Nymaim, a malware family connected to several online ransom campaigns in recent years, is retrieving network card MAC addresses and using them to uncover virtual environments, thwarting automated antivirus analysis tools in the process.
Virtualized environments are widely used in large organizations trying to simplify IT by only giving users a thin client, according to SophosLabs researcher Sandor Nemes. It’s also where antivirus researchers deploy the sandboxes they use for automated malware analysis. By going around virtualized environments, Nymaim loses potential targets. But it escapes the automated antivirus sandboxes, which can buy an attacker precious time, Nemes said.
“Malware that deliberately avoids showing its real behavior on an automated malware analysis system is frustrating,” he said. “If they can successfully avoid a virtualized sandbox, someone has to analyze the sample manually, and the malware authors can win some time.”
Nymaim is a downloader Trojan that emerged in 2013. It originally delivered file-encrypting ransomware as its final payload. It recently resurfaced, and is still used as a delivery platform for different malware families. One strain combines the code from Nymaim with Gozi, a banking malware, resulting in a new malware family called GozNym.
SophosLabs spotted Nymaim’s sandbox-avoidance tricks while investigating a large spam campaign targeting mostly German-speaking users. Researchers found that a Nymaim sample they were studying didn’t properly execute in the lab’s VirtualBox-based replication environment. They dug in further to figure out why.
“The first we found was that each of the samples has a hardcoded expiration date, after which it refuses to properly run,” Nemes said. “After changing the date on the analysis machine, the sample ran further than before, displaying a message box with the text ‘Can not view a PDF in a web browser’. Then it loaded a DirectDraw graphics library, and tried to unsuccessfully load a non-existing DLL, then quit, but later it turned out that this is part of the malware’s misdirection tactics.”
Nymaim’s checklist
Deeper analysis showed that when Nymaim does a check and fails, it keeps running for a while to make its failure less obvious. The list of identified Nymaim checks are below:
- Checks the current date against the hardcoded expiration date.
- Checks the hash of the username against a list of blacklisted username hashes.
- Checks the hash of the sample filename against a list of blacklisted filename hashes.
- Computes a hash value for every environment variable set. If the resulting value matches a hardcoded one, then it skips the rest of the checks. This was probably intended as a feature to allow easy debugging from the malware author’s side.
- Checks the MAC address of the computer against a list of blacklisted vendors.
- Computes a hash value for every filename in the C:\Windows directory to see if any of them matches the list of blacklisted filename hashes.
- Checks the hash of the computer against a blacklist of hashes.
- Queries the system BIOS version and video BIOS version from Windows registry and checks if it contains “VBOX” or “VirtualBox.”
Uses custom hash algorithms
Nemes said Nymaim uses hashes with a custom hash algorithm instead of the actual strings, which is a clever tactic because:
- It takes less space and the hash is less visible in the file than a string would be, and
- A researcher won’t know what it looks for exactly, unless they start brute-forcing the hash values.
“I started a brute-force crack against the hash values, and found that the username and the computer name are checked against the text ‘sandbox’,” Nemes said. “The text is converted to lowercase before calculating the hash, so case does not matter. That was the only hash I could recover, so the strings corresponding to the rest of the hash values are still unknown.”
Then came the most interesting discovery: Nymaim’s retrieval of the MAC address from the network card.
Identifying virtual environments, then moving on
Nymaim makes a call to UuidCreateSequential, which generates a universally unique identifier (UUID) using the current time and the MAC address of the network card (these two values represent a single point in space and time, so should be unique).
This way, Nemes said, the malware author can extract the MAC address using a seemingly innocuous API call and doesn’t have to fiddle around with networking stuff, and can avoid handling the corner cases when there is no network card in the computer, or there are multiple network cards.
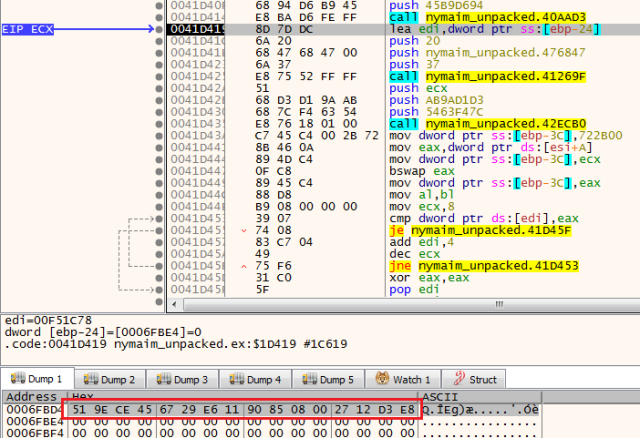
The first three bytes of the MAC address is known as the OUI (organizationally unique identifier), which uniquely identifies the vendor of the network card. The malware checks this against the following list (hardcoded into the malware) to find out if it is running on a virtualized infrastructure:
– F0:1F:AF Dell Inc.
– 00:50:56 VMware, Inc.
– 00:0C:29 VMware, Inc.
– 00:05:69 VMware, Inc.
– 08:00:27 PCS Systemtechnik GmbH (VirtualBox)
– 00:03:FF Microsoft Corporation
– 00:1C:42 Parallels, Inc.
– 00:16:3E Xensource, Inc.
Spotting suspicious file extensions
Executables come with a .com extension, an old executable file format that dates back to the MS-DOS era. The malware is a regular Windows executable and has nothing to do with the archaic MS-DOS COM format, but Nymaim’s masters use the .com extension hoping they’ll evade AVs that rely on the file extension to determine the file.
For historical, backwards-compatibility reasons, Nemes said Windows runs the .com file when the user launches it, even if it’s a newer Windows executable and the file format does not conform to the old MS-DOS format.
“In my opinion, the best option for the user is to uncheck the Windows setting which hides the file extensions (Folder and search options > View > Hide extensions for known file types), this will make it much easier to spot files having suspicious file extensions,” he said.

Wilbur
Question – would it be possible to get around the MAC check by using MAC address spoofing software or would UuidCreateSequential report the actual VM MAC address so it would not be fooled?
Paul Ducklin
You can change the simulated MAC address in most VM software on a per-VM basis. More precisely, you can do so with VirtualBox, which I know well, and I assume you can do the same with other virtualisation tools.
In VBox you can use the GUI, e.g. Settings | Network | Adapter 1 | Advanced | MAC Address, or you can use the command line, e.g.
$ VBoxManage modifyvm [VMname] --macaddress1 xxxxxxxxxxxx
Above, xx...xx represents 12 characters in hex specifying the 6-byte MAC address you wish to use. Avoiding MAC collisions in your virtual network is your own responsibility :-)
researcher
md5 of the sample you analyzed?