Thanks to Fraser Howard and Dorka Palotay of SophosLabs for thir behind-the-scenes work on this article.
First it was Locky, then it morphed into Zepto, and now it’s become Odin.
That’s the latest reinvention of the Locky-turned-Zepto strain of ransomware.
If you’re unfortunate enough to get hit by this one, you’ll see its Locky heritage as soon as you reach the Dark Web “buy page” where the crooks tell you how to pay their extortion demand.
(Sophos products block this malware as Troj/Locky-NP, another reminder of its Locky roots.)
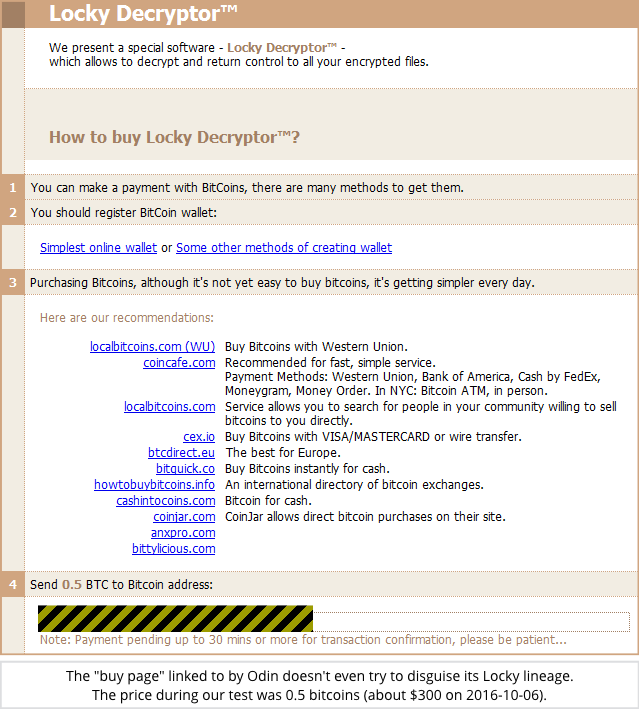
You don’t need to be able to understand English to get the message, because the crooks are offering localised “buy page” advice in many languages:
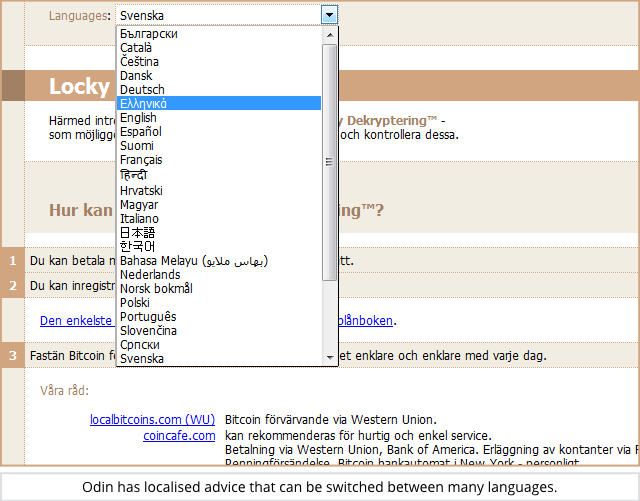
So far, we’ve only seen Odin pushed out by email, with a vaguely grammatical English text body telling you that your order has been processed, and a ZIP attachment that claims to contain the order itself:
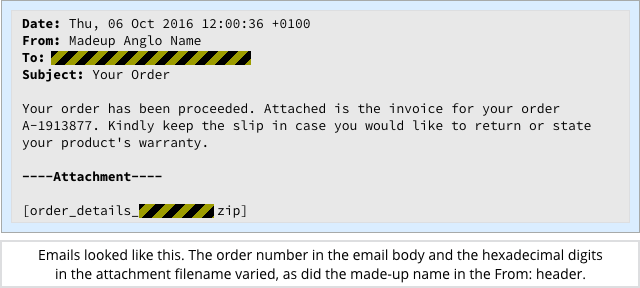
If you open the email, you’ll see two files, one of which claims to be a cancellation form.
