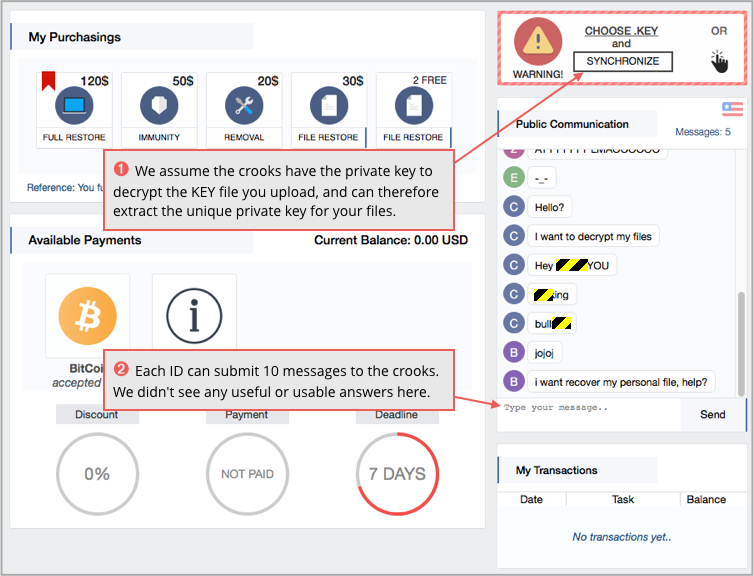
We haven’t tried paying up, so we can’t tell you exactly how the curiously-named immunity option works; we assume it is some sort of protection racket that means the crooks won’t take money from you if you get infected again.
Because Spora doesn’t call home before it attacks your files, it’s tricky for the crooks to figure out who you are before they encrypt your data.
So we can only guess that this sort of “immunity” doesn’t actually stop you getting infected and affected in the first place, but is effectively offering you a pre-paid decryption key for next time, if that should ever happen.
What to do?
As always, the best defence is not to get infected in the first place, so we’ve published a guide entitled How to stay protected against ransomware that we think you’ll find useful:
You might also enjoy our Techknow podcast Dealing with Ransomware:
LISTEN NOW
(Audio player above not working? Listen on Soundcloud or access via iTunes.)

Jim
Excellent (and very thorough) writeup on this one.
We can only hope that the number of people with backups has been increasing. If so, then ransomware (in general) has at least one positive aspect to it.