The other item in the ZIP is a dummy file with a single-letter filename that contains a random byte repeated a few thousand times, presumably to make things look a little different from ransomware you may have seen before:
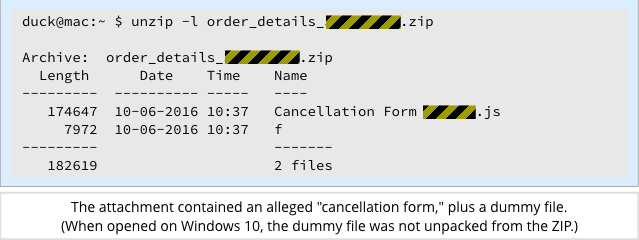
When we opened the ZIP on Windows 10, the dummy file did not show up, but a file looking very much like a text document called Cancellation Form did:
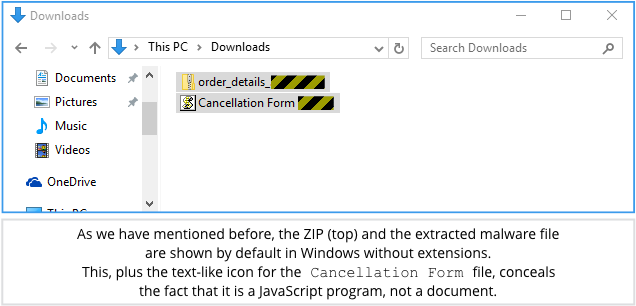
Just like many other recent malware samples, including Zepto, the cancellation form that the crooks want you to open is a JavaScript program.
When opened outside your browser, the Cancellation Form malware file isn’t limited by the browser’s sandbox, so it can download and launch the Odin ransomware program without popping up any warning dialogs.
As we’ve recommended regularly before, you can give yourself a better chance of spotting this sort of treachery by using File Explorer’s View | File name extensions option to reveal extensions that are otherwise suppressed:
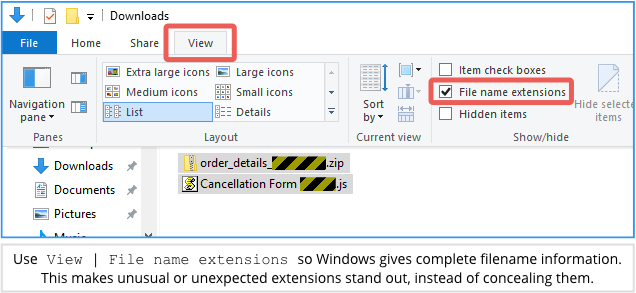
(If you’re on a company network, your sysadmins can turn on File name extensions for everyone using a Microsoft Group Policy setting.)
Opening the Cancellation Form runs the first stage of the Odin malware, which:
- Unscrambles its own JavaScript to produce a second obfuscated JavaScript program.
- Runs the second JavaScript stage to download a scrambled DLL (a special form of Windows program).
- Unscrambles the downloaded DLL.
- Loads and runs the DLL using the Windows utility
rundll32.exe.
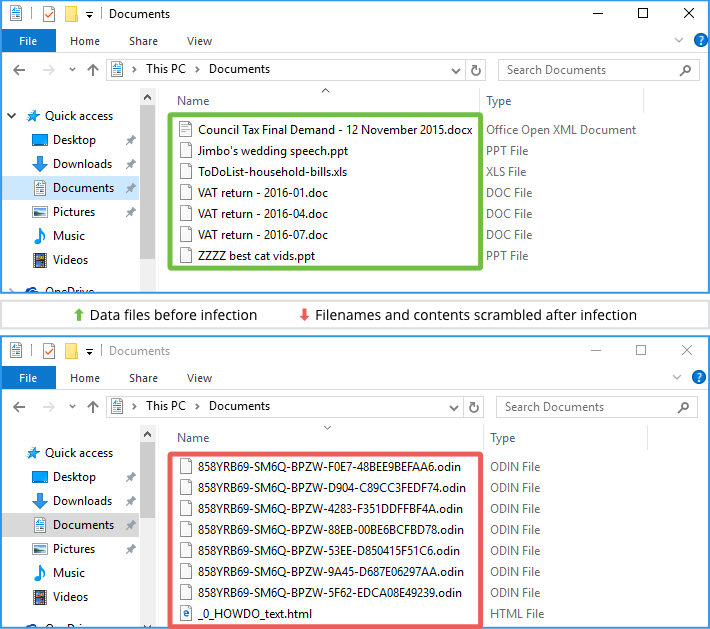
At this point, the ransomware component of Odin is active, and file encryption starts:
Just as with Zepto, each data file is encrypted using AES with a randomly chosen key, and each file’s AES key is encrypted with an RSA public key.
Remember that although AES is a symmetric algorithm, with the same key used to lock and unlock your data, the RSA algorithm uses two keys, one for locking (the public key), and the other for unlocking (the private key).
The reason for using a two-layer encryption system of this sort, with a symmetric cipher for the bulk shrouding of files, followed by asymmetric (public key) encryption for shrouding the symmetric keys, is performance. Public key cryptography is thousands of times slower than symmetric encryption.
Because the crooks have the only copy of the RSA private key, and because the AES key used for each file is only ever saved to disk after it has been locked with the corresponding RSA public key…
…then only the crooks can unlock the keys needed to unlock your files, and that’s why they feel confident to squeeze you for $300 to buy back access to your data:
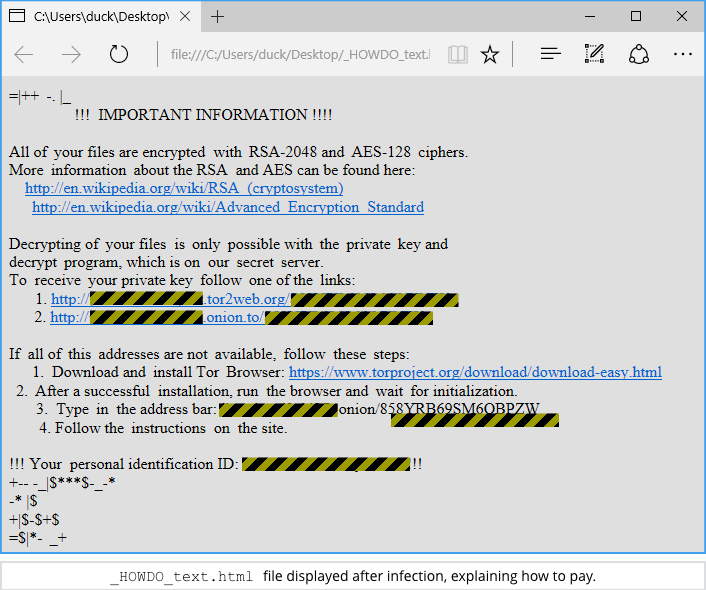
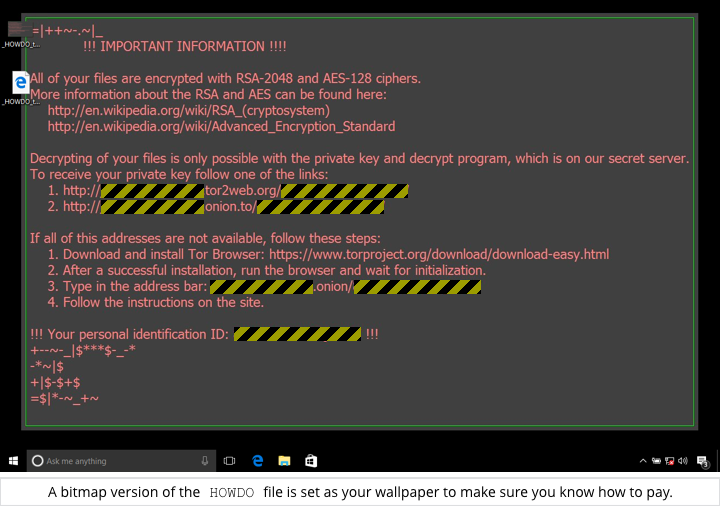
As has become common in ransomware attacks, the crooks not only open a file in your browser, but also change your wallpaper to an image that makes sure you know where to go to pay the extortion money:
What to do?
We regularly offer advice on preventing (and recovering from) attacks by ransomware and other nasties.
Here are some links we think you’ll find useful:
- To defend against ransomware in general, see our article How to stay protected against ransomware.
- To protect against JavaScript attachments, tell Explorer to open .JS files with Notepad.
- To protect against misleading filenames, tell Explorer to show file extensions.
- To learn more about ransomware, listen to our Techknow podcast.
- To protect your friends and family against ransomware, try our free Sophos Home for Windows and Mac.
LISTEN NOW
(Audio player above not working? Listen on Soundcloud or access via iTunes.)


Patrick Palmer
Any solution to this yet??
Paul Ducklin
Yes, we blocked the emails proactively in our email filtering products, and blocked the malware itself before execution. (As an aside, if it were to get through, our new product Intercept X would block the actual data scrambling part with its CryptoGuard component.)
Incidentally, if your company doesn’t use JavaScript outside the browser, then you don’t need to allow .JS files to run directly under Windows at all, which is something the Sophos Endpoint product can manage with what we call App Control. That’s where you optionally decide to block certain legitimate programs along with malware, on the grounds that it reduces your attack/breach/problem-causing surface area. The Windows Script Host (WSH), which is what launches JavaScript programs outside the browser, is on the controllable list.
(You can do the app blocking in groups, which is handy if you want to give your sysadmins selective access to certain so-called “hacking tools,” such as port scanners or packet sniffers, that you’d prefer not to have everyone messing around with “because they can.”)
Er, that’s the end of the commercial :-)
AdamD
Friend of mine who runs a small business got hit with this, it encrypted all their excel spreadsheets, do you think someone will bring out a decryptor?
She may have to close her business at this rate, as she only has a 2+ month old backup of her data.
Real pain in the rear.
Paul Ducklin
I am not aware of any cryptographic bugs in this variant that would allow you to decrypt for free.
If time is of the essence, and your friend has no other way out, she may be stuck with paying the crooks. It hurts to do so; it might not work; and we recommend that you don’t do it…
…but that’s easy for us to say, because it’s not our data on the line.
There’s a big drive in some quarters to say, “NEVER PAY UP,” as though you’re a crook yourself if you do, but we’re not that hard-hearted.
Sorry that I don’t have anything more useful to tell you :-(
AdamD
Quick one for you Paul, in my friends case, it was the client PC which downloaded the ransomware via email, which then encrypted the data on a network share (server)
Assuming that the virus wasn’t run on the server itself, wouldn’t the shadow copy service be able to restore files from the folder they were deleted from?
And/or wouldn’t a recovery program like Recuva or something similiar be able to retrieve the files from the deleted share/drive on the server itself?
Paul Ducklin
If you still have shadow copy files on the server, you ought to be able to recover those.
RichardD
“the mythological man”
That’s an odd way to refer to a Norse god! :)
Lucy Millington
Ditto! I’ll argue with Duck and Anna to get that updated
Paul Ducklin
I removed that bit, as I’m not actually sure that the malware was named after Odin after all.
Someone
You can protect against this (and most rogue javascript malware) by changing your system’s javascript file associations to open javascript in your favorite text editor instead of allowing it to auto-run.
Paul Ducklin
Errrr, this is covered in the article…and there’s a link to another article that shows you how to do it :-)
(See list of tips under “What to do?”)
Yasser
what is the method of spreading in the network once get in connected machine ?
Paul Ducklin
It’s not a virus in the true sense, i.e. it doesn’t spread by itself. Each infection is delivered individually, though using spamming techniques, the crooks can deliver 1000s or even 1,000,000s of infected attachments at a time.
Jeny Liza
nice
Thijs
Our company got hit last week by the odin variant, at first we didn’t even realized we got hit that bad.
It seems to have “seeded” from 1 pc to our file server (this got flagged by the antivirus), a couple of other pc’s (wasn’t flagged by the antivirus and had a devastating effect ) and ( this was a first to me ) to our NAS server ( that’s working on ubuntu and was the IT back up). So the 1 original file, contained enough information to do damage to windows and linux.
moundir
Thijs, did you recover your files?
Pedro
In my personal case, I did a restoration from shadow copy but didn’t work due was modified too for Odin, someone know if Odin too delete original files? if the answer is yes, my last option is try to recover with a getdataback or some utility that can recover from deleted items
Thanks in advanced
Fernandes
Hello admin,
I need help, all of my data had been corrupted with odin, do you have any idea to recover my files?
Thank you before